|
|

Your download link is at the very bottom of the page... always. |
Processed through Paypal No account required. |
Buy our over-priced crap to help keep things running.










|
|

Your download link is at the very bottom of the page... always. |
Processed through Paypal No account required. |










| File - Download PEAnatomist v0.2 | ||||||||
| Description | ||||||||
|
A plea... Deanna and I have been running this site since 2008 and lately we're seeing a big increase in users (and cost) but a decline in percentage of users who donate. Our ad-free and junkware-free download site only works if everyone chips in to offset the revenue that ads on other sites bring in. Please donate at the bottom of the page. Every little bit helps. Thank you so much. Sincerely, your Older Geeks: Randy and Deanna Always scroll to the bottom of the page for the main download link. We don't believe in fake/misleading download buttons and tricks. The link is always in the same place. PEAnatomist v0.2 Want to look inside PE format? The free PEAnatomist utility supports almost all known and some undocumented structures inside MS PortableExecutable files (EXE, DLL, SYS and the like), LIB files and object files in COFF, MSVC CxxIL and ExtendedObj formats, and also performs simple analysis of the received data. 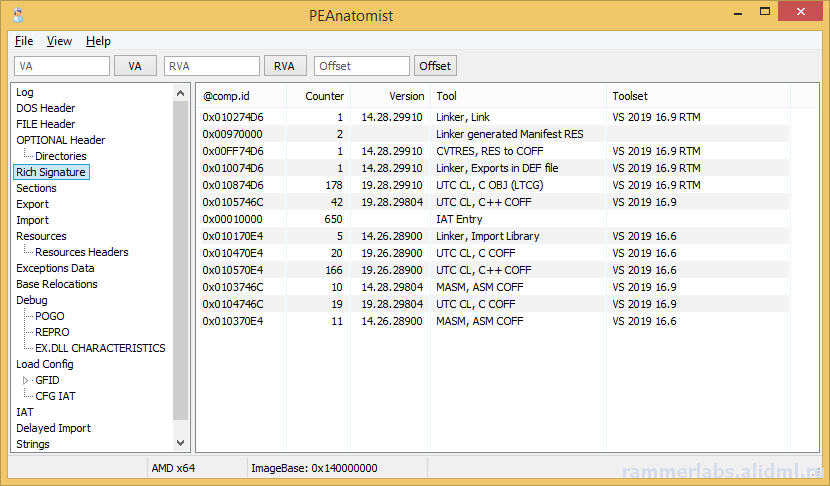 File Formats PE32 PE32+ COFF Object File MSVC IntermediateLanguage AnonCOFF Object File (MSVC CxxIL) ExtendedObj (BIGobj) Objects Library DBG Stripped Debug Information MS PDB (Program Database), MSF v7 PE Image Architectures Intel x86 AMD64 ARM7 ARM7 Thumb ARM8-64 Intel IA64 Hybrid (CHPE, ARM64X, ARM64EC) A little of supported headers and data structures PE: IMAGE_DOS_HEADER, IMAGE_FILE_HEADER, IMAGE_OPTIONAL_HEADER, IMAGE_OPTIONAL_HEADER64 and the DataDirectories List with additional information about some fields PE: Table of COFF symbols PE: Sections table, supporting long section names (via symbols table) and entropy calculating PE: Import table (supports MS-styled names demangling) PE: Bound Import Table PE: Delayed Import Table PE: Export