Buy our over-priced crap to help keep things running.




















| Files | ||||
| File Name | Rating | Downloads | ||
| ACleaner v4.5 ACleaner v4.5 ACleaner is a safe and easy-to-use privacy protection tool, that allows you to erase common Internet and computing tracks, including browser cache, cookies, visited websites, typed URLs, recent documents, index.dat files and more. You can also easily erase the tracks of up to 100 popular applications. It also includes an option to overwrite deleted data multiple times, so it cannot be easily recovered. The cookie cleaning feature allows you to specify which cookies to keep, so that you don't erase your important login cookies. You also can schedule automatic erasing for any time you like and use boss key to hide all browser windows in one quick keystroke! In addition, the program comes with a registry scanner to optimize your system registry by finding and removing errors and invalid entries. After fixing the invalid entries, your system will be more stable and run faster. For maximum safety, ACleaner will make a backup of the repaired entries. You will be able to restore any changes made using the software by choosing Restore registry backup. Why do you need ACleaner? • Your Internet activities can be traced through cache, cookies, and history. • Windows and third party software stores information that could compromise your privacy. • The Windows Registry is a crucial part of your PC's operation system. Problems with the Windows Registry are a common cause of Windows crashes and error messages. Key Features: Remove the tracks of your activities completely 1.Windows Item Remove Windows recent documents history Remove Start Menu -- Run/Find history Remove the files in Window recycle bin Remove Windows temporary files directory Remove clipboard Remove memory dumps Remove chkdsk file fragments Remove Windows log files Remove menu order cache Remove open/save dialog history Remove tray notifications cache Remove user assist history Remove Media Player/Real Player history Remove Paint history Remove Microsoft Office ... |
 |
5,557 | Mar 20, 2019 Cleanersoft Software 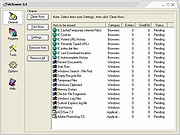 |
|
| Alternate File Shredder v2.550 Alternate File Shredder v2.550 This program offers the possibility to finally delete files and/or folders (no recovery possible). The program also can overwrite the free space on a drive, which means, that already deleted files cannot be restored, too. The program offers also options to select how the overwriting shall be done (using a specific value, random values or a file-content as template). The program is freeware/open source, it requires the .NET-framework 2.0 (already included in operation system since Windows Vista). IMPORTANT NOTE: You are using this program at your own risk. Think carefully which files you want to delete! Changes in this version: - Internal corrections MD5 value: 3cf185a4c5bfcd627a0e35f7396c57cf Supported operating systems: Windows 98, Me, 2000, XP, Server 2003, Vista, Server 2008, 7, 8, 8.1, 10 Languages included: English, German, Spanish, French, Italian, Chinese, Japanese, Korean, Swedish, Arabic, Greek, Russian, Czech, Hungarian, Turkish, Polish, Portuguese Click here to visit the author's website. |
 |
6,551 | Apr 29, 2020 Alternate Tools 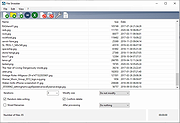 |
|
| AskAdmin v2.0 AskAdmin v2.0 Free tool designed to restrict an Application a Folder or a File. Ideal for those who have small children or for a computer used in business. Do you wish to restrict some users from accessing certain programs, services, and files on a computer? With AskAdmin, you can simply block access to chosen applications, files, and folder contents. AskAdmin can block most any resource on your computer, including Microsoft Store, Microsoft EDGE, Google Chrome, Skype, built-in apps (e.g. UWP), CMD and BAT files/scripts, reg data and more. To further prevent access to blocked items, AskAdmin provides an optional password. How to use it There are two ways to create a block list: 1. The easiest way is to drag and drop Application/s, a Folder/s or a File/s you wish to block to the AskAdmin interface. If you wish, you can drag several applications on GUI at once. 2. Click the ‘Add File’ button (Plus icon) browse to the application you wish to block. How to block an Application a Folder or a File If an Application , Folder or File name is on the list , mean: it is Automatically blocked (Folder inhalt will be blocked not folder itself) , but on some cases you should use the “Restart” buton (Guarantee) , if you accidentally block any windows System file this can cause system crash therefore we have tried to prevent it, after that you can use the safe mode to unblock the file. How to unblock an application , a Folder or a File You can unblock a single application/Folder/File, or you can simultaneously unblock all of them. a) Untick an Application , a Folder or a File name. b) Delete the Application , Folder or File name (Edit > Delete or Right click > Delete). If the block does not seem to be work, you may need ... |
 |
4,726 | Apr 24, 2025 Sordum.org 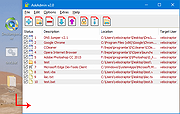 |
|
| AZdecrypt v1.19 AZdecrypt v1.19 A powerful multi-threaded letter n-gram based substitution cipher solver for Windows since 2014. Originally written in attempt to solve the Zodiac Killer's unsolved 340 code. Read how this team finally used it to solve the 340 Cipher. BREAKING NEWS: The Zodiac’s “340 Cipher” has been solved This download is for the standard version of the program and the source code. The following are CPU architecture native .exe's compiled with -march. These should run AZdecrypt a little bit faster if your CPU supports the instruction set and may crash if it does not. AZdecrypt 1.19 (64-bit) GCC 5.2.0.exe download here. AZdecrypt 1.19 (64-bit) Ivy Bridge.exe download here. AZdecrypt 1.19 (64-bit) Ryzen.exe download here. AZdecrypt 1.19 (64-bit) Skylake.exe download here. Click here to visit the author's website. |
 |
3,295 | Dec 12, 2020 Jarl Van Eycke 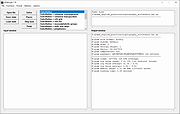 |
|
| BCTextEncoder 1.01 BCTextEncoder 1.01 Never worry that someone might read a confidential email, BCTextEncoder will easily encrypt part or all of your messages. Easily encrypt your messages using strong and approved symmetric and public key algorithms for data encryption. BCTextEncoderTM utility software simplifies encoding and decoding text data. Plain text data is compressed, encrypted and converted to text format, which can then be easily copied to the clipboard or saved as a text file. BCTextEncoder uses public key encryption methods as well as password-based encryption. |
 |
8,887 | Sep 06, 2016 Jetico Inc. |
|
| BlackBeltPrivacy Tor+WASTE 3.01.2014.01 BlackBeltPrivacy Tor+WASTE 3.01.2014.01 Tor helps keep you safe online.. WASTE enables secure content exchange. A usability enhanced Tor+WASTE+darkRendezvous(). An installer, for Windows XP 32/64, Vista 32/64, Win7 32/64, Linux (WINE). Features: 4 Modes, Censored Client, Bridge(default), Relay and Exit - chosen by you at install time. Be sure to check-out the screen shots. Friendly support provided. Streamlined Installation Package. No additional configuration necessary for server, client or darkNet() Auto Firefox config. Optional Tor Relaying, bandwidth restricted. From 0->100mb or 0->500mb per day - its your choice. Regularly updated includes auto-configured Obfsproxy, for censored-clients and bridge-operators Screen shots may differ due to our continuous development cycle. •NOTE: Linux/Unix/MacOSX Compatibility is obtained via WINE. (tested working) •NOTE: The core tor team no longer ship a proxy. We have adopted the same. |
 |
9,017 | Sep 06, 2016 darkNet() |
|
| Blank And Secure v8.15 Blank And Secure v8.15 A portable tool to securely delete data from Windows. Blank And Secure overwrites data in Windows with random numbers 1-32 times to securely delete files with no possibility of recovery. Usage Add the files or folders via drag and drop on "Blank And Secure" or program icon on the desktop. Then press "delete". The file(s) will be rewritten with NULL before deleting, so the content is now irreparable. Press the button "Fill the free space with null" this will remove the standard deletion tracks from the hard drive . Features • Secure delete and Shutdown the PC • Overwrite the Files 1-32 times with random numbers and delete. • Fill the free HD space with random numbers • Remove the standard deletion tracks from the hard drive • Multiple Renaming of the file to a random name before erase Other specifications • Very Small • Full Unicode Support • Low CPU and Memory Usage • Drag and Drop Support • Portable • Freeware • Multilingual Options • Reset: Clear the List Contents (not delete the files). • Delete: Overwrite folder and files with random numbers and delete. • Overwrite X times: Overwrite the data X times with random numbers. • Delete Delay X-sec.: At this time you can stop the erasing procedure with the key [ESC]. • Fill the free space with random numbers: This will remove the standard deletion tracks from the harddrive. Supported operating systems Windows 11, Windows 10, Windows 10 Pro, Windows 10 Enterprise, Windows 10 Home, Windows 8.1, Windows 8.1 Enterprise ... |
 |
6,272 | Jun 26, 2025 Nenad Hrg 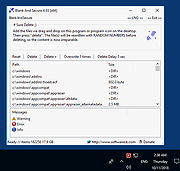 |
|
| BleachBit v5.0.0 BleachBit v5.0.0 Clean Your System and Free Disk Space When your computer is getting full, BleachBit quickly frees disk space. When your information is only your business, BleachBit guards your privacy. With BleachBit you can free cache, delete cookies, clear Internet history, shred temporary files, delete logs, and discard junk you didn't know was there. Designed for Linux and Windows systems, it wipes clean thousands of applications including Firefox, Internet Explorer, Adobe Flash, Google Chrome, Opera, Safari,and more. Beyond simply deleting files, BleachBit includes advanced features such as shredding files to prevent recovery, wiping free disk space to hide traces of files deleted by other applications, and vacuuming Firefox to make it faster. Better than free, BleachBit is open source. Features • Shred sensitive files, so one can ever read their contents. • You always have the "Pro" version: BleachBit is free of charge • Anonymous: you do not need to register an account • Simple to operate: read the descriptions, check the boxes you want, click preview, and click delete. • Multi-platform: it runs on both Linux and Windows • What's hiding in your software? BleachBit is free to share, learn, and modify because it is open source, so there are no secrets. • No adware, spyware, telemetry, malware, bloatware, backdoors, browser toolbars, or "value-added software" • Translated to 68 languages • Overwrite free disk space to hide previously deleted files • On Windows, choose to either install or run in portable mode. like from a USB drive. • Command line interface for scripting and automation • Advanced users can write their own cleaners using CleanerML • Automatically import and update winapp2.ini cleaner files giving Windows users access to thousands of additional cleaners Uses • Free disk space • Reduce the size of backups and ... |
 |
6,354 | May 07, 2025 Andrew Ziem  |
|
| BMP Wrap 2.0 BMP Wrap 2.0 Ever needed to email a file but it keeps on bouncing because it's an illegal attachment? Renaming the file or storing it in a ZIP archive sometimes works, but many ISP can detect that low-tech obfuscation. You need BMP Wrap. BMP Wrap temporarily hides a file inside a valid .BMP image. Once hidden, you can send the BMP file to anybody you wish and they can then extract that file from the BMP image using BMP Wrap. Now you can send EXEs, DLLs, or whatever file format you want, and the destination mail server will never be the wiser. No installation is required - just save the EXE file to your desktop, and then drag the file you want to wrap/unwrap onto the the BMPWrap Icon (a new .BMP file is created, the original file is left unmodified). This program is free & does not include any ad-ware or other malware. |
 |
5,260 | Jan 27, 2017 HCI Design  |
|
| CipherShed v0.7.4.0 CipherShed v0.7.4.0 CipherShed is free (as in free-of-charge and free-speech) encryption software for keeping your data secure and private. It started as a fork of the now-discontinued TrueCrypt Project. Learn more about how CipherShed works and the project behind it. The CipherShed project is open-source, meaning the program source code is available for anyone to view. We encourage everyone to examine and audit our code, as well as encourage new ideas and improvements. Click here to visit the author's website. |
 |
4,485 | Jun 25, 2019 The CipherShed Project  |
|
| ClearClipboard v1.07-1 ClearClipboard v1.07-1 ClearClipboard is a simple tool that will periodically clear your clipboard. This is useful, for example, to hide sensitive information, such as passwords. The clear timeout can be configured freely and defaults to 30 seconds. Also, the clipboard will not simply be cleared at a fixed interval. Instead, the clear timer will be reset every time that new content is copied to the clipboard. This ensures that only "stale" content will be cleared; recently copied content will never be cleared away. Note: The ClearClipboard program runs "hidden" in the background. However, there will be an icon in the notification area, which can be used to control or terminate ClearClipboard. Only one instance of ClearClipboard can be running at a time. System requirements ClearClipboard runs on Windows Vista or newer. The "x64" version requires a 64-Bit version of Windows Vista or newer. Windows XP is not supported due to the lack of the AddClipboardFormatListener system function! Windows 10 Warning Windows 10 contains some "problematic" features that can put a risk on sensitive information copied to the clipboard: The first of those features is called Clipboard History, which will silently keep a history (copy) of all data that has been copied to clipboard at some time. This history will persist even after the clipboard has been cleared! The second feature is called Automatic Syncing (Cloud Clipboard), which will automatically upload all data that is copied to clipboard to the Microsoft cloud servers – purportedly to synchronize the clipboard between your devices! We highly recommend to disable both of these features in order to keep your data safe and allow ClearClipboard to function as expected. To the best of our knowledge, the most reliable way to achieve this is to completely disabled the "Clipboard History" (cbdhsvc) system service. ClearClipboard will now detect ... |
 |
4,336 | Apr 11, 2021 LoRd_MuldeR  |
|
| CrococryptFile 1.6 CrococryptFile 1.6 CrococryptFile is a file encryption tool which creates encrypted archives of arbitrary files and folders. The encryption features of CrococryptFile can be compared to a ZIP utility that uses ZIP's AES encryption. However, there are significant differences. CrococryptFile... - encrypts all file and folder information including filenames, time/date and filesize information, - disguises any information of the archive's content, because all data and meta-data is simply integrated into a giant file dump. =Crypto Suites= For a full list of and details about supported crypto suites, please visit the CrococryptFile Homepage. Examples: - Password-based encryption (following PBKDF2) with AES-256, Twofish, Serpent, ... - Public key encryption using GPG/OpenPGP, Windows Keystore/CAPI with RSA/X.509 certificates - Cloaked (headerless) Password-based Encryption (AES-Twofish-256) Features file encryption encryption aes twofish pbkdf2 cloak pgp Version History 1.6 (05/13/2017): New: Support for Russian added (Special thanks to Aleksey Cheremnykh |
 |
5,350 | Apr 02, 2018 Frank Hissen  |
|
| Crypt It v1.4.3.0 Crypt It v1.4.3.0 Crypt it is a portable software to encrypt and decrypt files and texts. It uses AES official code to encrypt and decrypt files and Rijndael algorithm to encrypt and decrypt strings. Change Log: Version 1.4.3.0 [9/2/2019] GUI changes New: Encrypted files can be saved in their own folders by selecting “Save to original folder” option. Output folder section will be disabled when “Save to original folder” option is enabled. New: Crypt it main form is now resizable and also files list rows and columns can be resized too. Crypt it background is now white and not gray Internal fixes CRC32: 5E0BCEE9 MD5: 494309AA1658230843B4534473709993 SHA-1: BBE545C603B08EA90A2514CA48122CAF42B9D2E8 SHA-256: EB18E25668E6DDA5DA5D9C1CDFF2FF012B53F133DBE098A1726736C68CEE36D3 Requirements: .NET 4.6 minimum Click here to visit the author's website. |
 |
4,285 | Jul 15, 2019 Sami Jildeh  |
|
| Crypter Geek 2.0 Crypter Geek 2.0 Encrypt / Decrypt text files by this mysterious encryption tool, No installation required. Warning: Windows Defender and other anti-malware programs may incorrectly detect this as malicious. It is a clean file. |
 |
6,209 | Feb 25, 2017 Christos Beretas  |
|
