 |
AllThreadsView v1.00 32bit
AllThreadsView v1.00 32bit
AllThreadsView is a simple tool for Windows that displays a list of all running threads from all processes on your system in one table. For every thread, the following information is displayed: Thread ID, Creation Time, Kernel Time, User Time, Duration, Start Address, Priority, Base Priority, Context Switch Count, Context Switch Change (Since the last refresh), Wait Reason, Process ID, Process Path.
System Requirements
This tool works on any version of Windows, starting from Windows XP and up to Windows 10. Both 32-bit and 64-bit versions of Windows are supported. On Windows Vista and later, if you want to view the full path of system processes , you have to run AllThreadsView as Administrator.
Start Using AllThreadsView
This utility doesn't require any installation process or additional DLL files. In order to start using it, simply run the executable file - AllThreadsView.exe
After running AllThreadsView, the main window displays the list of all threads running on your system and the list is automatically refreshed. If you want to view only the active threads (Threads with change in the Context Switch Count), simply turn on the 'Show Only Active Threads' option.
Command-Line Options
/stext <Filename> Save the threads list into a simple text file.
/stab <Filename> Save the threads list into a tab-delimited text file.
/scomma <Filename> Save the threads list into a comma-delimited text file (csv).
/shtml <Filename> Save the threads list into HTML file (Horizontal).
/sverhtml <Filename> Save the threads list into HTML file (Vertical).
/sxml <Filename> Save the threads list into XML file.
/sjson <Filename> Save the threads list into JSON file.
Translating AllThreadsView to other languages
In order to translate AllThreadsView to other language, follow the instructions below:
Run AllThreadsView with /savelangfile parameter:
AllThreadsView.exe /savelangfile
A file named AllThreadsView_lng.ini will be created in the folder of AllThreadsView utility.
... |
 |
3,907 |
Jan 06, 2020
Nir Sofer 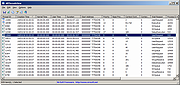 |
 |
AllThreadsView v1.00 64bit
AllThreadsView v1.00 64bit
AllThreadsView is a simple tool for Windows that displays a list of all running threads from all processes on your system in one table. For every thread, the following information is displayed: Thread ID, Creation Time, Kernel Time, User Time, Duration, Start Address, Priority, Base Priority, Context Switch Count, Context Switch Change (Since the last refresh), Wait Reason, Process ID, Process Path.
System Requirements
This tool works on any version of Windows, starting from Windows XP and up to Windows 10. Both 32-bit and 64-bit versions of Windows are supported. On Windows Vista and later, if you want to view the full path of system processes , you have to run AllThreadsView as Administrator.
Start Using AllThreadsView
This utility doesn't require any installation process or additional DLL files. In order to start using it, simply run the executable file - AllThreadsView.exe
After running AllThreadsView, the main window displays the list of all threads running on your system and the list is automatically refreshed. If you want to view only the active threads (Threads with change in the Context Switch Count), simply turn on the 'Show Only Active Threads' option.
Command-Line Options
/stext <Filename> Save the threads list into a simple text file.
/stab <Filename> Save the threads list into a tab-delimited text file.
/scomma <Filename> Save the threads list into a comma-delimited text file (csv).
/shtml <Filename> Save the threads list into HTML file (Horizontal).
/sverhtml <Filename> Save the threads list into HTML file (Vertical).
/sxml <Filename> Save the threads list into XML file.
/sjson <Filename> Save the threads list into JSON file.
Translating AllThreadsView to other languages
In order to translate AllThreadsView to other language, follow the instructions below:
Run AllThreadsView with /savelangfile parameter:
AllThreadsView.exe /savelangfile
A file named AllThreadsView_lng.ini will be created in the folder of AllThreadsView utility.
... |
 |
3,875 |
Jan 06, 2020
Nir Sofer  |
 |
DDS
DDS
DDS is a program that will scan your computer and create logs that can be used to display various startup, configuration, and file information from your computer. This program is used in security forums to provide a detailed overview of what programs are automatically starting when you start Windows. The program will also display information about the computer that will allow experts to quickly ascertain whether or not malware may be running on your computer.
To use DDS, simply download the executable and save it to your desktop or other location on your computer. You should then double-click on the DDS.com icon to launch the program. DDS will then start to scan your computer and compile the information found into two log files. When DDS has finished it will launch the two Notepad windows that display the contents of these log files. The contents of these log files can then be attached to a reply in virus removal forums so that an expert can analyze them.
|
 |
6,284 |
Nov 13, 2019
sUBs 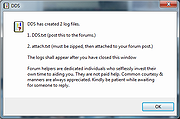 |
 |
Farbar Recovery Scan Tool v19.12.2024.1
Farbar Recovery Scan Tool v19.12.2024.1
A portable application designed to run on Windows 7/8/10/11 in normal or safe mode to diagnose malware issues.