Table with additional info PE: Resource Table with additional info about different resource types and detailed view for all types PE: Base Relocation Table. Target address determining and interpretation available for all supporting architectures. It detects imports, delayed imports, exports, tables from loadconfig directory, ANSI and UNICODE strings. PE: Brief info about PE Authenticode Signature PE: LoadConfig Directory with SEH, GFID, decoded CFG bitmap, GIAT, CFG LongJumps, CHPE Metadata, ARM64X Metadata, Dynamic Value Reloc Table, Enclave Configuration, Volatile Metadata, CFG EH Continuations tables parsing and additional information about some fields PE: Hybrid PE (ARM64X) Export, Import, DelayImport tables PE: Debug Directory. It parses contents of CODEVIEW, POGO, BBT, VC FEATURE, REPRO, FPO, EXDLL CHARACTERISTICS, SPGO debug types PE: TLS config and callbacks table with additional information about some fields PE: Exceptions Data Table. x64 (including version 2 with EPILOG unwind codes), arm, arm64, ia64 architectures are support, as well as chain of unwind data for x64, language-specific handler data (C Scope, C++ FuncInfo, C++ EH4, C++ DWARF LSDA) and hexadecimal view of unwind data PE: COM Descriptor directory pasring: headers, tables and metadata info available. Some of NGEN and ReadyToRun headers are also included PE: Decode Rich signature indicating the tool used, the action being taken, the full version of the tool, and the version of VisualStudio to which the tool belongs PE: IAT table contents PE: VB5 and VB6 typical structures: project info, DLLCall-imports, referenced modules, object table PE: Detecting an ANSI and Unicode encoded strings PE: Plotting entropy OBJ: IMAGE_FILE_HEADER, ANON_OBJECT_HEADER, ANON_OBJECT_HEADER_V2, IMPORT_OBJECT_HEADER OBJ: COFF symbol table with decoding @comp.id and @feat.00, as well as auxiliary symbols OBJ: Section table and relocations for the selected section OBJ: Exceptions Data Table. x64 (including version 2 with EPILOG unwind codes), arm, arm64, ia64 architectures are support, as well as chain of unwind data for x64 OBJ: Functions