| Crypto Notepad v1.6.6 Crypto Notepad v1.6.6 Notepad-like simple text editor for Windows, where files are saved and loaded encrypted with AES algorithms. Features Drag and Drop support Detect URLs and email links Fully customizable editor. Able to customize the colors and fonts Able to customize different parameters of the encryption (hash algorithm, key size, password iterations) Included all the features of the default Windows Notepad Association with the application extension Easily search through the content System requirements Windows Vista SP2 and higher .NET Framework 4.5 License Distributed under MIT license Read this before updating from v1.5.1 (and from earlier versions) After auto-update delete Ionic.Zip.dll file from the app folder v1.6.6 (2020-01-20) Added Auto lock if the app is inactive #48 Able to make editor readonly. Readonly indicator in the status panel. Word wrap indicator in the status panel. Auto-clear clipboard on app close. Auto-clear clipboard after copy text from the editor. Able to clear clipboard manually from the Edit main menu. Able to disable all shortcut keys. Improved Remapped some shortcut keys #49 When app is minimized, editor text is hidden in windows thumbnail previews (how it looks). Categories in Settings window was reorganized. Now all main menu items have hotkeys. Fixed Shortcut keys doesn't work or worked when it's not necessary. File hash CRC32: 80B37B3F MD5: E8AE90B3DEE96D4EAB71C906E40E73AA SHA-1: A4EFB2D4D8B138C9A5A561BCBEE91AF7A992AF41 Click here to visit the author's website. |
 |
4,717 | Jan 20, 2020 Sigmanor  |
|
| Cryptomator v1.17.0 Cryptomator v1.17.0 A simple tool for digital self-defense. It allows you to protect your cloud data by yourself and independently. Most cloud providers encrypt data only during transmission or they keep the keys for decryption for themselves. These keys can be stolen, copied, or misused. Thanks to Cryptomator, only you have the key to your data in your hand. Cryptomator allows you to access your files from all your devices. It's easy to use and integrates seamlessly between your data and the cloud. How does Cryptomator protect your data? Cryptomator's technology meets the latest standards and encrypts both files and filenames with AES and 256 bit key length. To start with Cryptomator, you assign a password for a folder - we call it a vault - within your cloud. That is all. No complicated key creation, no registration, no configuration! To access the vault, simply enter the password again. You will be provided with a virtual encrypted drive to which you can move your data - just like a USB flash drive. Every time you store something on this drive, Cryptomator encrypts the data automatically. Pretty simple, right? The technology behind this is state-of-the-art and encrypts both files and filenames with AES and 256 bit key length. This means: if someone looks into the folder in your cloud, they cannot draw any conclusions about your data. Optimal protection thanks to the latest technology standards If someone looks into the folder in your cloud, they cannot draw any conclusions about your data. Why is Cryptomator secure and trustworthy? No backdoors, no expiration date thanks to open source You don't have to trust Cryptomator blindly, because it is open source software. For you as a user, this means that everyone can see the code. Audited by security researchers In addition to independent security audits, the software is continuously and publicly tested in an automated way and ... |
 |
5,075 | Jun 26, 2025 Skymatic 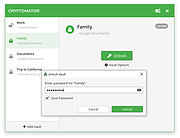 |
|
| CyberShredder v1.12 CyberShredder v1.12 CyberShredder is a quick, safe and handy utility that lets you erase confidential files from your computer permanently. Normal file deletion will remove a file's directory entry and allocation table information. The actual disk clusters that contained the file's data remains intact on your hard disk and can be recovered later. CyberShredder overwrites the space occupied from a file with random data and erases the file, so an unerase utility will never be able to recover it. CyberShredder's simple interface will help you get rid of confidential data permanently. It deletes files using three different shredding methods, including the NSA approved seven-pass file deletion method. Please note that files and directories erased by CyberShredder can not be recovered using an undelete program. Make sure you use it with care. We recommend that you learn how to use the program by testing its behaviour with some test data first. Version 1.12: Quicker abort, abandons operation even at the end of a file operation File operation progress gauge, shows progress of each file operation (pass) Renames file multiple (26) times, not just once Remembers form position Click here to visit the author's website. |
 |
4,604 | Mar 02, 2019 CyLog Software  |
|
| Debotnet v0.7.7 Debotnet v0.7.7 Debotnet is a free and portable tool for controlling Windows 10's many privacy-related settings and keep your personal data private. The Windows 10 default privacy settings leave a lot to be desired when it comes to protecting you and your private information. Whenever I set up a new computer or update a current setup for my family or job, I always carefully go through the privacy settings for each install, making sure to lock it down to make it as private as possible. Windows 10 has raised several concerns about privacy due to the fact that it has a lot of telemetry and online features, which send your data (sensitive and not) to Microsoft and can't be disabled. If you haven’t yet installed Windows 10, or if you’re planning on buying a PC with Windows 10 already installed, do NOT use the “Express Settings” option when you do your initial setup. Instead, select “Custom Settings” so you can take charge of locking down your privacy from the get-go. After the Installation Debotnet is coming into play. It prevents Windows 10 on basis of a dozen of script files from sending your data to Microsoft. The most important features at a glance Disable telemetry and online features, which send your data (sensitive and not) to Microsoft Choose which unwanted functions you wish to disable Uninstall Windows 10’s Built-in Apps Debotnet will show you what it's doing. You have full control, because the executing code can be viewed in a simple text editor Debug mode. E.g. the Test mode lets you see which values are twisted in registry, commands executed etc. Simple scripting engine for adding custom privacy rules Scripts updated ... |
 |
3,867 | Apr 12, 2020 Mirinsoft  |
|
| DeepSound 2.0 DeepSound 2.0 DeepSound is a steganography tool and audio converter that hides secret data into audio files. The application also enables you to extract secret files directly from audio files or audio CD tracks. DeepSound might be used as copyright marking software for wave, flac, wma, ape, and audio CD. DeepSound also support encrypting secret files using AES-256(Advanced Encryption Standard) to improve data protection. The application additionally contains an easy to use Audio Converter Module that can encode several audio formats (FLAC, MP3, WMA, WAV, APE) to others (FLAC, MP3, WAV, APE). System requirements: - Windows XP/Vista/7/8 - Microsoft .NET Framework 3.5 Documentation: 1 DeepSound 2.0 1.1 Hide data into carrier audio file To hide data into audio file, follow these steps: Select carrier audio file or drag and drop audio file (flac, wav, wma, mp3, ape) into the file explorer. Click to 'Add files' or drag and drop secret files into the panel on the right side of application. Press F3 key or click to encode secret files. You can choose output audio format (wav, flac or ape). DeepSound does not support wma output format. If you want to hide data into wma, hide secret data into wav file and then use external software such as Windows Media Encoder for convert wav to wma lossless file. In settings dialog you can turn On/Off encrypting and set password. Modified audio file will be copied to output directory. Click Ok to start hiding secret files into carrier audio file. 1.2 Extract secret data from audio file or audio CD track To extract secret data from audio file, follow these steps: In the file explorer, select audio file or audio CD track, which contains secret data. If the secret files are encrypted, enter ... |
 |
6,285 | Mar 16, 2016 Jozef Bátora 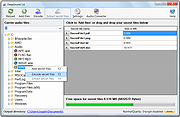 |
|
| DeleteOnClick 2.3.0.0 DeleteOnClick 2.3.0.0 DeleteOnClick is a very simple to use file secure delete utility for Microsoft Windows 98SE/ME/ 2000/XP/2003 and Vista. Any type of file can be deleted, including NTFS compressed and NTFS encrypted files. DeleteOnClick completely deletes files in one click and the data becomes unrecoverable, and also has the option to wipe free disk space. For this reason you must use the program carefully. Once a file is 'Securely Deleted' no one can undelete it. |
 |
8,586 | Feb 24, 2014 2brightsparks |
|
| DidMySettingsChange v1.0.0.5 DidMySettingsChange v1.0.0.5 A python script that checks to see if your privacy settings got changed without you noticing. Microsoft has been under heavy scrutiny with how they manage Windows over the years, particularly concerning privacy and telemetry settings. Many users find that after disabling certain settings, these settings are mysteriously re-enabled after updates or without any apparent reason. DidMySettingsChange is a Python script designed to help users keep track of their Windows privacy and telemetry settings, ensuring that they stay in control of their privacy without the hassle of manually checking each setting. Here's a visual example of how DidMySettingsChange detects changes in your system settings: Before (Normal State) The setting is in its expected state. After (Setting Changed) A change was detected! The tool flags this with both a report and a log entry so you can act accordingly. Features: • Comprehensive Checks: Automatically scans all known Windows privacy and telemetry settings. • Change Detection: Alerts users if any settings have been changed from their preferred state. • Customizable Configuration: Allows users to specify which settings to monitor. • Easy to Use: Simple command-line interface that provides clear and concise output. • Logs and Reports: Generates detailed logs and reports for auditing and troubleshooting. Installation: 1) Download below. 2) Unzip the contents. 3) Run the .py script. 4) Repeat step 3 after installing Windows updates. Changes: v1.0.0.5 27 Mar 2025 -Added a UI interface -Cleaned up some code -Bug Fixes Click here to visit the author's website. |
 |
150 | Apr 01, 2025 nolesapex 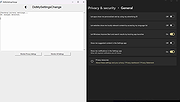 |
|
| DiskCryptor v1.3 DiskCryptor v1.3 An open-source, free encryption software for Windows to encrypt hard drives, partitions, and external storage devices. It was initially released in 2008 by a developer known as ‘ntldr,’ and it’s been helping people safeguard their data ever since. Features • Support of AES, Twofish, Serpent encryption algorithms, including their combinations. - Transparent encryption of disk partitions. - Full support for dynamic disks. - Support for disk devices with large sector size (important for hardware RAID operation). • High performance, comparable to efficiency of a non-encrypted system. - Support for hardware AES acceleration: AES New Instructions set on recent Intel and AMD CPUs; PadLock extensions on VIA processors. - Support for the SSD TRIM extension. • Broad choice in configuration of booting an encrypted OS. Support for various multi-boot options. - Full compatibility with UEFI/GPT boot - MBR bootloader Full compatibility with third party boot loaders (LILO, GRUB, etc.). - Encryption of system partitions with pre-boot authentication. - Option to place boot loader on external media and to authenticate using the key media. - Support for key files. • Full support for external storage devices. - Option to ... |
 |
1,508 | Mar 29, 2024 David Xanatos  |
|
| Easy File Locker 32bit 2.2 Easy File Locker 32bit 2.2 Easy File Locker is a light-weight and easy-to-use file lock software product for Windows. It can protect your private files and folders. With its great protection, users will not be able to open, read, modify, delete, move, copy the locked files/folders, or even not be able to see it. The hidden files/folders will be totally invisible to all users and to any program. Easy File Locker will keep protecting the files/folders even under Windows Safe Mode. It is designed for protecting files/folders on your local computer. it doesn't change the protected files and folders, it will not slow down the system speeds and it will never have the chance to destroy your data. Lock files, Lock folders: The locked files/folders are protected from accessing, users can not open, read, modify, move, delete, copy, rename the protected files/folders. Files and sub-folders in a locked folder are also protected. Hide files, Hide folders: You can hide your private files and folders, to make them completely invisible to users and programs. Password protected GUI and uninstaller: Once you set a password, no one can launch the application or uninstall the software without the correct password. |
 |
8,476 | Jan 13, 2017 XOSLAB.COM  |
|
| Easy File Locker 64bit 2.2 Easy File Locker 64bit 2.2 Easy File Locker is a light-weight and easy-to-use file lock software product for Windows. It can protect your private files and folders. With its great protection, users will not be able to open, read, modify, delete, move, copy the locked files/folders, or even not be able to see it. The hidden files/folders will be totally invisible to all users and to any program. Easy File Locker will keep protecting the files/folders even under Windows Safe Mode. It is designed for protecting files/folders on your local computer. it doesn't change the protected files and folders, it will not slow down the system speeds and it will never have the chance to destroy your data. Lock files, Lock folders: The locked files/folders are protected from accessing, users can not open, read, modify, move, delete, copy, rename the protected files/folders. Files and sub-folders in a locked folder are also protected. Hide files, Hide folders: You can hide your private files and folders, to make them completely invisible to users and programs. Password protected GUI and uninstaller: Once you set a password, no one can launch the application or uninstall the software without the correct password. |
 |
8,546 | Jan 13, 2017 XOSLAB.COM  |
|
| EasyCrypt v2.01 EasyCrypt v2.01 EasyCrypt is a simple and easy to use file encryption and decryption tool. Fast encrypt or decrypt files with AES-256, a very secure encryption algorithm. Features: Lightweight, simple and easy to use UI Secure encryption with AES-256, a random IV and 256-bit (32 bytes) salt Fast encryption and decryption Requirements: .NET Framework 4.5 2 GHz Processor, 128 MB RAM 2 MB of free disk space MD5 · 4fbc229845a7cef249ac4fed5e1d2c14 SHA1 · 731b6853575c60bc382f0978d939a9365019be88 SHA256 · de595d00b24412be4916c19f3e081d79e319217b3dc30f0cd8104ab4601bb102 Changes: v2.01 Small Improvements |
 |
5,330 | Jun 08, 2021 HEXAGON Developments 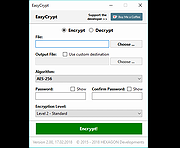 |
|
| EncryptOnClick v2.4.2.0 EncryptOnClick v2.4.2.0 EncryptOnClick Freeware is a program that lets you securely encrypt and decrypt files. It uses 256-bit AES encryption and compression that is compatible with WinZip 9 and newer, SecureZip and other modern compression utilities. To use EncryptOnClick on a USB flash drive, simply copy the following files from the program's directory to the USB device: EncryptOnClick.exe EncryptOnClick.exe.manifest XceedZip.dll Benefits A very secure encryption method is also used (256-bit AES encryption). Files are both compressed & encrypted, which results in a smaller file. Optionally encrypt the filenames. Password protected. Will encrypt and decrypt single files, a selection of files or all files in a folder. Very simple to use interface. Can be used on a USB key. Fully Unicode enabled so filenames in any language can be encrypted. Click here to visit the author's website. |
 |
2,762 | Jun 28, 2021 2BrightSparks Pte Ltd 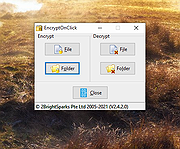 |
|
| EncryptPad v0.4.0.4 for Mac EncryptPad v0.4.0.4 for Mac EncryptPad is an application for viewing and editing symmetrically encrypted text. Using a simple and convenient graphical and command line interface, EncryptPad provides a tool for encrypting and decrypting binary files on disk while offering effective measures for protecting information, and it uses the most widely chosen quality file format **OpenPGP** [RFC 4880](https://tools.ietf.org/html/rfc4880). Unlike other OpenPGP software which main purpose is asymmetric encryption, the primary focus of EncryptPad is symmetric encryption. Features Symmetric encryption Passphrase protection Key file protection Combination of passphrase and key file Random key file generator Key repository in a hidden directory in the user's home folder Path to a key file can be stored in an encrypted file. If enabled, you do not need to specify the key file every time you open files. Encryption of binary files (images, videos, archives etc.) Read only mode to prevent accidental file modification UTF8 text encoding Windows/Unix configurable line endings Customisable passphrase generator helps create strong random passphrases. File format compatible with OpenPGP Iterated and salted S2K Passphrases are not kept in the memory for reuse, only S2K results (more ...) Cipher algorithms: CAST5, TripleDES, AES128, AES256 Hash algorithms: SHA-1, SHA-256, SHA-512 Integrity protection: SHA-1 Compression: ZLIB, ZIP Large multi-gigabyte files are supported Why use EncryptPad? Multi-platform codebase: it has been compiled on three popular operating systems and can be adapted to more. Portable: simply copy the executable to a ... |