Farbar Recovery Scan Tool, or FRST, is a portable application designed to run on Windows XP, Windows Vista, and Windows 7/8/10/11 in normal or safe mode to diagnose malware issues. It is also possible to run FRST in the Windows Recovery Environment in order to diagnose and fix boot issues.
This program will display detailed information about the Windows Registry loading points, services, driver services, Netsvcs entries, known DLLs, drives, and partition specifications. It will also list some important system files that could be patched by malware.
If you are using Windows XP and have boot issue, the system should boot to the Recovery Environment using a PE Boot CD and then you can run FRST
This program will display detailed information about the Windows Registry loading points, services, driver services, Netsvcs entries, known DLLs, drives, and partition specifications. It will also list some important system files that could be patched by malware.
Note: There are both 32-bit and 64-bit versions of Farbar Recovery Scan Tool available. Please pick the version that matches your operating system's bit type. If you don't know which version matches your system, you may try both of them. Only one of them will run on your system.
Supported operating systems:
Windows XP/Vista/7/8/Windows 10/Windows 11 32-Bit and 64-Bit
This download is for the 64bit version. If you need the 32bit version, download here.
Click here to visit the author's website. |
 |
7,817 |
Dec 19, 2024
Farbar  |
 |
Ghidra v11.2
Ghidra v11.2
A software reverse engineering (SRE) suite of tools developed by NSA's Research Directorate in support of the Cybersecurity mission
SHA-256: a98fe01038fe8791c54b121ede545ea799d26358794d7c2ac09fa3f5054f3cdc
Ghidra Software Reverse Engineering Framework
Ghidra is a software reverse engineering (SRE) framework created and maintained by the National Security Agency Research Directorate. This framework includes a suite of full-featured, high-end software analysis tools that enable users to analyze compiled code on a variety of platforms including Windows, Mac OS, and Linux. Capabilities include disassembly, assembly, decompilation, graphing, and scripting, along with hundreds of other features. Ghidra supports a wide variety of process instruction sets and executable formats and can be run in both user-interactive and automated modes. Users may also develop their own Ghidra plug-in components and/or scripts using Java or Python.
In support of NSA's Cybersecurity mission, Ghidra was built to solve scaling and teaming problems on complex SRE efforts, and to provide a customizable and extensible SRE research platform. NSA has applied Ghidra SRE capabilities to a variety of problems that involve analyzing malicious code and generating deep insights for SRE analysts who seek a better understanding of potential vulnerabilities in networks and systems.
Ghidra Installation Guide
Changes
v11.2 (September 2024)
New Features
Basic Infrastructure. Ghidra now requires JDK 21 to run. (GP-4122)
Build. A Gradle wrapper script is now included at support/gradle/gradlew(.bat) which can be used to perform all Gradle commands without the need for prior Gradle installation. The Gradle wrapper requires an Internet connection to work. Offline Gradle installations on the PATH continue to work the same way as before. (GP-4486, Issue #455)
Debugger. Provided new launchers/features for the traceRMI version of dbgeng, including extended launch options, kernel debugging, and remote process server connections. (GP-4686)
... |
 |
5,130 |
Sep 27, 2024
NSA's Research Directorate  |
 |
HijackThis 2.0.5
HijackThis 2.0.5
HijackThis is a free utility that generates an in depth report of registry and file settings from your computer. HijackThis makes no separation between safe and unsafe settings in its scan results giving you the ability to selectively remove items from your machine. In addition to this scan and remove capability HijackThis comes with several tools useful in manually removing malware from a computer.
IMPORTANT: HijackThis does not determine what is good or bad. Do not make any changes to your computer settings unless you are an expert computer user.
Advanced users can use HijackThis to remove unwanted settings or files.
|
 |
9,177 |
Nov 13, 2019
TrendMicro  |
 |
Mitec Certificate Information v1.0
Mitec Certificate Information v1.0
Tool for extracting and browsing certificates from signed files and certificates files.
It has capability to export displayed certificate to PEM format.