 |
4,976 | Nov 19, 2019 Evgeny Pokhilko 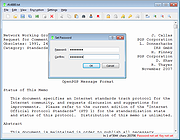 |
|
| EncryptPad v0.4.0.4 for Windows EncryptPad v0.4.0.4 for Windows EncryptPad is an application for viewing and editing symmetrically encrypted text. Using a simple and convenient graphical and command line interface, EncryptPad provides a tool for encrypting and decrypting binary files on disk while offering effective measures for protecting information, and it uses the most widely chosen quality file format **OpenPGP** [RFC 4880](https://tools.ietf.org/html/rfc4880). Unlike other OpenPGP software which main purpose is asymmetric encryption, the primary focus of EncryptPad is symmetric encryption. Features Symmetric encryption Passphrase protection Key file protection Combination of passphrase and key file Random key file generator Key repository in a hidden directory in the user's home folder Path to a key file can be stored in an encrypted file. If enabled, you do not need to specify the key file every time you open files. Encryption of binary files (images, videos, archives etc.) Read only mode to prevent accidental file modification UTF8 text encoding Windows/Unix configurable line endings Customisable passphrase generator helps create strong random passphrases. File format compatible with OpenPGP Iterated and salted S2K Passphrases are not kept in the memory for reuse, only S2K results (more ...) Cipher algorithms: CAST5, TripleDES, AES128, AES256 Hash algorithms: SHA-1, SHA-256, SHA-512 Integrity protection: SHA-1 Compression: ZLIB, ZIP Large multi-gigabyte files are supported Why use EncryptPad? Multi-platform codebase: it has been compiled on three popular operating systems and can be adapted to more. Portable: simply copy the executable to a ... |
 |
5,092 | Nov 19, 2019 Evgeny Pokhilko  |
|
| Eraser v6.2.0.2996 Eraser v6.2.0.2996 An advanced security tool for Windows which allows you to completely remove sensitive data from your hard drive by overwriting it several times with carefully selected patterns. Features • Erases residue from deleted files • Erases MFT and MFT-resident files (for NTFS volumes) and Directory Indices (for FAT) • Powerful and flexible scheduler Supported operating systems: Windows XP (with Service Pack 3), Windows Server 2003 (with Service Pack 2), Windows Vista, Windows Server 2008, Windows 7, 8, 10, 11 and Windows Server. Eraser is Free software and its source code is released under GNU General Public License. Why Use Eraser? Most people have some data that they would rather not share with others – passwords, personal information, classified documents from work, financial records, self-written poems, the list continues. Perhaps you have saved some of this information on your computer where it is conveniently at your reach, but when the time comes to remove the data from your hard disk, things get a bit more complicated and maintaining your privacy is not as simple as it may have seemed at first. Your first thought may be that when you ‘delete’ the file, the data is gone. Not quite, when you delete a file, the operating system does not really remove the file from the disk; it only removes the reference of the file from the file system table. The file remains on the disk until another file is created over it, and even after that, it might be possible to recover data by studying the magnetic fields on the disk platter surface. Before the file is overwritten, anyone can easily retrieve it with a disk maintenance or an undelete utility. Click here to visit the author's website. |
 |
9,126 | May 27, 2025 Heidi Computers LTD 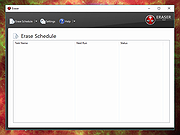 |
|
| Eusing Maze Lock v4.2 Eusing Maze Lock v4.2 Pattern based technique to lock your computer. Locking your screen prevents other people from accessing your computer while you are away from it. There are several applications able to help you lock your computer. However, few of these applications are comparable to Eusing Maze Lock. Eusing Maze Lock uses a new technique to help your computer. This technique is pattern based. You need first to set your own unlock pattern by connecting some of the nine dots together (There is a default unlock pattern has been pre-set). When you try to unlock your computer, you need to draw the same pattern exactly as you set. It is a cool software which lets you to lock your pc with your customize maze. Eusing Maze Lock is a powerful tool designed to help you lock your computer with a single click on the tray icon. While it provides a different locking system than the one bundled into Windows, Eusing Maze Lock places an icon in the system tray that allows you to either lock the machine instantly or using a custom hotkey. Then Eusing Maze Lock will display a lock screen and protected your computer. Overall, Eusing Maze Lock is a useful application that serves its purpose and provides some interesting configuration options that can be easily set up by both beginners and more experienced users. You can specify the lock screen background image, change the pattern to 4 x 4 or 5 x 5. Eusing Maze Lock can auto-lock the computer when windows startup and computer inactivity. With this unique application installed on your computer you will get a truly impressive security application. Key Features Pattern based technique to lock your computer Quick and safe computer lock by hot key, or mouse click ... |
 |
2,366 | Dec 08, 2021 Eusing Software  |
|
| Fastlock v1.2 Fastlock v1.2 Fastlock is a small and fast utility to hide the screen activity with a security password. This tool blocks any windows control components: Alt+F4, Alt+Tab, Task Manager, Windows Keys, Security Screen. There is no way to kill Fastlock's process and get access to your desktop. Difference to system's lock screen: There is no CPU deceleration, which enables you an instant access to your programs after unlocking. Notice, that Fastlock is only a temporary solution to lock your screen. Changelog: Version 1.2: - Fixed taskbar and starbutton flickering - Fixed possible access to the startmenu by spamming winbutton - Implemented new error exceptions - Changes in the Fastlock's Password Tool are now being processed in real-time - Locked keys and changing keyboard layout are now being displayed |
 |
5,300 | May 30, 2017 2xDSoft  |
|
| Fate v11.02.1 Fate v11.02.1 File And Text Encryption No nonsense file and text encryption for Windows and Linux. Fate is a stripped down, no nonsense, no options encryption utility for normal users who just want to secure their files and text and move on. The ciphers used are Aria, Camellia, (all in 256 bit key mode) and ChaCha20. Modes are CBC, OFB, CFB, and CTR, except for ChaCha20 which is a stream cipher. The password hashing and salt derivation are robust. Features • No hassle file and text encryption Note from author: Some encryption utilities offer more-than-is-necessary options, and Fate was created to achieve very secure file and text encryption with no confusing options to consider. The ciphers used are ChaCha20, Aria(256), and Camellia(256) the modes used are CBC, CFB, OFB, and CTR. (ChaCha20 is a stream cipher and does not use modes) Fate sends your passwords through robust hashing and salting routines, and then calls on OpenSSL to do the actual encryption. The ciphers and modes are randomly chosen at runtime. These ciphers are all newer than the Rijndael cipher, aka AES, and are held in high regard by the cybersecurity community. Fate requires the use of OpenSSL and Cat, these two utilities are standard in every Linux distribution, but not so much on Windows. A copy of Windows ports of these two utils are in the zip file, you can place them in the working directory, you can place them in your path for a more permanent solution. I've included a small script in the archive named ossl_path.exe, and if run, this script will place openssl.exe and cat.exe in the users' path, if you're unsure of how to do that, see the separate readme file for that script. If you like to use these little scripts that I make, consider writing an email and tell me where you're from. Have fun! Dana ... |
 |
712 | Feb 01, 2024 Dana Booth  |
|
| Fawkes v0.3 Fawkes v0.3 Image "Cloaking" for Personal Privacy 2020 is a watershed year for machine learning. It has seen the true arrival of commodized machine learning, where deep learning models and algorithms are readily available to Internet users. GPUs are cheaper and more readily available than ever, and new training methods like transfer learning have made it possible to train powerful deep learning models using smaller sets of data. But accessible machine learning also has its downsides. A recent New York Times article by Kashmir Hill profiled clearview.ai, an unregulated facial recognition service that has downloaded over 3 billion photos of people from the Internet and social media and used them to build facial recognition models for millions of citizens without their knowledge or permission. Clearview.ai demonstrates just how easy it is to build invasive tools for monitoring and tracking using deep learning. So how do we protect ourselves against unauthorized third parties building facial recognition models that recognize us wherever we may go? Regulations can and will help restrict the use of machine learning by public companies but will have negligible impact on private organizations, individuals, or even other nation states with similar goals. The SAND Lab at University of Chicago has developed Fawkes1, an algorithm and software tool (running locally on your computer) that gives individuals the ability to limit how their own images can be used to track them. At a high level, Fawkes takes your personal images and makes tiny, pixel-level changes that are invisible to the human eye, in a process we call image cloaking. You can then use these "cloaked" photos as you normally would, sharing them on social media, sending them to friends, printing them or displaying them on digital devices, the same way you would any other photo. The difference, however, is that if and when someone ... |
 |
3,709 | Aug 20, 2020 The SAND Lab at University of Chicago  |
|
| File Access Monitor 1.0.2 File Access Monitor 1.0.2 File Access Monitor is a multipurpose tool that monitors access to your files and provides detailed history of who read, wrote and manipulated them. SoftPerfect File Access Monitor can be used on a file server to track network users activity, as well as on a local computer where it will track local users file access. It is similar in nature to Windows auditing features yet is much easier to use and provides flexible reporting capabilities and notifications. Key features Monitors file actions: creating, moving, deleting, reading and writing to files. Records remote user access to shared folders. Keeps track of local users as to what files they access. Features a powerful filter system to include or exclude certain activities. Self-contained, doesn’t require a database server alongside. Supported platforms Windows XP through Windows 10, Windows Server 2003 through 2012 32-bit and 64-bit Changelog: 2016-10-10 1.0.2 This software is now freeware. |
 |
5,527 | Dec 14, 2016 SoftPerfect 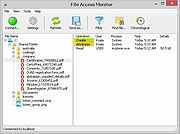 |
|
| FileCrypt R1.0 Rev4 FileCrypt R1.0 Rev4 FileCrypt is a fast, free and secure file encryption software. It's portable and very easy to use. Supported algorithms: AES, RC2 and TripleDES. All are available in their supported key sizes. More algorithms may be added in the future. It encrypts your files very securely using 32-bit long salts and a IV. You can drag and drop files into FileCrypt to quickly add them. Press F10 on your keyboard while not setting a password to switch between visible and non visible password mode. System Requirements: 1,2 GHz Single-Processor, 512 MB RAM, Windows Vista or higher, .NET Framework 4.5.2 |
 |
5,343 | Aug 01, 2017 Davaxyr 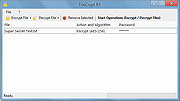 |
|
| Files Terminator Free (PORTABLE) 2.6.0.0 Files Terminator Free (PORTABLE) 2.6.0.0 Secure deletion of sensitive data! Files Terminator Free is an easy to use application that allows users to permanently delete their files and wipe free disk space. Portable version available. The utility protects the users privacy by permanently delete sensitive documents, images, videos and other files and by overwriting the free disk space. The software uses several shredding methods (one pass Pseudorandom, British HMG IS5, two pass Russian GOST P50739-95, three pass US DoD 5220.22M, seven pass German VSITR, Canadian RCPM TSSIT OPS-II, Bruce Schneier and the 35-pass Peter Gutmann) and supports drag and drop for easier use. During file shredding the content of the selected files are overwritten several times with random data and predefined characters and cannot be recovered any more. Finally, Files Terminator Free is a quick and easy to use application with a user-friendly interface that helps users permanently delete sensitive documents and swap free disk space. |
 |
8,783 | Jan 19, 2014 Elefant Software |
|
| Files Terminator Free 2.6.0.0 Files Terminator Free 2.6.0.0 Secure deletion of sensitive data! Files Terminator Free is an easy to use application that allows users to permanently delete their files and wipe free disk space. Portable version available. The utility protects the users privacy by permanently delete sensitive documents, images, videos and other files and by overwriting the free disk space. The software uses several shredding methods (one pass Pseudorandom, British HMG IS5, two pass Russian GOST P50739-95, three pass US DoD 5220.22M, seven pass German VSITR, Canadian RCPM TSSIT OPS-II, Bruce Schneier and the 35-pass Peter Gutmann) and supports drag and drop for easier use. During file shredding the content of the selected files are overwritten several times with random data and predefined characters and cannot be recovered any more. Finally, Files Terminator Free is a quick and easy to use application with a user-friendly interface that helps users permanently delete sensitive documents and swap free disk space. |
 |
8,778 | Jan 19, 2014 Elefant Software |
|
| FinalCrypt v6.3.8 FinalCrypt v6.3.8 World's strongest encryption & #1 one-time pad encryption. Why FinalCrypt ? Today's cyber espionage comes from hidden spyware waiting for you to unlock your drive. Disk Encryption no longer protects! Even when you're logged on, unopened files have to remain encrypted. Only File Encryption stops spyware reading your files. Also most crypto software uses broken AES or asymmetric crypto soon broken by The Shor's Algorithm with Quantum Computers. Today's global cyber espionage can only be stopped by One-Time Pad File Encryption. That's why FinalCrypt. FinalCrypt is designed to be as easy as possible for home users offering a good looking Graphical User Interface with user guidance and a professional Command Line Interface for IT professionals to automate reporting, encryption & decryption Automatic Key Generation Another reason why good One Time Pad Encryption software is so scarse is because of its high key demands requiring an equally sized key file for every encrypted file FinalCrypt is unique in its Key Management as it automatically generates FIPS 140-2 & RFC1750 compliant OTP keys making One Time Pad Encryption easy This download is for the Windows version. If you need the MacOS version, download here. If you need the Linux Debian version, download here. If you need the Linux RPM version, download here. Changes: Date: 2020-06-20 Version: 6.3.8 Added new backup mirror to support & check updates Improved open "Download Software" pages on updates Click here to visit the author's website. |
 |
3,450 | Jun 21, 2020 Ron de Jong  |
|
| Firefox Multi-Account Containers v8.0.6 Firefox Multi-Account Containers v8.0.6 A Mozilla Firefox browser add-on that lets you keep parts of your online life separated into color-coded tabs. Cookies are separated by container, allowing you to use the web with multiple accounts and integrate Mozilla VPN for an extra layer of privacy. About This Extension The Firefox Multi-Account Containers extension lets you carve out a separate box for each of your online lives – no more opening a different browser just to check your work email! Under the hood, it separates website storage into tab-specific Containers. Cookies downloaded by one Container are not available to other Containers. You can even integrate individual Containers with Mozilla VPN to protect your browsing and location. With the Firefox Multi-Account Containers extension, you can... Sign in to two different accounts on the same site (for example, you could sign in to work email and home email in two different Container tabs. Keep different kinds of browsing far away from each other (for example, you might use one Container tab for managing your Checking Account and a different Container tab for searching for new songs by your favorite band) Avoid leaving social-network footprints all over the web (for example, you could use a Container tab for signing in to a social network, and use a different tab for visiting online news sites, keeping your social identity separate from tracking scripts on news sites) Protect your browsing activity in individual Containers using Mozilla VPN, so you can shop while traveling abroad but check your bank account from a server in your home country. After installing the Firefox Multi-Account Containers extension, click the Containers icon to edit your Containers. Change their colors, names, and icons. Long-click the new tab button to open a new ... |
 |
2,092 | Apr 07, 2022 Mozilla  |
|
| Free File Camouflage 1.25 Free File Camouflage 1.25 Want to save a copy of your personal file on a USB Pendrive but you are worried that, in case of theft, someone will be able to access your data? With Free File Camouflage you can hide your files inside a JPEG image! The software can be used with the main interface or via the explorer "send to" context menu (the first time you only need to select a directory with some images). All the files are encrypted using AES and hidden inside an image. What happens if someone tries to open a camouflaged image? Well... nothing! He will only see the image. Change Info: Version 1.25: - added a new registration method: SMS. Useful if you don't have a credit card or PayPal - new error reporting system engine - various code fix - updated internal libraries code |
 |
8,390 | May 31, 2017 My Portable Software  |
|
| Free File Wiper 1.76 Free File Wiper 1.76 Delete files securely with this software! Just right click on files or directories and select "Send to / Free File Wiper" to erase them completely! Or ... you can drag and drop them on the trashcan to perform the wipe operation. The files will be overwritten with standard and random patterns. After the wipe, the files cannot be undeleted and restored. Up to four wipe methods (from 1 pass to 7 passes). Change Info: -updated registration library code |
 |
8,373 | Apr 01, 2014 My Portable Software |
|
| Free Hide IP 4.1.8.8 Free Hide IP 4.1.8.8 Free Hide IP - The best free privacy protection software. Free Hide IP the best way is to keep your IP address from being shown to others. Hackers and identity thieves are becoming more and more rampant in today's society. They may break into anyone's computer and monitor one's activity or steal one's identity or other personal information. To stay safe online, the best way is to keep your IP address from being shown to others. Now we provide you a FREE solution to hide your IP address. Use Free Hide IP to hide your real IP address for free, anonymize your web surfing, keep your computer safe from hacker attacks and other risks, all with a single click. |
 |
9,171 | Jun 07, 2017 Free Hide IP  |
|
| Free VPN Test v1.1.0.7 Free VPN Test v1.1.0.7 Free program to detect DNS traffic and IP leaks from your VPN. What DNS traffic is your VPN leaking? Your computer uses DNS to lookup the location of web sites and services in order to connect to them. Even if you use a proxy or VPN, your DNS traffic can still be exposed. Your ISP, governments, WiFi hotspot providers and other users on your WiFi hotspot can all see your DNS requests. |
 |
5,086 | Nov 26, 2019 Free VPN Test  |
|
| fSekrit v1.4 fSekrit v1.4 fSekrit is a small application for keeping securely encrypted notes. These notes are truly stand-alone; the editor program and your note are merged together into a tiny self-contained program file, bypassing the need to install a special application to view your data. This makes fSekrit ideal for keeping encrypted notes on, for example, USB flash drives. Another advantage of using fSekrit is that your un-encrypted data is never stored on your harddisk. With a traditional encryption utility you would have to decrypt your file to disk, view or edit it, and then re-encrypt it. Unless you use secure file wiping tools, it would be a trivial matter for someone to retrieve your un-encrypted data, even though you deleted the temporary file. This is not a viable attack against fSekrit, though, since it never stores your un-encrypted data on disk. (See security notes about swapping and hibernation, though!) fSekrit uses very strong encryption to ensure that your data is never at risk. Rather than using hocus-pocus home-brewed algorithms, fSekrit uses the standard, military grade, peer-reviewed AES/Rijndael in CBC mode, with a 256-bit keysize. Self contained fSekrit notefiles are tiny! Only around 50k plus the size of your encrypted text. Release History: ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ version 1.40 - December 3, 2009 - 90kb/45.5kb - fixed: long-standing bug where failing to save changes when closing fSekrit with a modified document would cause fSekrit to exit, rather than notifying of error and let user attempt to save again. - fixed: saves are *finally* done properly, by saving to a temporary file and replacing the current file only when all the file writing business is done. - added: font selection dialog, no longer do you need to much around with the registry to set another default font. The font is still not stored in your document, ... |
 |
5,026 | Oct 22, 2019 f0dder  |
|
| G Security 1.0 G Security 1.0 G Security is an easy to use Desktop locker/Screen locker developed for Microsoft Windows. It allows a user to securely lock down Windows in such a way that it cannot be accessed by an unauthorized user. G Security is light weight and easy to use with a highly user friendly interface. It prevents anyone from accessing your computer when its locked down so that your private data stored on the computer cannot be accessed by anyone. It completely locks down your computer so that even if someone gets a hold of your computer, he or she can do nothing on it. It can lock down your computer on start up as well as any time you want just by pressing some keys. Once the computer is locked down shortcut keys like Alt+tab, Ctrl+Alt+Esc, Alt+F4 etc will not work at all. The Ctrl+Alt+Del screen will also be secured in such a way that no one can unlock you computer without correct password. Any running application will also be prevented from messing up with the locked computer. It can be used by multiple users at a time on a single computer with settings stored for each user individually so that each user can use G Security with its own preferences. G Security also supports hotkey to lock the system. In a few words its extremely secure, easy to use and configurable desktop locking solution available for everyone free of cost. Some of its key features include : Its easy to use. Its a Freeware. Fully locks down your computer. Can protect Windows on startup. Suitable for all kinds of users. Multi user support. ... |
 |
5,706 | Jun 20, 2016 Malik Usman Aura  |
|
| GuardAxon 3.9 GuardAxon 3.9 GuardAxon is a free program that is used to encrypt and decrypt files e.g. for safe transmission or transportation on removable media. The program uses the following encryption algorithms: BlowFish, Twofish, DES, 3DES, AES-128, AES-192, AES-256. Selecting files to protection is very simple because GuardAxon uses the classic file manager. The program can generate reports in PDF format at the end of the encryption / decryption. GuardAxon also allows you to calculate and verify the checksum of files (MD-5, SHA-1, SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, SHA-512/256). |
 |
6,556 | Apr 18, 2015 The Geneosoft Team  |
|
| GuardAxon 3.9 PORTABLE GuardAxon 3.9 PORTABLE GuardAxon is a free program that is used to encrypt and decrypt files e.g. for safe transmission or transportation on removable media. The program uses the following encryption algorithms: BlowFish, Twofish, DES, 3DES, AES-128, AES-192, AES-256. Selecting files to protection is very simple because GuardAxon uses the classic file manager. The program can generate reports in PDF format at the end of the encryption / decryption. GuardAxon also allows you to calculate and verify the checksum of files (MD-5, SHA-1, SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, SHA-512/256). |
 |
6,586 | Apr 18, 2015 The Geneosoft Team  |
|
| Hardwipe v5.2.1 Hardwipe v5.2.1 Hardwipe is the free data sanitization toolset used by activists, journalists, IT technicians and anyone needing to ensure that discarded, but sensitive, information can never be recovered by someone else. Freedom to Securely Erase Sensitive Information Use Hardwipe to permanently erase (or "hard wipe") data on disk and portable storage media. Hardwipe for Desktop provides a slick user interface with optional support for "right-click" context menus in Windows File Explorer. It can conveniently destroy files and folder contents on-demand, erase drives and USB media, and sanitize the Windows Recycler. Hardwipe for Desktop is free for non-commercial use. |
 |
6,268 | Mar 08, 2019 Big Angry Dog  |
|
| Image Lock PEA v1.3 Image Lock PEA v1.3 Protects photos, drawings, and documents with a password. Thanks to the integrated viewer the images are never stored unencrypted on the hard disk, but are held only in the memory. Because all documents can be easily converted in image formats like png, bmp, gif or jpg, the Image Lock PEA is also suitable to display all sorts of documents with a little more effort. You can use for example the PeaFactory's extra menu to convert pdf files into images which can than be encrypted with the Image Lock PEA. Image Lock PEA uses functions to derive the key from the password, that protect against attackers with a high budget (availability of ASICs, FPGAs). The authenticated Encryption (EAX mode) ensures the integrity and authenticity in addition to confidentiality. The Image Lock PEA offers the possibility to export the encrypted images unencrypted. Different images can be managed by one PEA and can be encrypted with different passwords. Since version 1.0 you can encrypt several images, but for performance reasons, Image Lock PEA is still not suitable for managing a large number of images. Key Derivation Function: Catena-Dragonfly, Argon2 Cipher (EAX-Mode): Threefish, AES-256 Hash Function: Blake2b, SHA-3 How to use Start the Jar Archive You need OpenJDK, Java Runtime Environment (JRE) or something similar. On most systems there is at least one available. These PEAs are single Java jar archives, a file with the extension "jar". If you are familiar with jar archives, you can skip the following part. Linux, BSD systems and Mac OS and other UNIX like systems: unpack the compressed download file (tar or unzip), store it for example in your home folder, change in the directory in konsole and type: java -jar YOUR_ARCHIVE.jar or try to double click the file unix_start_imagePEA.sh. Windows: Normally you can open the jar archive just by a double click. But sometimes ... |
 |
2,337 | Dec 08, 2021 Peafactory  |
|
| JPEG & PNG Stripper v1.5.7.70 JPEG and PNG Stripper v1.5.7.70 A tool for stripping/cleaning/removing unnecessary metadata (junk) from JPG/JPEG/JFIF and PNG files. The image quality IS NOT AFFECTED. Includes command line support. Just specify a folder or file on the commandline (wildcards allowed) Supported operating systems: Windows 95 through Windows 11 A few notes on this one: 1) There are a few hits on VirusTotal for this file. We have confirmed that these are false positives. The file is safe. 2) This program will commence to stripping metadata from any images you drag to it's window immediately without confirming with you. If this is not the behavior you desire, check the Preview Only box before dragging. Commandline Syntax /GUI={0|1} /IGNORE-READONLY={0|1} /PRESERVE-DATETIME={0|1} anything else on the command line is treated as a folder or filename (allows wildcards) examples stripper /gui=0 c:\path\test.jpg stripper /gui=0 c:\path\test.* /ignore-readonly=1 This download is for the English version. If you need the German version, download here. Click here to visit the author's website. |
 |
1,530 | Feb 14, 2023 SteelBytes  |
|
| KCleaner v3.8.0.110 KCleaner v3.8.0.110 KCleaner is designed to be the most efficient Hard Disk cleaner, tracking every useless byte in order to give you all the ressources you may need for your documents, music, pictures, movies,... It is the first product of this kind featuring a full automatic mode, which works in background so that you don't have to care about when to launch it. As a proof of its efficiency, it often finds up to many Gb not even seen by its competitors so... give KCleaner a try ! And if data security is something you are interested in, you'll love the secured file deletion methods proposed by KCleaner, making deleted files unrecoverable by any known mean. Features Detects and cleans temporary and useless files (cache, unused setup files...) Automatic mode working in background Secured file deletion method Expert mode : let users control any file deletion done by KCleaner Internationalization support. Changes: KCleaner - 3.8 Released 2021-02-21 0006382: [Refactoring] Updated French translation (Kyle_Katarn) 0006378: [New Feature] Capacity to remove licence (Kyle_Katarn) 0004732: [Bug] Does not clean browser caches (Kyle_Katarn) 0006348: [Refactoring] Updated Chinese translation (Kyle_Katarn) 0006335: [Refactoring] Updated Dutch translation (Kyle_Katarn) Click here to visit the author's website. |
 |
4,694 | Feb 22, 2021 KC Softwares 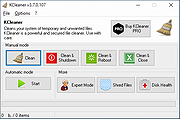 |
|
| KeyLock v2.1.20101.1 KeyLock v2.1.20101.1 KeyLock is a program to lock your computer with a USB Flash Drive or a phone. Safe: It's not possible to use your computer after you've locked it with KeyLock. Our exclusive technologies use the Windows lock screen to lock your PC, making it impossible to reach the desktop. After unlocking, you can immediately use your computer again. Easy and Quick: You quickly need your computer with the common Windows security? First you need to unlock, type your password, have a typo, type in again and finally, your pc is unlocked. With KeyLock, all these problems are solved: Press "Unlock" on your phone or put your USB Flash Drive in your computer and you can use it immediately. Changelog: 2.1.1 18 August 2018 - Bug fixes There are two malware hits on Virus Total. These are false positives. The program has been tested malware free. Click here to visit the author's website. |
 |
7,714 | Dec 28, 2018 Brabonet  |
|
| KeyScrambler 3.8.0.0 KeyScrambler 3.8.0.0 KeyScrambler encrypts your keystrokes deep in the kernel, foiling keylogging attacks with scrambled, undecipherable data. This advanced method of keystroke protection defeats both known and unknown keyloggers. The friendly interface displays realtime encrypted stream of keystrokes so you see when and how KeyScrambler is working. Strengthens where defenses are the weakest in your traditional anti-virus, anti-malware programs and PC security. Compare Editions A free browser add-on, KeyScrambler Personal protects all your inputs in IE, Firefox, and Flock. KeyScrambler Pro and Premium are paid programs that protect a wide array of apps. How It Works KeyScrambler encrypts your keystrokes at the keyboard driver level and decrypts them at the destination application, giving keyloggers "scrambled," useless keys to record. For Online Games Both KeyScrambler Pro and Premium protect your player's IDs, passwords and digital assets in over two dozen online games. For Business Read how and why KeyScrambler is important for your business. KeyScrambler Premium protects critical systems and reduces risks of information theft at the workplace. Features KeyScrambler defeats known and unknown keyloggers; also protects Chinese, Japanese, and Korean inputs; is compatible with other security programs, tokens and smart cards; and requires no user effort. How To The user-friendly interface allows you to do things on KeyScrambler for a more comfortable, personalized fit. Supports: Advanced Browser, AM Browser, AOL Explorer, AOL 9, Avant, Comodo Dragon, Comodo IceDragon, CometBird, Crazy Browser, Firefox, Flock, Google Chrome, Internet Explorer, K-meleon, Maxthon, MSN Explorer, Netscape, Orca Browser, Opera, Safari, Seamonkey, SlimBrowser, SR Iron Browser, TheWorld Browser, Palemoon, Lunascape, RockMelt, WaterFox, and Yahoo Browser. |
 |
8,072 | Jul 29, 2015 QFX Software  |
|
| KORO File Shredder 4.2.3.0 KORO File Shredder 4.2.3.0 KORO File Shredder is a program to erase sensitive data in a way that a recovery will be impossible. Data will be overwritten several times e.g. using the US DoD 5220.22-M ( ECE ) erasure method. Using File Shredder you can delete files and documents from your hard drive and must not worry about that they could be recovered anytime later. Software tools offered for retrieval of deleted files under Windows, usually called "file recovery" software, are taking advantage of the shortcoming of the Windows "delete" command we are normally using to delete files. In fact, the "delete" operation in Windows only removes some bits of information from file directories so that the files disappear from thefile manager view. To undelete such a file, it is just necessary to repair the entry in the file directory. To remove files permanently from your system, like a shredder does with your paper documents, you have to use a program that is capable of overwriting the files with a series of random generated binary data for multiple times. Thus, the current contents of the files will be overwritten in a way that a recovery is practically unpossible. Wiping out method Before deletion all files are overwritten using one of the following algorithms Zero (1 Pass): Overwrite the files with zeros. DoD (7 Passes): Overwrite files in accordance with the US Department of Defense regulation DoD 5220.22-M(ECE). Gutmann (35 Passes): Overwrite files using the method developed by Peter Gutmann.. This method is considered to be the most secure, but slow. KORO File Shredder will operate on the following versions of Microsoft Windows: Windows 8.1, 8, 7, Vista, XP, 2000 32-bit és 64-bit Operating system. Special features Easy to use interface Multiple preset shredding methods Support for internal and external drives Support for removable media (SD Flash, Compact Flash, USB drives) Fool proof warnings before deleting any files Custom shredding settings to fit your needs Protects system files ... |