Here are supported file types:
All Portable Executables (e.g. *.exe;*.dll;*.sys;*.ocx;*.acm;*.ax;*.cpl;*.scr;*.drv;*.tsp;*.rll;*.rs;*.tlb)
All Structured Storage files (e.g. *.msi)
All Certificate files (*.pem;*.crt;*.cer;*.p7b;*.p7c;*.der;*.pfx;*.p12)
Target platforms
Windows XP
Windows 2003
Windows Vista
Windows 7
Windows Server 2008
Windows 8
Windows 8.1
Windows Server 2012
Windows Server 2012 R2
Windows 10
Windows Server 2016
Licence
Free to use for private, educational and non-commercial purposes.
Click here to visit the author's website. |
 |
4,070 |
Nov 13, 2019
MiTeC  |
 |
Mitec EXE Explorer v3.7.4
Mitec EXE Explorer v3.7.4
Executable File Explorer for OS/2, NE, PE32, PE32+ and VxD file types.
It enumerates introduced classes, used units and forms for files compiled by Borland compilers.
It contains powerful Resource Viewer that is able to analyze and display all basic resource types and some extra ones as JPEG, PNG, GIF, AVI, REGISTRY.
It contains excellent Type Library viewer that enumerates all objects and creates import interface unit in Object Pascal language. Every type of resource can be saved to file.
EXE Explorer produces text report with all important information about selected file.
Searching capability is also available. It searches all resources that can be interpreted as text.
Here are enumerated structures that are evaluated:
DOS, File, Optional, Rich and CLR headers
CLR Metadata streams
Sections
Directories
Imports
Exports
Resources
ASCII and Unicode Strings
.NET Metadata
Load Config
Debug
Thread Local Storage
Exceptions
Units
Forms
Packages
Classes
Certificates
Package Flags
Version Info
Hexadecimal File Content View
TypeLib Viewer
Form Preview
VirusTotal scan report
Compiler and installer/packer/protector identification
Supported operating systems:
Windows XP
Windows 2003
Windows Vista
Windows 7
Windows Server 2008
Windows 8
Windows 8.1
Windows Server 2012
Windows Server 2012 R2
Windows 10
Windows 11
Windows Server 2016
Windows Server 2019+
Changes:
v3.7.4 17.12.2024
* Exceptions for 64bit fixed
Click ... |
 |
4,180 |
Dec 17, 2024
MiTeC  |
 |
OTL 3.2.69.0
OTL 3.2.69.0
OTL, or OldTimer ListIt, is a tool that is used to diagnose a computer for a possible malware presence and to provide system diagnostics information that can by someone working on a computer. When run, OTL will scan your computer for a variety of information and then generate a report with a tremendous amount of information about your computer's hardware, programs, files, and running environment.
|
 |
10,920 |
Nov 13, 2019
OldTimer  |
 |
PE-sieve v0.3.4
PE-sieve v0.3.4
A tool that helps to detect malware running on the system, as well as to collect the potentially malicious material for further analysis.
Recognizes and dumps variety of implants within the scanned process: replaced/injected PEs, shellcodes, hooks, and other in-memory patches.
Detects inline hooks, Process Hollowing, Process Doppelgδnging, Reflective DLL Injection, etc.
PE-sieve is meant to be a light-weight engine dedicated to scan a single process at the time. It can be built as an EXE or as a DLL. The DLL version exposes a simple API and can be easily integrated with other applications.
Changes:
v0.3.4
2-10-22
In /mignore - removed buffer limit (Details: #99). WARNING: API change)
New param: /threads, enabling scan of the threads' callstack . This is another layer of shellcode detection, allowing to capture "sleeping beacons", and others, decrypted just before the execution.
This download is for the 64bit version. If you need the 32bit version, download here.
Click here to visit the author's website.
|
 |
5,017 |
Feb 11, 2022
Hasherezade 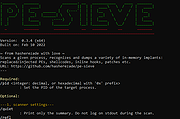 |
 |
PEAnatomist v0.2
PEAnatomist v0.2
Want to look inside PE format?
The free PEAnatomist utility supports almost all known and some undocumented structures inside MS PortableExecutable files (EXE, DLL, SYS and the like), LIB files and object files in COFF, MSVC CxxIL and ExtendedObj formats, and also performs simple analysis of the received data.