 |
6,142 | Jan 14, 2016 Robert Kovacs 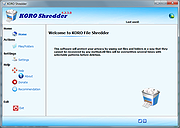 |
|
| KryptoFiler 1.0.2 KryptoFiler 1.0.2 Encrypt and decrypt files, documents, and archives through major cryptographic standards, including, TripleDES, Blowfish, TwoFish, Cast128, DES, Ice, Ice2, RC2, RC4, RijnDael, Serpent, Tea, Thin Ice. Features: Strong encryption : Support for cryptographic standards, TripleDES, Blowfish, TwoFish, Cast128, DES, Ice, Ice2, RC2, RC4, RijnDael, Serpent, Tea, Thin Ice. Hash data through various secure algorithms including Haval 256, MD4, MD5, RipeMD-128, RipeMd-160, SHA1, SHA256, SHA384, SHA512, Tiger. Using 'salts' in order to defend against dictionary attacks versus a list of password hashes and against pre-computed rainbow table attacks. Encrypt & Decrypt Large Files. OS: Windows Xp/ Vista/ 7/ 8/ 10. What's New version 1.0.2 : added drag and drop |
 |
6,263 | Sep 29, 2015 3nity Softwares 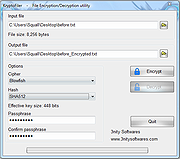 |
|
| KryptoMessage 1.0 KryptoMessage 1.0 Encrypt and decrypt messages, mails and conversations through cryptographic standards, including, TripleDES, Blowfish, TwoFish, Cast128, DES, Ice, Ice2, RC2, RC4, RijnDael, Serpent, Tea, Thin Ice. Features: Strong encryption : Support for cryptographic standards, TripleDES, Blowfish, TwoFish, Cast128, DES, Ice, Ice2, RC2, RC4, RijnDael, Serpent, Tea, Thin Ice. Hash data through various secure algorithms including Haval 256, MD4, MD5, RipeMD-128, RipeMd-160, SHA1, SHA256, SHA384, SHA512, Tiger. Using 'salts' in order to defend against dictionary attacks versus a list of password hashes and against pre-computed rainbow table attacks. Unicode support. OS: Windows Xp/ Vista/ 7/ 8/ 10. What's New version 1 : first release |
 |
6,207 | Sep 29, 2015 3nity Softwares  |
|
| LeoMoon QuickCrypt v2.0.8 LeoMoon QuickCrypt v2.0.8 A file encryption software available on several operating systems that uses the industry standard Advanced Encryption Standard (AES256-CBC) to easily and securely encrypt files. Features Small size Uses strong AES256-CBC encryption algorithm Encrypted files are compatible with Windows, Linux and macOS Includes a password generator Changes: 2.0.8 2021-10-05: Added cross-platform auto dark mode Added Ctrl + M hotkey to toggle dark mode Updated all dependencies Compatibility Windows 7 SP1 and later, macOS 10.14 and later, Ubuntu 16.04 and later Windows MacOS Ubuntu Linux This download is for the Windows version. All other download assets are below: MacOS: leomoon-dot-com_leomoon-quickcrypt_mac.zip Ubuntu: leomoon-dot-com_leomoon-quickcrypt_lin.zip Click here to visit the author's website. |
 |
2,377 | Dec 20, 2021 Amin Babaeipanah  |
|
| MajorPrivacy v0.98.0 MajorPrivacy v0.98.0 A free, cutting-edge privacy and security tool for Windows. Major Privacy offers unparalleled control over process behavior, file access, and network communication. By leveraging advanced kernel-level protections, MajorPrivacy creates a secure environment where user data and system integrity are fully safeguarded. Unlike traditional tools, MajorPrivacy introduces innovative protection methods that ensure mounted encrypted volumes are only accessible by authorized applications, making it the first and only encryption solution of its kind. Features: Process Protection Secure your processes in isolated enclaves, preventing interference from unauthorized applications—even those running with elevated or system-level privileges. Software Restriction Block undesired processes and prevent unauthorized DLLs from loading, ensuring only trusted software operates on your system. Secure Drives – A Revolutionary Encryption Solution MajorPrivacy introduces a game-changing feature for encrypted volumes: • Encrypted Volumes: Create secure disk images to store confidential data. • Guarded Access: Unlike traditional encryption tools where mounted volumes are accessible to any running process, MajorPrivacy ensures that only authorized applications can access data in mounted volumes. Unauthorized processes, even those running with elevated privileges, are completely blocked from interacting with the volume. • This unique approach makes MajorPrivacy the only encryption tool capable of protecting mounted volumes from unauthorized access, ensuring unparalleled security for sensitive data. File and Folder Protection Protect sensitive files and folders from being accessed or modified by unauthorized processes, securing your personal and professional data. Advanced Network Firewall Control inbound and outbound network communications with an advanced firewall, giving you full control over which applications access the internet. DNS Inspection and Filtering DNS Inspection: Monitor DNS cache and trace events to identify domains accessed by running processes. DNS Filtering (Coming Soon): Apply pre-defined blocklists (compatible with Pi-hole) or custom ... |
 |
90 | May 19, 2025 David Xanatos  |
|
| MRU-Blaster 1.5 MRU-Blaster 1.5 Protect your privacy, and keep your PC free from clutter. Find and remove over 30,000 MRU lists. MRU-Blaster is a program made to do one large task - detect and clean MRU (most recently used) lists on your computer. These MRU lists contain information such as the names and/or locations of the last files you have accessed. They are located ALL OVER your registry, and for almost ANY file type. By looking at these MRU lists, someone could determine what files you opened/saved/looked at, what their file names were, and much more! (And, in many cases, the lists are displayed in drop-down menus automatically.) With additional plug-ins that allow you to clean out your Temporary Internet Files and Cookies, MRU-Blaster enhances the protection of your privacy! Clean Up Clutter MRU-Blaster safely, efficiently, and rapidly handles cleaning up tens of thousands of "usage tracks" and other remnants that most programs leave behind. These remnants aren't just a potential privacy concern - they can clog up your registry, and take up valuable space on your hard drive. Windows as well as most third-party programs are culprits. And MRU-Blaster can detect and remove over 30,000 different MRUs and usage tracks. Securely Erase Browsing Tracks MRU-Blaster also supports secure removal of Internet Explorer Temporary Internet Files (cache) and Cookies, with its built-in Plugins. The Internet Explorer cache alone can take up GB (gigabytes) of space on your hard drive. System Requirements MRU-Blaster works on Windows 95, 98, ME, NT, 2000, XP, Vista, 7. |
 |
5,432 | Jan 27, 2017 Brightfort LLC  |
|
| NetMod VPN Client v3.9.6 NetMod VPN Client v3.9.6 Proxy/SSH/OpenVPN/V2Ray A networking tool that has main purpose for VPN with extra settings. Surf any blocked websites through this app privately and securely, You can also add profile (SSH/V2Ray/OpenVPN/Proxy) as much as possible, so you wont get bother when your preferred server down and just change it to another profile by easily. Features Payload Generator Host Checker Multi Profiles SSH-Client OpenVPN-Client SSL / TLS Tunneling Tunneling over VPN Response Replacer Private Configuration File HTTP Ping Host to IP / IP to Host IP Lookup V2Ray What's new in version 3.9.6? -Support multiple any keyword split -Support multiplier for keyword [crlf] | [lfcr] | [cr] | [lf] Example: [crlf*2] This download is for the 64bit version. If you need the 32bit version, download here. Android Version: https://play.google.com/store/apps/details?id=com.netmod.syna Click here to visit the author's website. |
 |
3,736 | Sep 16, 2021 Henry Gustian  |
|
| OandO ShutUp10++ v1.9.1443 OandO ShutUp10++ v1.9.1443 Free antispy tool for Windows 10 and 11 OandO ShutUp10++ means you have full control over which comfort functions under Windows 10 and Windows 11 you wish to use, and you decide when the passing on of your data goes too far. Using a very simple interface, you decide how Windows 10 and Windows 11 should respect your privacy by deciding which unwanted functions should be deactivated. OandO ShutUp10++ is entirely free and does not have to be installed – it can be simply run directly and immediately on your PC. And it will not install or download retrospectively unwanted or unnecessary software, like so many other programs do these days! More control over your operating system • Adapt your security settings • Protect your privacy • Control location services • Do not pass on your user data and diagnostics Further information • Portable Version – no installation required • Free of charge for private users, • companies and educational institutions • Operating System: Supports all Microsoft® Windows 11 and Windows 10 • Available in English, German, French, Italian, Spanish, • Russian and Chinese (simplified) Windows 11 and Windows 10 wants to give users the easiest possible daily experience and in doing so very rarely forces you to actually read and confirm a security notice. Unfortunately, this simplified approach from Microsoft means much more data is passed onto them than many users would like. Microsoft uses most data to display personalized information to you that is aimed at making your computer life easier. As an example, Windows can remind you to set off to the airport 30 minutes earlier due to traffic ... |
 |
7,408 | Feb 12, 2025 OandO Software GmbH  |
|
| OnionShare v2.1 (MacOS) OnionShare v2.1 (MacOS) OnionShare lets you securely and anonymously send and receive files. It works by starting a web server, making it accessible as a Tor onion service, and generating an unguessable web address so others can download files from you, or upload files to you. It does not require setting up a separate server or using a third party file-sharing service. If you want to send files to someone, OnionShare hosts them on your own computer and uses a Tor onion service to make them temporarily accessible over the internet. The receiving user just needs to open the web address in Tor Browser to download the files. If you want to receive files, OnionShare hosts an anonymous dropbox directly on your computer and uses a Tor onion service to make it temporarily accessible over the internet. Other users can upload files to you from by loading the web address in Tor Browser. Documentation To learn how OnionShare works, what its security properties are, and how to use it, check out the wiki. Click here to visit the author's website. |
 |
4,578 | Sep 23, 2019 Micah Lee  |
|
| OnionShare v2.1 (Windows) OnionShare v2.1 (Windows) OnionShare lets you securely and anonymously send and receive files. It works by starting a web server, making it accessible as a Tor onion service, and generating an unguessable web address so others can download files from you, or upload files to you. It does not require setting up a separate server or using a third party file-sharing service. If you want to send files to someone, OnionShare hosts them on your own computer and uses a Tor onion service to make them temporarily accessible over the internet. The receiving user just needs to open the web address in Tor Browser to download the files. If you want to receive files, OnionShare hosts an anonymous dropbox directly on your computer and uses a Tor onion service to make it temporarily accessible over the internet. Other users can upload files to you from by loading the web address in Tor Browser. Documentation To learn how OnionShare works, what its security properties are, and how to use it, check out the wiki. Click here to visit the author's website. |
 |
4,719 | Sep 23, 2019 Micah Lee  |
|
| OpenPuff v4.01 OpenPuff v4.01 An open source, professional steganography tool OpenPuff is a professional steganography tool: HW seeded random number generator (CSPRNG) Deniable steganography Carrier chains (up to 256Mb of hidden data) Carrier bits selection level Modern multi-cryptography (16 algorithms) Multi-layered data obfuscation (3 passwords) X-squared steganalysis resistance Unique layers of security and obfuscation: 256bit+256bit symmetric-key cryptography (with KDF4 password extension) 256bit symmetric-key data scrambling (CSPRNG-based shuffling) 256bit symmetric-key data whitening (CSPRNG-based noise mixing) Adaptive non-linear carrier bit encoding OpenPuff supports many carrier formats: Images (BMP, JPG, PCX, PNG, TGA) Audio support (AIFF, MP3, NEXT/SUN, WAV) Video support (3GP, MP4, MPG, VOB) Flash-Adobe support (FLV, SWF, PDF) OpenPuff is a portable/stealth software: Native portable structure (no installation, registry keys, .ini files) Runs in user mode with DEP on Multithread support (up to 32 CPUs) = Faster processing OpenPuff is safe: Spyware/adware-free Fully redistributable OpenSource core crypto-library (libObfuscate) OpenPuff is a professional steganography tool with unique features, suitable for highly sensitive data covert transmission. Carrier chains: Data is split among many carriers. Only the correct carrier sequence enables unhiding. Moreover, up to 256Mb can be hidden, if you have enough carriers at disposal. Last carrier will be filled with random bits in order to make it undistinguishable from others. Supported formats: Images, audios, videos, flash, adobe. Layers of security: Data, before carrier injection, is encrypted ... |
 |
2,626 | Feb 10, 2022 Embedded SW  |
|
| Optimizer v15.8 Optimizer v15.8 An advanced configuration utility designed to enhance your privacy and security on Windows. This tool is highly recommended for use after a fresh installation of Windows to achieve maximum privacy and security benefits. Depending on your Windows version, Optimizer can also help you apply specific system tweaks. Note: This program has 4 hits on VirusTotal These are false positives due to the changes this program makes to your computer. The program is safe. Features: • Full multilingual support (22 languages available) • Enhance system and network performance • Disable unnecessary Windows services • Turn off Windows telemetry, Cortana, and more • Disable Office telemetry (works with Office 2016 or newer) • Stop automatic Windows 10 updates • Download multiple useful apps quickly • Uninstall UWP apps • Clean system drive and browser profiles • Fix common registry issues • Ping IPs and assess latency • Search IPs on SHODAN.io • Quickly change DNS server (from a pre-made list) • Flush DNS cache • Remove unwanted startup programs • Edit your HOSTS file • Identify and terminate file lock handles • Hardware inspection tool • Add items to the desktop right-click menu • Define custom commands for the run dialog • Support silent runs using a template file Compatibility: • Requires .NET Framework 4.8.1 • Compatible with Windows 7, 8, 8.1, 10, 11 • Can run on Windows Server 2008, 2012, ... |
 |
4,245 | Sep 12, 2023 hellzerg  |
|
| OSE File and Text Encryption v1.11 OSE File and Text Encryption v1.11 Free tool to encrypt files and text using any one of a number of ciphers and modes provided by OpenSSL. Features • Completely portable • Ideal for Tails persistent storage • Very fast encryption Note from the author: OSE, A Graphical Frontend to OpenSSL's symmetric encryption OSE will encrypt files and text using any one of a number of ciphers and modes provided by OpenSSL, and its use is quite self explanatory. OSE is completely self contained and portable, making it ideal for USB flash drives and Tails persistent storage. It will create one file in the working directory, ".ose_cipher", which simply keeps track of the last used cipher. It is not necessary, just there for convenience, and if it's removed or not there, OSE will simply create another one defaulting to aes-128-ecb. Of course, OpenSSL must be present for OSE to work, and additionally, it makes calls to the system utility "echo" when encrypting text, so: Linux - OpenSSL and echo are already part of every distribution Windows - OpenSSL is probably not installed on your system, and the Windows "echo" call is inadequate for use by OSE. OSE, when launched, will spawn both openssl.exe and echo.exe in the working directory. (echo.exe is a Windows port of the UNIX/Linux echo) OSE will clean up these files upon terminating. Notes on long text strings: While you can encrypt a lot of text with the "echo" pipe, it's not unlimited. If you run into the case where OSE informs of a too long text string, an option is included to encrypt text using the TCL AES package using a 256 bit keystream and cbc mode. The password hashing and salting using this mode are extremely robust; you lose no security. Using this mode, the length of the ... |
 |
1,998 | Feb 06, 2024 Dana Booth  |
|
| Permadelete v0.6 Permadelete v0.6 A file shredding app. When a file is deleted, only a reference to the location of the file is deleted. In other words, the file system just “forgets” about the existence of the file. But the actually data, the 0’s and 1’s, still remain on the disk. They will eventually be replaced by other files and data, but this can take a long long time and during this time recovery softwares can be used to recover the “deleted” files. But file shredding apps like Permadelete make sure the files you delete can’t be recovered. If you are the curious type, you can read more about how Permadelete works. You might also want to read this short tutorial about 3 fun ways to shred files permanently using Permadelete. Note: It needs .Net Framework 4.5 to run which you can download here. Changes: Version 0.6 Oct 26, 2019 This small-ish update is all about customization and control! Allow users to customize the apps theme color Allow users to select how many times should a file be overwritten Click here to visit the author's website. |
 |
3,618 | Mar 18, 2020 Muhammad Azeez  |
|
| Permanent Eraser v2.9.1 Permanent Eraser v2.9.1 When you normally delete files on the Mac, the operating system is only forgetting where those particular files are placed, while the data still physically remains on the drive. Beginning with Mac OS X 10.3, Apple enhanced its security by introducing the Secure Empty Trash feature, which follows the U.S. DoD pattern of overwriting data seven times. This feature was then later removed in OS X 10.11 El Capitan. Permanent Eraser provides additional wiping methods such as the 3-pass DoE or 35-pass Gutmann algorithms. This utility overwrites your data multiple times, scrambles the original file name, and truncates the file size to nothing before Permanent Eraser finally unlinks it from the system. Once your data has been erased, it can no longer be read through traditional means. CD/DVD Erasing Permanent Eraser fills in what the Finder forgot! Simply drag a CD-RW or DVD-RW onto Permanent Eraser to erase the disc's contents. Finder Integration Don't want to take up more space in your already cluttered Dock? Instead, drag Permanent Eraser into your Finder's toolbar or sidebar for easy access to wipe away the files you no longer need. Click the icon to empty your Trash, or drag and drop files to erase them. Better Progress Not only has the progress meter's accuracy greatly increased over earlier versions, but it is also displayed from the Dock's icon. Automator + Services Mac OS 10.4+ users get to make use of the bonus Automator Actions and Finder plug-in built to work with Permanent Eraser. Right-click on items you want to destroy and select Services → Erase, or make use of the Erase Trash, Erase Selected Items, or Erase Free Space Automator Actions. International Permanent Eraser has been translated for English, German, French, Italian, Dutch, Swedish, Traditional Chinese, and Welsh. Changes: Permanent Eraser 2.9.1 (18 July 2020) ... |
 |
3,243 | Jan 12, 2022 Edenwaith  |
|
| Pixeloid 1.1 Pixeloid 1.1 Pixeloid A novel and uber-secure way to store data The Pixeloid Matrix The all new Pixeloid Matrix is extremely dense and enables encoding of both text and images(β) along with an automatic ciphering of the data Password Protection Pixeloid additionally provides impenetrable security to users by enabling them to password protect their matrices with Triple Data Encryption Standard (TripleDES) encryption over the automatic ciphering Licensing Pixeloid is Licensed to Ajay Menon and is completely free to use. |
 |
5,284 | Aug 25, 2017 Ajay Menon |
|
| Portable Text Encryption v14.12 Portable Text Encryption v14.12 Self contained and completely portable binary for Windows and Linux encrypts text for secure email, messaging, IRC use, etc. Ideal for USB flash drives. AES-128/192/256 (ecb/cbc), Blowfish (ecb/cbc), DES / TripleDES (ecb/cbc/ofb/cfb), or RC4. Linux and Windows binaries. Features • no config • no helper files • completely portable • very fast text encryption • options save to clipboard or file Note from author: This util does not depend on any external helper utils, and so is completely portable, making it well suited for USB flash drives and Tails persistent storage. It is written in TCL and uses the AES, DES, Blowfish, and RC4 packages from tcllib version 2.1. The use is pretty self explanatory, but... The upper text box is for plaintext, type some text or import a text file, when you "encrypt", this text will be encrypted and the result, the "cipher text", will be displayed in the bottom text box. In the password dialog, there is a checkbox labled "No L/F's in Output". By default, the cipher text will consist of lines with a width of 75 characters, if this box is checked, the output will be one continuous line without line feeds (carriage returns for Windows fans) which is desirable in some cases, i.e., copying and pasting to IRC channels or possibly web page input. If you enjoy these little scripts that I make, consider writing me an email and letting me know where you're from. Dana Booth dana@parksoft.ddns.net Changes: v14.12 - Added option to save ciphertext as file. Added option to import ciphertext from file. Click here to visit the author's website. |
 |
2,301 | Aug 31, 2024 Dana Booth  |
|
| PreventPageFileSnoops v1.0 PreventPageFileSnoops v1.0 Changes a single registry value to force Windows to delete the pagefile.sys file when you shutdown your computer. When your computer runs out of memory (RAM), Windows keeps things running by pretending that a reserved area of your hard drive is RAM. All of the information your that Windows and you programs generate is stored in a single file called pagefile.sys in this reserved area. This file can grow to be several gigabytes in size and does not get deleted when your computer is shutdown. Not only does this use up a sizable chunk of your hard drive, it also opens you up to skilled individuals retrieving this information from your hard drive. PreventPageFileSnoops changes a single registry value to force Windows to delete the pagefile.sys file when you shutdown your computer. AllowPageFileSnoops sets this value back to its default (do not delete pagefile.sys on shutdown). KEEP IN MIND Since the pagefile.sys is sometimes huge and depending on the speed of your computer and hard drive, it could take a few minutes to shut down your computer with this enabled. INSTRUCTIONS (Note: You may not get asked all of these questions.) 1) Double or single click on PreventPageFileSnoops.reg 2) On the Security Warning window, click RUN. 3) When asked "Do you want to allow this app to make changes to your computer?", choose YES. 4) When asked "Adding information can unintentionally change or delete values and cause... Are you sure you want to continue?", choose YES. 5) On the message telling you it was successful, click OK. 6) Restart your computer. The pagefile.sys will not be deleted during this restart but it will be deleted every shutdown after that. Click here to visit the author's website. |
 |
2,430 | Feb 20, 2022 OlderGeeks.com  |
|
| Privacy Badger v2024.7.17 Privacy Badger v2024.7.17 A browser extension that automatically learns to block invisible trackers. Privacy Badger is a browser extension that stops advertisers and other third-party trackers from secretly tracking where you go and what pages you look at on the web. If an advertiser seems to be tracking you across multiple websites without your permission, Privacy Badger automatically blocks that advertiser from loading any more content in your browser. To the advertiser, it’s like you suddenly disappeared. How is Privacy Badger different from other blocking extensions? Privacy Badger was born out of our desire to be able to recommend a single extension that would automatically analyze and block any tracker or ad that violated the principle of user consent; which could function well without any settings, knowledge, or configuration by the user; which is produced by an organization that is unambiguously working for its users rather than for advertisers; and which uses algorithmic methods to decide what is and isn’t tracking. As a result, Privacy Badger differs from traditional ad-blocking extensions in two key ways. First, while most other blocking extensions prioritize blocking ads, Privacy Badger is purely a tracker-blocker. The extension doesn’t block ads unless they happen to be tracking you; in fact, one of our goals is to incentivize advertisers to adopt better privacy practices. Second, most other blockers rely on a human-curated list of domains or URLs to block. Privacy Badger is an algorithmic tracker blocker – we define what “tracking” looks like, and then Privacy Badger blocks or restricts domains that it observes tracking in the wild. What is and isn’t considered a tracker is entirely based on how a specific domain acts, not on human judgment. How does Privacy Badger work? When you view a webpage, that page will often be made up of content from many different sources. (For ... |
 |
3,547 | Oct 08, 2024 Electronic Frontier Foundation  |
|
| Privacy Guardian Keep your what you do on your computer and the Internet protected from prying eyes! Internet and Online Privacy PC Tools Privacy Guardian works with popular Internet browsers to erase your browsing history, search history, cookies, passwords, and download logs to help keep your Internet activities private. It even works with chat programs, media players, FTP browsers, email clients, and peer-to-peer file transfer programs to protect your other online activities as well. Everyday Computing Privacy PC Tools Privacy Guardian also helps maintain your day-to-day computing privacy. Temporary and recent file history erasers clear your temporary file folders, as well as your recently opened files lists, keeping your PC use and file access history private. Other cleaners erase Windows® history, including the ones found in Microsoft® Office, the Recycle Bin, your Recently Run programs, and the Find and Search bar. Secure File Deletion PC Tools Privacy Guardian helps ensure that the files you delete stay deleted with secure file shredding. And to further safeguard your Recycle Bin, a disk-bleaching tool wipes your free hard disk space, preventing of your deleted files from being restored by file recovery tools. |
 |
10,414 | Mar 01, 2012 Pctools |
|
| PrivateWin10 v0.85 PrivateWin10 v0.85 An advanced Privacy tool for windows it provides a simple and comprehensive UI for tweaking privacy settings, as well as options to block system access to files and registry keys in order to enforce privacy whenever Windows does not provide a satisfying setting for that. To solve privacy issues with other software the tool includes a powerful custom firewall frontend for the windows built in firewall. Changes: [0.85] - 2021-09-13 Changed presets now always clean up firewall rules fixed when in rule restoration mode new unsolicited rules are deleted instead of disabled -- no notification is shown as no user action is to be taken Fixed fixed auto undo issue fixed potential crash when loading fw presets fixed compatybility issue with windows insider 21H2 This executable allows you to choose a portable installation. Click here to visit the author's website. |
 |
3,939 | Oct 22, 2021 David Xanatos  |
|
| Privatezilla v0.60.0 Privatezilla v0.60.0 Performs a privacy and security check of Windows 10 Privatezilla integrates the most critical Windows 10 privacy settings and allows you to quickly perform a privacy check against these settings. Active settings are marked with the status "Configured" and indicates that your privacy is protected. The inactive ones are declared as "Not configured". All available settings (currently 60) can be enabled as well as disabled. Maintain privacy Block telemetry and online features, which send your data (sensitive and not) to Microsoft Remove preinstalled and sponsored apps Uninstall Windows 10’s Built-in Apps after clean installation and install your favorite apps again with built-in support for Windows Package Manager Community powered Features community powered and trending script files for your privacy, windows, apps and automation PowerShell scripting Integrated PowerShell scripting engine for adding custom automation tasks Well designed Simple to use modern and familiar UI Free and Portable Small footprint. No installation required and 100% Free Software also for commercial purposes Changes: Privatezilla 0.60.0 (Pollux) ixed critical bug in search and removal of "all built-in apps, except defaults" This was reported here #62 #34 #21 For clarification! If you only want just to remove bloatware apps, so please use the new rewritten option "Remove pre-installed bloatware apps ONLY". The matching takes place on the basis of a community list, which can be viewed here Added LoveWindowsAgain app to Privatezilla package. This is for those planning to upgrade to Windows 11. Click here to visit the author's website. |
 |
5,650 | Feb 06, 2024 Builtbybel 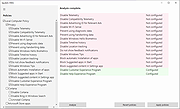 |
|
| PrivaZer v4.0.107 PrivaZer v4.0.107 Free tool that cleans and removes unwanted traces of your past activities. • Internet browsers • Index.dat • Cookies • Cookies Tor • Cookies Flash • Cookies Silverlight • DOM Storage • IndexedDB • AppCache • Registry • RAM • Pagefile.sys and Hiberfil.sys files • Use of software • Messengers • Histories of visited websites, viewed videos, use of software, opened docs, etc • Jumplists • Recycle bin • Temp files • Log files • Invalid Prefetch entries • Indexing service • ThumbCaches, Thumbs.db • Residual traces of deleted files • Free space • File table (MFT or FAT) • INDEX attributes in MFT • USN Journal, etc 1- Detection of residual traces in free space Visualization of residual traces of old files remaining in free space 2- Smart cleanup of free space Cleanup of residual traces in free space areas needing a reset to zero We assure no useless cleanups. Areas already reset to zero are not cleaned which can speed up cleanup by 2x to 100x. Cleanup runs faster after each run. 3- File table cleanup Cleanup of residual traces in file tables, not only in MFT but in FAT as well Additional cleanup of INDEX attributes in MFT 4- Smart overwriting Recognition of type of storage medium of your storage device : magnetic disk, SSD, etc Adaptation of overwriting algorithms to storage medium 5- Smart cleanup of Jumplists Cleanup of your Jumplists without deleting your pinned items/ websites which are preserved 6- Smart cleanup of Prefetch Removing of invalid Prefetch entries. Old valid entries are preserved. 7- Deletion of USB history Deletion of remaining traces of disconnected device (name, date, etc) 8- Scan and cleanup of Pagefile.sys / Hiberfil.sys content Visualization of Pagefile.sys / Hiberfil.sys content Pagefile.sys cleanup options ... |
 |
12,809 | Jun 26, 2025 Goversoft LLC  |
|
| Program Blocker Program Blocker Program Blocker is a portable TWC freeware that lets you block any desktop application. You can block it with a password or simply make it non-functional on your computer. The program is completely based on the idea of simply blocking applications from running, without taking any chances with the system, as a result of which the program does not make any changes in the registry and operates independently of the system. Features: Password protection Block applications Task manager Hidden mode |
 |
8,370 | Mar 20, 2014 The Windows Club |
|
| Proxy Mask - Proxy Switcher 3.4.4 Proxy Mask - Proxy Switcher 3.4.4 Proxy Checker and Switcher allow access to blocked websites Access blocked websites, and you can watch blocked YouTube videos such as This Video Is Not Available In Your Country (by changing your IP to different country), hide your IP address, surf anonymously without a trace on the Internet. You can access many of blocked websites without using proxy with Smart DNS Changer Free. Supports HTTP and HTTPS proxy servers You can define different proxy setting for different processes at the same time At least several hundred working proxies (always) Updates Working proxy list automatically Supports all windows (XP to windows 10, 32 and 64-bits) When to use Proxy Mask or Proxy Switcher Accessing blocked websites: Your ISP (Internet Service Provider) may block some websites. Normally, network adapters on your computer, uses your IPS DNS server, and most of blocked websites blocking by your ISP's DNS server. This type of restrictions can be bypassed by changing DNS server settings of network adapters. You can use the Smart DNS Changer Free to change your DNS settings. Some websites blocks by their IP addresses and this type of restriction cannot be bypassed by changing DNS server settings. In this case you should use Proxy Mask (Proxy Switcher) to access blocked websites. Bypassing websites region (country) restrictions: Some videos on YouTube cannot be watched from some countries (because of publisher restriction or copyright etc.), In this case YouTube shows text message on video player like This Video Is Not Available In Your Country. To bypass such restrictions you can use Proxy Mask (Proxy Switcher) to access restricted contents by changing your IP address to different country (by using Elite proxy ... |
 |
6,454 | Feb 25, 2017 Rentanadviser.com  |
|