File Formats
PE32
PE32+
COFF Object File
MSVC IntermediateLanguage AnonCOFF Object File (MSVC CxxIL)
ExtendedObj (BIGobj)
Objects Library
DBG Stripped Debug Information
MS PDB (Program Database), MSF v7
PE Image Architectures
Intel x86
AMD64
ARM7
ARM7 Thumb
ARM8-64
Intel IA64
Hybrid (CHPE, ARM64X, ARM64EC)
A little of supported headers and data structures
PE: IMAGE_DOS_HEADER, IMAGE_FILE_HEADER, IMAGE_OPTIONAL_HEADER, IMAGE_OPTIONAL_HEADER64 and the DataDirectories List with additional information about some fields
PE: Table of COFF symbols
PE: Sections table, supporting long section names (via symbols table) and entropy calculating
PE: Import table (supports MS-styled names demangling)
PE: Bound Import Table
PE: Delayed Import Table
PE: Export Table with additional info
PE: Resource Table with additional info about different resource types and detailed view for all types
PE: Base Relocation Table. Target address determining and interpretation available for all supporting architectures. It detects imports, delayed imports, exports, tables from loadconfig directory, ANSI and UNICODE strings.
PE: Brief ... |
 |
4,123 |
Nov 09, 2023
RamMerLabs 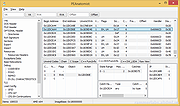 |
 |
PeStudio Standard v9.09
PeStudio Standard v9.09
pestudio is used by many Cyber Emergency Response Teams (CERT) worldwide in order to perform malware initial assessments.
Malicious software often attempts to hide its intents in order to evade early detection and static analysis. In doing so, it often leaves suspicious patterns, unexpected metadata, anomalies and other indicators.
The goal of pestudio is to spot these artifacts in order to ease and accelerate Malware Initial Assessment. The tool uses a powerful parser and a flexible set of configuration files that are used to detect various types of indicators and determine thresholds. Since the file being analyzed is never started, you can inspect unknown or malicious executable file, trojan and ransomware without any risk of infection.
features
pestudio implements a rich set of features that is especially designed to retrieve every single detail of any executable file. Results are checked against the Microsoft specification. Additionally, the content of the file being analyzed is checked against several white and black lists and thresholds.
pestudio can query Antivirus engines hosted by Virustotal. Only the MD5 of the file being analyzed is sent. This feature can be switched ON or OFF using an XML file included with pestudio.
Even a suspicious binary file must interact with the operating system in order to perform its activity.
pestudio retrieves the libraries and the functions referenced. Several XML files are used to blacklist functions (e.g. Registry, Process, Thread, File, etc). Blacklist files can be customized and extended according to your own needs. pestudio brings out the intent and purpose of the application analyzed.
Resources sections are commonly used by malware to host payload.
pestudio detects many embedded file types (e.g. EXE, DLL, SYS, PDF, CAB, ZIP, JAR, etc ). Detected items can be saved to a file, allowing therefore the possibility of further analysis.
The goal of ... |
 |
9,458 |
Dec 27, 2020
Marc Ochsenmeier 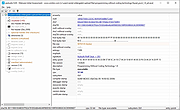 |
 |
PPEE (puppy) v1.13
PPEE (puppy) v1.13
A professional PE file explorer for
reversers, malware researchers and those who want to statically inspect PE files in more details.
Puppy is free and tries to be small, fast, nimble and
friendly as your puppy!
Visual C++ 2015 - 2022 Redistributable Package required for plugins
Features
Puppy is robust against malformed and crafted PE files which makes it handy for reversers, malware researchers and those who want to inspect PE files in more details. All directories in a PE file including Export, Import, Resource, Exception, Certificate(Relies on Windows API), Base Relocation, Debug, TLS, Load Config, Bound Import, IAT, Delay Import and CLR (.Net) are supported.
Both PE32 and PE64 support
Examine Yara rules against opened file
Virustotal and OPSWAT's Metadefender query report
Statically analyze windows native and .Net executables
Robust Parsing of exe, dll, sys, scr, drv, cpl, ocx and more
Parse Rich Header
Parse Safe SEH, Control Flow Guard Functions, Enclave Configuration and Volatile information in load config directory
Edit almost every data structure
Easily dump sections, resources and .Net assembly directories
Entropy and MD5 calculation of the sections and resource items
Entropy, SSDEEP, TLSH, CRC32, ImpHash, MD5, SHA1, SHA256 and Authentihash calculation of the files
View strings including URL, Registry, Suspicious, ... embedded in files
Resolve ordinal to name in imported APIs
Demangle (undecorate) mangled import/export APIs
Detect common resource types
Extract artifacts remained in PE file
... |
 |
5,415 |
Nov 09, 2023
Zaderostam 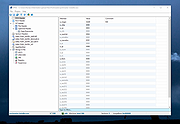 |
 |
Recently Created or Modified Executables Search v2.1.0.2
Recently Created or Modified Executables Search v2.1.0.2
Free tool for incident response.
Inspect executable modules created or modified on your computer during a recent time window (cybersecurity incident time) you select. Returns each module's metadata along with the file's SHA-256 value. Helps discover file artifacts from malware incidents.
More info:
This application may be used at no cost after reading and accepting the built-in EULA. Write access to the Application's working directory is required for the product license file. Uniquely identify executable modules, file artifacts, deposited by System processes and unsafe user activity during a Cybersecurity incident time. Helps associate modules with unsafe or risky applications. Intended target audience: Cybersecurity, Network, Systems Analysts, and similar technical users.
SHA-256: 239fbc57cafdadeec735bf12aa1453b5c8858af16286c8606c8a7d2c7340bc22
Supported operating systems:
Windows 10/11 64bit
Important Notes:
1) This program will not function unless you install Microsoft .NET 6.0. Get it HERE.
2) This program will not function unless you right-click the file and choose to run as an administrator.
3) Once launched, allow the program to finish it's scan operation. This may take a few minutes.
|
 |
3,037 |
May 07, 2024
Steve Chaison Software  |
 |
VirusTotal Scanner v7.5
VirusTotal Scanner v7.5
VirusTotal Scanner is the desktop tool to quickly perform Anti-virus scan using VirusTotal.com
VirusTotal.com is a free online scan service that analyzes suspicious files using 40+ Anti-virus applications. It facilitates the quick detection of viruses, worms, trojans, all kinds of malware and provides reliable results preventing any False Positive cases.
'VirusTotal Scanner' is the desktop tool which helps you to quickly scan your file using VirusTotal without actually uploading the file. It performs direct Hash based scan on VirusTotal thus reducing the time taken to upload the file.
It comes with attractive & user friendly interface making the VirusTotal scanning process simpler and quicker. You can simply right click on your file and start the scan.
VirusTotal Scanner is fully portable tool but also comes with Installer for local installation & un-installation. It works on wide range of platforms starting from Windows XP to new Windows 10 version.
Features
Easily & Quickly perform VirusTotal scan of your file.
Performs Hash based scan without uploading the file.
Right click context menu to launch it directly by simply right clicking on the file.
'Drag & Drop' feature to quickly choose the file
Displays detailed VirusTotal Scan report
Very easy to use with attractive interface
Completely Portable Tool and can be run directly
Includes optional Installer for local Installation & Uninstallation.
Installation & Uninstallation
Though VirusTotalScanner is a Portable tool, it comes with Installer so that you can install it locally on your system for regular usage. It has intuitive setup wizard which guides you through series of steps in completion of installation.
At any point of time, you can uninstall the product using the Uninstaller located at following location (by default)
[Windows 32 bit]
C:\Program ... |
 |
5,377 |
Nov 13, 2019
SecurityXploded  |
 |
VirusTotalUploader v1.0.136
VirusTotalUploader v1.0.136
Open-source desktop uploader for VirusTotal.
To use this program you will need to get a free API key from VirusTotal:
How to get API key
It is really simple! All you need to do is to go to VirusTotal official page, create profile and copy your key.
How to use
It is really easy! Just drag and drop file into the app and voila!
Click here to visit the author's website. |
 |
2,577 |
Aug 24, 2021
Samuel Tulach  |
 |
WinPatrol v35.5.2017.8
WinPatrol v35.5.2017.8
WinPatrol takes snapshot of your critical system resources and alerts you to any changes that may occur without your knowledge. WinPatrol was the pioneer in using a heuristic behavioral approach to detecting attacks and violations of your computing environment. Now, using our "Cloud" technology you can benefit from the experience of other WinPatrol users. WinPatrol continues to be the most powerful system monitor for its small memory footprint.
WinPatrol's easy tabbed interface allows you to explore deep inside your computer without having to be a computer expert. A one-time investment in WinPatrol PLUS provides a unique experience you won't find in any other software.
WinPatrol PLUS is a great investment!
One Time fee includes for ALL future WinPatrol versions.
No Hidden or Reoccurring Subscription Fees.
Single License valid on all your personal desktops and laptops!
No Toolbars or other unwanted software
WinPatrol PLUS is quicker and faster.
Upgrade Now with No Additional Download
What's new in V35.5.2017.8 (May 7, 2017)
Fixed addition of Startup programs to be compatible with recent changes to Windows 10.
Fixed removal of Startup programs to be compatible with recent changes to Windows 10.
Disabled and removed checkbox for Allow PLUS info data collection because recent changes in allowed URL length resulting in no data being returned for customers.
|
 |
9,283 |
Nov 13, 2019
BillP Studios  |




