| Psiphon v183.20241101 Psiphon v183.20241101 The Psiphon Circumvention System is a relay-based Internet censorship circumventer. The system consists of a client application, which configures a users computer to direct Internet traffic; and a set of servers, which proxy client traffic to the Internet. As long as a client can connect to a Psiphon server, it can access Internet services that may be blocked to the user via direct connection. Features: • Automatic discovery. Psiphon clients ship with a set of known Psiphon servers to connect to. Over time, clients discover additional servers that are added to a backup server list. As older servers become blocked, each client will have a reserve list of new servers to draw from as it reconnects. To ensure that an adversary cannot enumerate and block a large number of servers, the Psiphon system takes special measures to control how many servers may be discovered by a single client. • Cross-platform. Psiphon clients are available for Windows, Android, and iOS. • Zero install. Psiphon is delivered to users as a minimal footprint, zero install application that can be downloaded from any webpage, file sharing site or shared by e-mail and passed around on a USB key. We keep the file size small and avoid the overhead of having to install an application. • Custom branding. Psiphon offers a flexible sponsorship system which includes sponsor-branded clients. Dynamic branding includes graphics and text on the client UI; and a region-specific dynamic homepage mechanism that allows a different home page to open depending on where in the world the client is run. • Chain of trust. Each client instance may be digitally signed to certify its authenticity. Embedded server certificates certify that Psiphon servers the client connects ... |
 |
5,545 | Nov 01, 2024 Psiphon Inc.  |
|
| QuickStego 1.2.1 QuickStego 1.2.1 Free Steganography Software QuickStego lets you hide text in pictures so that only other users of QuickStego can retrieve and read the hidden secret messages. Once text is hidden in an image the saved picture is still a 'picture', it will load just like any other image and appear as it did before. The image can be saved, emailed, uploaded to the web What is Steganography? Steganography is the science of writing hidden messages in such a way that no one apart from the sender and intended recipient even realizes there is a hidden message. An Example of Image Steganography ... A perfectly innocuous picture? Nothing special about it? Well if you download QuickStego and copy the above image into the system, you will see that there is a lot of 'secret text' hidden in this image. Try it and see! Or if you can't wait, move further down this page for a screen shot of what will be revealed ... QuickStego - Screenshots Load the image from above into QuickStego and the secret text that was hidden in the photograph is revealed: System Requirements & FAQ * Operating System - Windows XP or Vista or 7. * Display - 32 bit color depth required * Image Types that can be opened - .jpg/.jpeg, .gif, or .bmp formats * Saved Hidden Text Images - .bmp format only * Approximately 2MB of free hard disk space (plus extra space for any images) |
 |
5,271 | Mar 31, 2017 Cybernescence ltd. 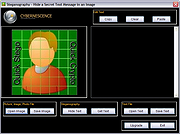 |
|
| Radmin VPN v1.1.4288.10 Radmin VPN v1.1.4288.10 Radmin VPN is a free and easy-to-use software product to create virtual private network (VPN). The program allows users to establish a secure connection between computers over the Internet as if they were connected over a LAN. Why Radmin VPN? Security Provides you with a secure VPN tunnel. Encryption keeps your connection safe. High speed The connection speed is up to 100Mbps. Reliability Radmin VPN does not malfunction after months of continuous operation. Ease-of-use Easy to set-up, easy to manage for both - IT Pros and home techs. Use Cases Connect distributed teams together Easily connect distributed teams together, create one cohesive network no matter how far you are located from each other. Radmin VPN allows you to connect to remote PCs even behind firewalls you don’t control. Work remotely Thanks to the integration with Radmin remote control software, Radmin VPN allows you to securely access and work at your remote computer from anywhere, whether from home, hotel or airport. Your network resources – files, apps, and emails are just a click away wherever you go. Play network games over the Internet Play your favourite LAN games with your friends over the Internet. Free Radmin VPN does not limit the number of gamers. Thanks to high speed of Radmin VPN you won’t see the difference – you will play your favourite games as if you were playing in the LAN. Click here to visit the author's website. |
 |
5,680 | Apr 04, 2021 Famatech  |
|
| SafeIP 2.0.0.2595 SafeIP 2.0.0.2595 Hide your IP address and protect your online identity with SafeIP by hiding your IP from websites, email, games, and more. Features: Encrypt all your Internet traffic with a private proxy, either browsing at home or on public WiFi hotspots Choose the anonymous IP location closest to you for the fastest connection speeds SafeIP can be used completely free for unlimited use, without advertisements and never expires |
 |
9,182 | Jan 19, 2014 SafeIP, LLC. |
|
| ScrambleOnClick v1.7.7.0 ScrambleOnClick v1.7.7.0 An easy to use program that allows you to quickly encrypt/decrypt a selectable section of text within any document that you wish to keep secure and private. ScrambleOnClick works with email programs, and any Windows program where text is editable. For example text editors, word processing documents, spreadsheets, and many more. Benefits • Encrypt any text quickly and easily using strong encryption. • Decrypt text which has been encrypted using ScrambleOnClick. • View the clipboard at any time. • Securely wipe the clipboard with a simple key stroke. • Use with any email program as well as document programs like Word. • Encrypt and Decrypt using either a keyboard shortcut, or via the ScrambleOnClick Tray menu. • Use the keyboard or ScrambleOnClick menu to encrypt or decrypt text. • An Encryption Keys Manager allows you to define different keys for friends, colleagues, business etc. • Start with Windows Logon. • The Master Password protects other people from using the Encryption Keys that you define. • Option to split the encrypted text into definable lengths of text. Great for email. • The keyboard Ctrl-C-C key press delay can be changed from 500 ms (half a second) to a second. • Password hints help you remember the password you have saved. • Complete help file, online forums, knowledge base, and FAQs. Using ScrambleOnClick ScrambleOnClick provides two methods for scrambling and unscrambling text. The first uses the keyboard, the second uses the ScrambleOnClick menu available by right clicking the ScrambleOnClick Tray icon: Note there is an option for whether the keyboard is used to control scrambling. You may for example prefer not to scramble the clipboard contents each time the key combination "Ctrl" "C" "C" is used. You may also be running a program that uses the "Ctrl" "C" "C" combination which may conflict with using the keyboard controls in this way. Uncheck the box "Use Ctrl-C-C combination for scrambling/unscrambling" to prevent ... |
 |
2,114 | Jul 05, 2024 2BrightSparks Pte Ltd 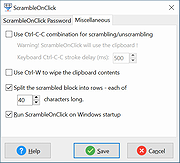 |
|
| ScreenBlur v2.1.0 ScreenBlur v2.1.0 Screen locker for Windows. Temporarily lock or hide the Windows desktop (and keyboard) from snooping humans or prancing cats. Use the supplied image for the lock screen or use your own image. Features Can lock PC after a while and unlock the next day. Weekly schedule. Blackout desktop, turn off the screen, put PC to sleep using hotkeys. To protect your data use Windows Lock and BitLocker features as well. Supported operating systems: Windows 7,8,10,11 Changes: v2.1.0 - can swap PgUp/PgDn keys with Arrow keys (see F1 help). - fixes and improvements. Click here to visit the author's website. |
 |
145 | Sep 24, 2024 InDeep Software  |
|
| Secret Disk Free v2021.04 Secret Disk Free v2021.04 Creates additional hidden disk protected with a password Creating a secure place for sensitive files has never been easier than with our software Secret Disk. Within a few clicks, you can create a password-protected additional hard disk to store, hide, and lock files. The software also enables you to set several automation scenarios to make usage very convenient for you. If you need more than one secret disk, that can easily be handled by our software. Easy And Fast Creation With our software, you won't need to format your hard disk or change anything to the boot sector. It can make a new disk automatically and quickly while providing you with plenty of set-up options. You can choose to make the disk invisible, including the contents in it, and keep it password-protected. The Secret Disk works similarly to a standard hard disk and provides compatibility with any other software. To top it all off, you can choose your disk letter. Clever in Any Situation In the case of a power outage or fatal error of your Windows OS, your secret disk will automatically lock and become invisible as the information related to the disk instance is stored in the virtual memory. The Secret Disk does not encrypt your files, but it does limit access to them by allowing you to keep them password protected. The software ties together your files with the virtual disk to provide ample security to keep your files secure. Regular updates Just as technology keeps advancing, we will too. As more gets added or enhanced, we will send out updates to keep you up-to-date. The update process is automatic and in the background, so you won't ever need to worry. Trust and Awards Our software has received multiple awards from world-known rating agencies and bloggers. We pride ourselves ... |
 |
6,595 | Jul 12, 2021 PrivacyRoot  |
|
| Secret v1.0 Secret v1.0 SECRET is a command line encryption tool for Windows, MacOS and Linux. It comes as a standalone binary file which does not need installation. Copy the file to some path and run it from there. SECRET is very easy to use and can handle encryption of very large files. It supports all file types. SECRET also allows you to encrypt directories with ease, even recursively. Note that on Linux you need to give SECRET binary execution permissions before you can use it. Examples These examples are for Windows, on MacOS or on Linux they are the same except the SECRET binary does not have .exe extension. Note that SECRET has built-in help function which you can call by using SECRET.exe –help. File encryption: SECRET.exe encrypt -f ”/path/to/some/file.txt” –delete This example would encrypt file.txt , rename it to file.txt.secret and after the enc ryption delete the original file (file.txt) File decryption: SECRET.exe decrypt -f ”/path/to/some/file.txt.secret” –delete This example would de crypt file.txt .secret , rename it to file.txt and after the enc ryption delete the original encrypted file (file.txt .sec ret Directory encryption: SECRET.exe encrypt -d ”/path/to/some/test-dir” --recursive Here we’re encrypting directory test-dir with –recursive flag. So all directories under test-dir will be encrypted too. How SECRET works is that it goes through all the files in the directory and encrypting them one by one. Without –delete flag SECRET will leave original files intact, useful for testing and for cases where you do want to keep the original files too. Decrypting directory would work the same way but calling decrypt instead of encrypt subcommand. This download is for the Windows version. If you need the MacOS version, download here If you need the Linux version, download here. Click here to visit the author's website. |
 |
3,429 | Jun 04, 2020 Niko Rosvall  |
|
| SecretFolder 3.0.0.0 SecretFolder 3.0.0.0 SecretFolder is a security tool to hide and lock your sensitive folder out from the other users. It provides immediate data protection (protect and unprotect commands are executed in no time). Features: Free to use at both home and in the office Support for 64-bit Windows. NTFS, FAT32, exFAT and FAT volumes are supported. Unlimited number of folders can be protected at the same time. No limits on the size of protected data. No file system structure modifications will occur. Protected uninstall. When you create a secret folder, using your own password, you can manage folder. CMD command will not be able to access the folders. |
 |
7,897 | Jun 05, 2014 Oh!Soft |
|
| SecureMyBit v2.3 SecureMyBit v2.3 SecureMyBit is a free, portable, and light application , which allows to encrypt any type of file with password (using AES 256 Bit encryption method) and then, decrypt them. SecureMyBit provide, for this purpose, also a secure and strong random password generator, which can generate passwords, as long as you want. Another utility of SecureMyBit is the Secure File Shredder, which can delete a file permanently with an irreversible shredding operation. Our software provides also an utility which can validate the strength of user’s passwords; and a System Specs utility, which can tell us all the informations about our computer. SecureMyBit provides also, in addition, a secure virtual keyboard which doesn’t produce any keystroke, so this guarantee a protection while entering your password. Finally, you can also get information about your files: hashes, file type, file attributes, etc. and compress your text easily and fast! When you encrypt your file(s) or folder(s) the Smart Monitor will check in real-time if they are modified, renamed or changed/deleted. Key Features Secure File Password Encryption (AES 256 Bit) Secure File Shredder System Specs Password Generator File Info Viewer Text Compressor Smart Monitor Compatibility Windows Vista Windows 7 Windows 8/8.1 Windows 10 Special Requirement: Microsoft .NET Framework 4.5 Languages: English F.A.Q. -Why SecureMyBit is detected by my antivirus/antimalware? We want to specify that this is surely a false positive. SecureMyBit is a clean file. Do I need to install SecureMyBit? No, SecureMyBit is avalaible only in “portable” version, so it doesn’t require any installation. -Is SecureMyBit free? Yes, SecureMyBit is absolutely FREE and WITHOUT advertisements! -Does SecureMyBit protect files against ransomware? Well, SecureMyBit provides surely additional protection to the encrypted files, against ransomware, also because the extension of the encrypted files are encoded. This doesn’t mean SecureMyBit protects files against all type of ransomware. -Why SecureMyBit gives me an error message when I ... |
 |
5,328 | May 19, 2019 JM Security  |
|
| Shellbag Analyzer and Cleaner v1.30 Shellbag Analyzer and Cleaner v1.30 Free, portable program to analyze and clean Windows Shellbag information. ShellBags keys may contain information concerning your past activities: 1. the names and paths of folders you opened even if the folder has been deleted ! 2. detailed timestamp information, creation time, modification time, access time That's really a privacy issue. Supports: Windows XP, Vista, 7, 8, 8.1, 10, 11 Changes: v1.30 (29 August 2021) + Improved scan Click here to visit the author's website. |
 |
3,614 | Dec 06, 2021 Goversoft 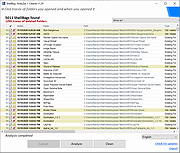 |
|
| SilentRun v1.0 SilentRun v1.0 Run Programs Hidden and Silently in the Background on Windows. SilentRun is a small and handy Windows system software tool that can easily let you run multiple programs silently in the background. It can hide program windows and interfaces, and increase or decrease the priority of background processes. For some programs with sound output, SilentRun can also mute the program then run it silently in the background. SilentRun has a simple interface and is very easy to use. To run a program silently, simply drag the selection box in the upper left corner of the SilentRun window to the title bar or the window of the program that needs to be run silently. You will see the program is selected by SilentRun and a thumbnail of the program would be displayed in the preview area. (Some applications use the non-standard GUI and that might be displayed as a solid black square). After that, you can select the background silent running priority (the default is the "Normal" priority) under the preview area, and set whether to mute the sound output, and finally click the "Hide It" button. You can repeat the above steps to let multiple programs run silently in the background. Quitting SilentRun will not close these programs that run silently in the background. You can open SilentRun at any time, restore these programs in the "Silent Processes "list on the left, make them visible and run in the foreground, or close and kill processes directly. In addition to the GUI visual interface, SilentRun also provides the command line mode, which allows you to run other visual programs through the command line. It automatically hides the interface of these programs and places them in the background to run silently. The command line mode also supports providing parameters to invoked ... |
 |
1,350 | Jun 20, 2023 AutoClose  |
|
| SlunkCrypt v1.3.2 SlunkCrypt v1.3.2 An experimental cross-platform cryptography library. SlunkCrypt is an experimental cross-platform cryptography library and command-line tool. A fully-featured GUI is provided for the Windows platform. Encryption algorithm The SlunkCrypt algorithm is based on core concepts of the well-known Enigma machine but with numerous improvements, largely inspired by R. Anderson’s “A Modern Rotor Machine”: The original Enigma machine had only three (or, in some models, four) rotors, plus a static “reflector” wheel. In SlunkCrypt, we uses 256 simulated rotors for an improved security. Furthermore, the original Enigma machine supported only 26 distinct symbols, i.e. the letters A to Z. In SlunkCrypt, we use 256 distinct symbols, i.e. the byte values 0x00 to 0xFF, which allows the encryption (and decryption) of arbitrary streams of bytes, rather than just plain text. Of course, SlunkCrypt can encrypt (and decrypt) text files as well. In the original Enigma machine, the signal passes through the rotors twice, once in forward direction and then again in backwards direction – thus the “reflector” wheel. This way, the Enigma’s encryption was made involutory, i.e. encryption and decryption were the same operation. While this was highly convenient, it also severely weakened the cryptographic strength of the Enigma machine, because the number of possible permutations was reduced drastically! This is one of the main reasons why the Enigma machine eventually was defeated. In SlunkCrypt, the signal passes through the simulated rotors just once, in order to maximize the number of possible permutations. This eliminates the most important known weakness of the Enigma machine. Obviously, in SlunkCrypt, separate “modes” for encryption and decryption need to be provided, since encryption and decryption no longer are the same operation. In the original Enigma machine, the rightmost rotor was moved, by one step, after every symbol. Meanwhile, all ... |
 |
1,965 | Nov 18, 2024 LoRd MuldeR  |
|
| Spybot Anti-Beacon for Windows 10 1.6 Spybot Anti-Beacon for Windows 10 1.6 Spybot Anti-Beacon for Windows 10 is a small utility designed to block and stop the various tracking (aka telemetry) issues that come with Windows 10. Seeing the bunch of incomplete or broken scripts to disable tracking in Windows 10, and the tools that install adware or worse in exchange for their function, we wrapped disabling tracking up in a small tool that’s free and clean. With the upcoming news about telemetry in Windows 7 and 8.1, Spybot Anti-Beacon has added support for those as well. Changelog: Spybot Anti-Beacon 1.6 now available December 5th, 2016 Many thanks for all the patience waiting for an update to Spybot Anti-Beacon! We spent a lot of time working on Spybot 3. And now that Spybot Anti-Beacon will also be integrated into Spybot 3, we found time to continue work. Today’s update to Anti-Beacon 1.6 will add two new immunizers and a few new blocked hosts. More updates are already pending since we’re actively working on this feature again (including a new look, but mostly focused on function of course)! Spybot Anti-Beacon 1.6 can be downloaded from here. Updates: Additional Telemetry Immunization Categories Additional Blocked Hosts Fixes: Immunization of Office 13/16 Telemetry Scheduled Tasks and Options is possible even if Microsoft Office is not installed (previously they appeared to immunize correctly, but the immunization could not be undone in Anti-Beacon) Don’t forget to always run Spybot Anti-Beacon as an administrator by right-clicking the downloaded installer, and choosing the option to “Run as administrator”. This will ensure that Anti-Beacon has the permissions it needs to function correctly. |
 |
6,558 | Dec 06, 2016 Safer-Networking Limited |
|
| SpyDetectFree 32bit 1.0 SpyDetectFree 32bit 1.0 SpyDetectFree is a FREE tool mainly intended for detecting processes on your computer that might be spying on your keyboard or in other word for detecting processes that might be recording your keystrokes. Just in one click get answers for your questions: -Are my keystrokes being recorded? -Is there any spyware on my computer? -Am I being spied on? -Is my computer being spied on? Why Free? Because NesterSoft Inc. supports Respectful Employee Monitoring Only without any spying functionality. Performance monitoring only. Strictly. SpyDetectFree is a purely free software: no requirements for using it, there are no fees, or hidden functionality. Digital Signature SpyDetectFree is digitally signed by NesterSoft Inc. Our signed software is completely safe to use: there are no bundles, no advertisement, no viruses, no toolbars or other addons. How To Use Easy! Run -> Click the Button -> Get Results No installation is required. To use SpyDetectFree simply run it and click “Check Now” button. The whole process takes just 1 minute: Reading Results Results answer two major questions: 1. Am I Being Spied On? To answer this question, SpyDetectFree is searching if there are any processes on your computer that have installed HOOKS on your keyboard. This is how SpyDetectFree detects processes that might be recording your keystrokes, as using hooks on keyboard is the most common practice when recording keystrokes pressed. 2. Am I Being Monitored? This result answers wether there are any processes that might be monitoring your computer. This result is based on the most common practices among monitoring software present on the market. Positive result means that there are some processes on your computer that periodically check on your windows’ captions. It does not necessarily mean that your computer is being monitored, but even if it is being monitored, then only applications and website usage can be recorded, not keystrokes or content. So, no personal information can be captured. Why ... |
 |
6,123 | Dec 07, 2015 NesterSoft Inc. 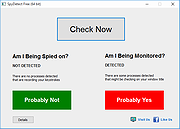 |
|
| SpyDetectFree 64bit 1.0 SpyDetectFree 64bit 1.0 SpyDetectFree is a FREE tool mainly intended for detecting processes on your computer that might be spying on your keyboard or in other word for detecting processes that might be recording your keystrokes. Just in one click get answers for your questions: -Are my keystrokes being recorded? -Is there any spyware on my computer? -Am I being spied on? -Is my computer being spied on? Why Free? Because NesterSoft Inc. supports Respectful Employee Monitoring Only without any spying functionality. Performance monitoring only. Strictly. SpyDetectFree is a purely free software: no requirements for using it, there are no fees, or hidden functionality. Digital Signature SpyDetectFree is digitally signed by NesterSoft Inc. Our signed software is completely safe to use: there are no bundles, no advertisement, no viruses, no toolbars or other addons. How To Use Easy! Run -> Click the Button -> Get Results No installation is required. To use SpyDetectFree simply run it and click “Check Now” button. The whole process takes just 1 minute: Reading Results Results answer two major questions: 1. Am I Being Spied On? To answer this question, SpyDetectFree is searching if there are any processes on your computer that have installed HOOKS on your keyboard. This is how SpyDetectFree detects processes that might be recording your keystrokes, as using hooks on keyboard is the most common practice when recording keystrokes pressed. 2. Am I Being Monitored? This result answers wether there are any processes that might be monitoring your computer. This result is based on the most common practices among monitoring software present on the market. Positive result means that there are some processes on your computer that periodically check on your windows’ captions. It does not necessarily mean that your computer is being monitored, but even if it is being monitored, then only applications and website usage can be recorded, not keystrokes or content. So, no personal information can be captured. Why ... |
 |
6,245 | Dec 07, 2015 NesterSoft Inc.  |
|
| Terms of Service; Didn't Read v2.0.0 Terms of Service; Didn't Read v2.0.0 “I have read and agree to the Terms” is the biggest lie on the web. Tosdr.org aim to fixs that. We are a user rights initiative to rate and label website terms and privacy policies, from very good Class A to very bad Class E. "Terms of service are often too long to read, but it's important to understand what's in them. Your rights online depend on them. We hope that our ratings can help you get informed about your rights." - Abdullah Diaa, Hugo, Michiel de Jong Install the browser extensions to get instant information about the terms and privacy policies of websites you browse. Pick the browser you are using below to install the extension: This download is for the Google Chrome extension. If you need the Mozilla Firefox add-on, download here. If you need the Safari extension, download here. If you need the Opera add-on, download here. Internet Explorer: coming soon Click here to visit the author's website. |
 |
6,152 | Aug 06, 2024 The www.tosdr.org Initiative  |
|
| Tor Browser v14.0.7 Tor Browser v14.0.7 Protect yourself against tracking, surveillance, and censorship. • Browse Privately. • Explore Freely. • Defend yourself against tracking and surveillance. • Circumvent censorship. Tor Team mission: To advance human rights and freedoms by creating and deploying free and open source anonymity and privacy technologies, supporting their unrestricted availability and use, and furthering their scientific and popular understanding. BLOCK TRACKERS Tor Browser isolates each website you visit so third-party trackers and ads can't follow you. Any cookies automatically clear when you're done browsing. So will your browsing history. DEFEND AGAINST SURVEILLANCE Tor Browser prevents someone watching your connection from knowing what websites you visit. All anyone monitoring your browsing habits can see is that you're using Tor. RESIST FINGERPRINTING Tor Browser aims to make all users look the same, making it difficult for you to be fingerprinted based on your browser and device information. MULTI-LAYERED ENCRYPTION Your traffic is relayed and encrypted three times as it passes over the Tor network. The network is comprised of thousands of volunteer-run servers known as Tor relays. BROWSE FREELY With Tor Browser, you are free to access sites your home network may have blocked. Changes: Read the latest release announcements This download is for the Windows 64bit version (very bottom of page). All other download assets are below: Windows: tor-browser-windows-i686-portable-14.0.7.exe (32bit) MacOS: tor-browser-macos-14.0.7.dmg Linux: tor-browser-linux-x86_64-14.0.tar.xz tor-browser-linux-i686-14.0.tar.xz Android: tor-browser-android-aarch64-14.0.7.apk tor-browser-android-armv7-14.0.7.apk tor-browser-android-x86_64-14.0.7.apk tor-browser-android-x86-14.0.7.apk Google Play Store Click here to visit the author's website. |
 |
5,964 | Mar 16, 2025 The Tor Project  |
|
| USB Raptor v0.18.84 USB Raptor v0.18.84 Turn any USB flash drive to a computer lock and unlock key! USB Raptor can lock the system once a specific USB drive is removed from the computer and unlock when the drive is plugged in again to any USB port. The utility checks constantly the USB drives for the presence of a specific unlock file with encrypted content. If this specific file is found the computer stays unlocked otherwise the computer locks. To release the system lock user must plug the USB with the file in any USB port. Alternative the user can enable (or disable) two additional ways to unlock the system such is network messaging or password. Features • Automated USB lock and unlock function • Lock file contents are encrypted • Password to override lock (can be enabled by user) • Network command to override lock (can enabled by user) • USB drive serial number check (can be enabled by user) • Unique key for each system (can be enabled by user) • Status report function Features Automated Windows lock/unlock with the use of common USB flash drives Compatible with all types of USB flash drives Robust design Easy to setup and use High security option to verify the serial number of the flash drive Various alternative unlock methods Supports LAN lockdown (and unlock) function Synchronized lock and unlock on LAN for multiple PCs Status report over internet and LAN Supports serial command integration (beta stage) Tray icon based application Option to delay and cancel the lock, to avoid unwanted locks Windows 10, Windows 7, Windows 8 and Windows XP compatible Multi screen ... |
 |
6,314 | Sep 13, 2021 Nikos Georgousis  |
|
| VeraCrypt v1.26.24 VeraCrypt v1.26.24 A free open source disk encryption software for Windows, Mac OSX and Linux. based on TrueCrypt. Features: • Creates a virtual encrypted disk within a file and mounts it as a real disk. • Encrypts an entire partition or storage device such as USB flash drive or hard drive. • Encrypts a partition or drive where Windows is installed (pre-boot authentication). • Encryption is automatic, real-time(on-the-fly) and transparent. • Parallelization and pipelining allow data to be read and written as fast as if the drive was not encrypted. • Encryption can be hardware-accelerated on modern processors. • Provides plausible deniability, in case an adversary forces you to reveal the password: Hidden volume (steganography) and hidden operating system. • More information about the features of VeraCrypt may be found in the documentation. Changes: v1.26.24 May 30th, 2025 All OSes: Fix whirlpool implementation for big-endian platforms (GH #1529). Rename "Dismount All" to "Unmount All" in UI. Use ALT+u as new accelerator key instead of ALT+s Add contributed Chinese and Russian CHM documentation. Update translations. Windows: Implemented screen protection against screenshots and screen recording, enabled by default. This feature can be disabled during installation or via the Performance/Driver Configuration settings. Added checkboxes to the MSI installer to control memory protection and screen protection features. ... |
 |
7,145 | Jun 03, 2025 IDRIX 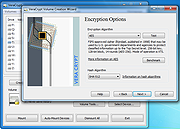 |
|
| W10Privacy v5.1.0.2 W10Privacy v5.1.0.2 Free tool to easily find and change privacy settings in Windows 10 and Windows 11. From the author: The by default highly questionable set options concerning privacy and data protection in Windows 10 brought me to the idea to develop this program. Microsoft generously enables everybody to change the concerning settings, but hides them in countless menus, where a normal user does not want to search for! The program should therefore be a help, to display the available settings relatively clearly and to set the desired options if necessary. The primary focus is on settings for Windows 10/11 and its apps (for example the new browser "Edge"). The program will be expanded gradually, if possible and available, with the corresponding Windows 8.1 features in the future. W10Privacy is certainly no programming masterpiece, but it fulfills my intended purpose. The software is still in an early development phase, requests are welcome and may be included in future releases! -Bernd Schuster This program may trigger anti-virus warnings since it changes core Windows settings.. These are false warnings. This program contains no viruses or malware. Read author's statement here. Changes: v5.1.0.2 (19.12.2024) - Minor adjustments for Windows 11 24H2 - Adding another setting for the "Privacy" area Instructions: https://www.w10privacy.de/english-home/instructions-1/ All Screenshots (download is at the bottom... we promise): Click here to visit the author's website. |
 |
6,824 | Dec 19, 2024 Bernd Schuster 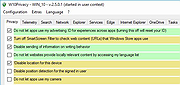 |
|
| WebCam On-Off v1.4 WebCam On-Off v1.4 Webcams allow us to stay in touch with family and friends, or perhaps record and stream video from your computer to the internet or to a file. When not in use , you may wish to disable your webcam to ensure it is not making unwanted recordings. Malware can take over webcams, so there is potential for spying. Hackers can utilize trojan-horse attacks, enabling them to take control of your webcam, allowing them to record you or take pictures of you without your knowledge. If you’re a parent, you may also wish to disable your webcam for safety reasons. Instant messengers and websites that utilize video aren’t always safe for children, thus disabling your webcam may be the best course of action. If the camera is external, you could always unplug it and hide it, but this can become tiresome if you are frequently in need of it. And what if, as on most laptops, you have a built in camera? The Washington Post highlighted an unnerving study published at Johns Hopkins University which found that a laptop webcam can function in relative secrecy – a slightly more subtle Eye of Sauron, if you will. Webcam spying, particularly the variant that involves disabling LED indicator lights, takes quite a bit of effort, but the practice isn’t limited to the realm of academics. The FBI has publicly acknowledged its ability to employ such techniques when investigating criminal activity. As you can see, disabling your webcam completely is the safest way to protect your privacy. Because of this, we have created “Webcam On-Off” which is both portable and freeware. With it you can easily disable or enable your webcam. Don’t let your home become someone else’s reality TV! What is new on version 1.4 (Friday 4 December 2020) 1.[Fixed] – WebCam On-Off Doesn’t Work on ... |
 |
6,543 | Dec 07, 2020 Sordum.org  |
|
OlderGeeks.com Copyright (c) 2025