xFG-hash values table OBJ: Volatile Metadata information decoding OBJ: Table of CodeView Debug Symbols OBJ: Table of CodeView Types OBJ: Table of MSVC CxxIL Types (.cil$db) OBJ: Table of MSVC CxxIL Global Symbols (.cil$gl) OBJ: Table of MSVC CxxIL Local Symbols (.cil$sy) LIB: List of archive members LIB: The first and second (if available) linker members LIB: Summary table of import elements IMPORT_OBJECT_HEADER, if any LIB: /ECSYMBOLS/ and /XFGHASHMAP/ members DBG: Table of COFF symbols DBG: Debug directory with more information about CODEVIEW, FPO, EXCEPTION, FIXUP, OMAP2SRC, SRC2OMAP contents DBG: Table of CodeView Debug Symbols DBG: Table of CodeView Types PDB: List of MSF streams with a brief description of characteristics and content PDB: PDB, TPI, DBI, IPI stream headers PDB: CodeView type tables from TPI and IPI streams PDB: Codeview symbol tables from GSI, Publics, ModI streams PDB: Subsections of the DBI stream: list of streams, information about the content of the PE sections, information about the source files of the modules PDB: Debug directory with additional information about the contents of FPO, EXCEPTION, FIXUP, OMAP2SRC, SRC2OMAP, sections, FRAMEDATA and original sections ZIP-file hash: MD5: BBADE2605B60B78D948CFC62F603C6D3 SHA1: C43FFB43C7752CA9C244B3414377F3B697A3244A SHA256: DA42E181C437B1EBD75DB2D646046AA1F58B5FF8411DDBECB13E446852B14FFD This tool was designed to be used with: Windows XP SP3 (x86), Windows Vista, Windows 7, Windows 8, Windows 8.1, Windows 10, Windows 11, ReactOS 0.4 and newer Changes: 0.2.12224.1953 (2023-10-24) 12224.1254: Fixed buffer overflow when copying lines containing RVA descriptions for methods from the READYTORUN_SECTION_INSTANCE_METHOD_ENTRYPOINTS table to the clipboard 12224.1538: Fixed a bug in copying lines containing RVA descriptions for .net metadata tokens, Ready2Run and .net method and type signatures to the clipboard 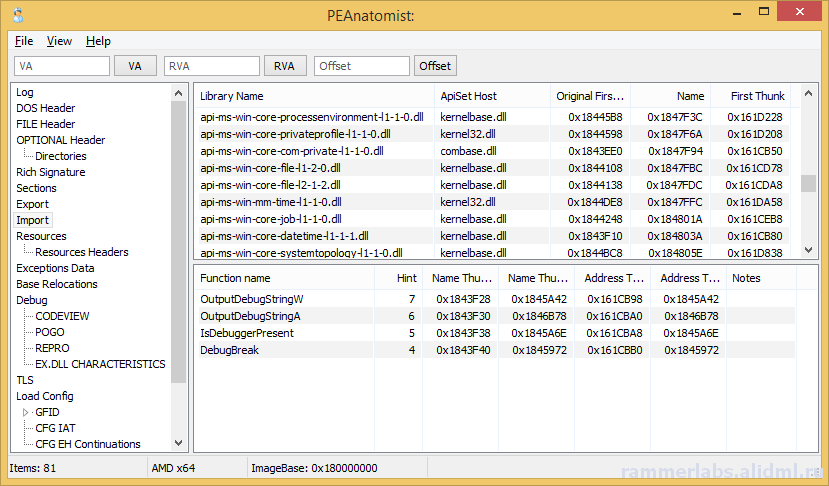 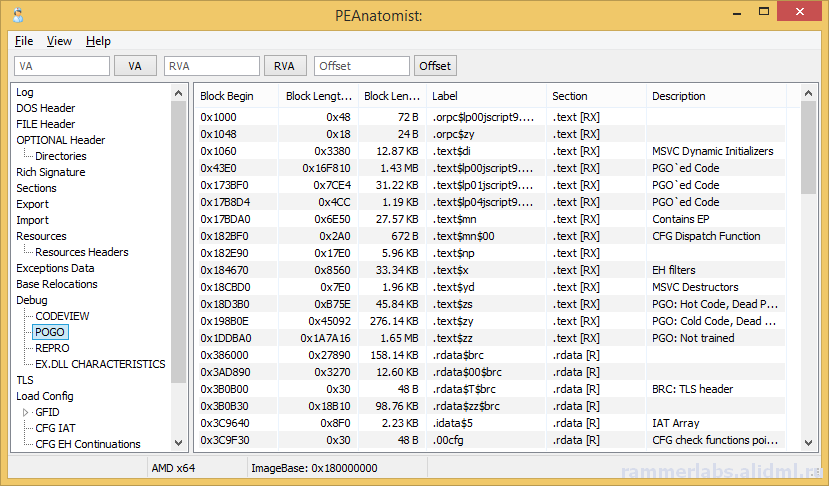 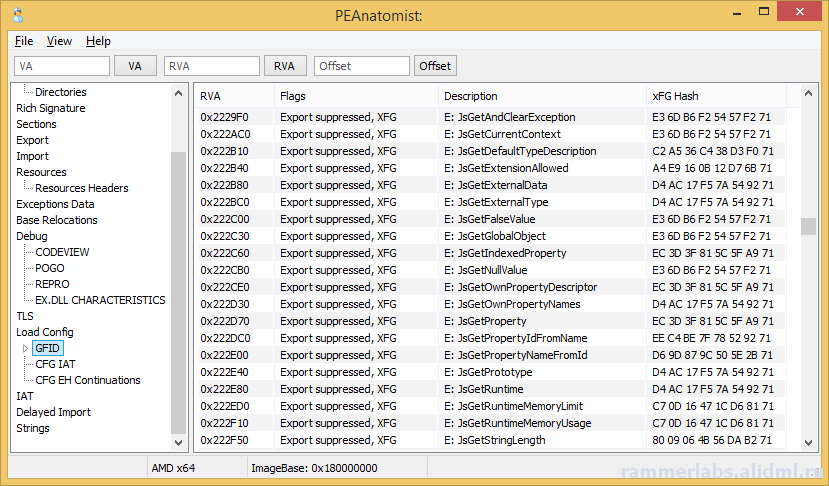 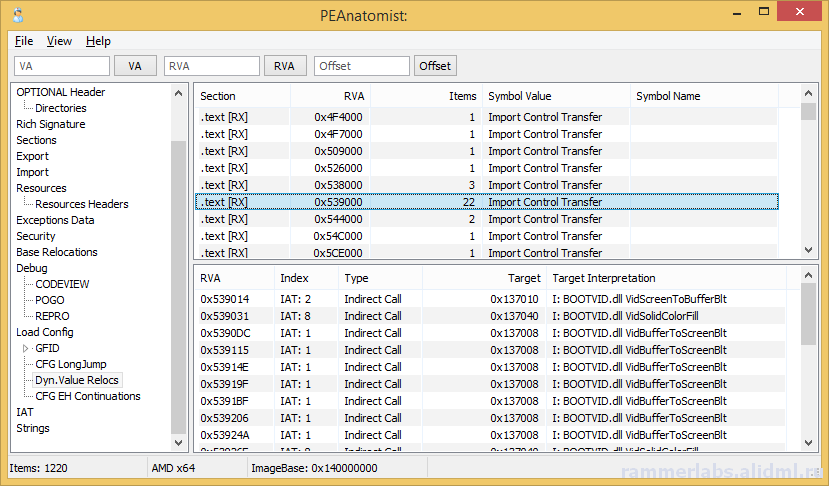 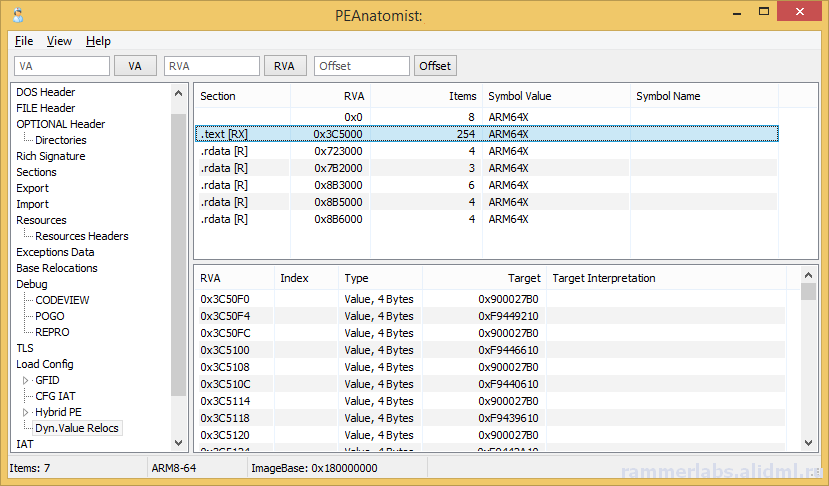 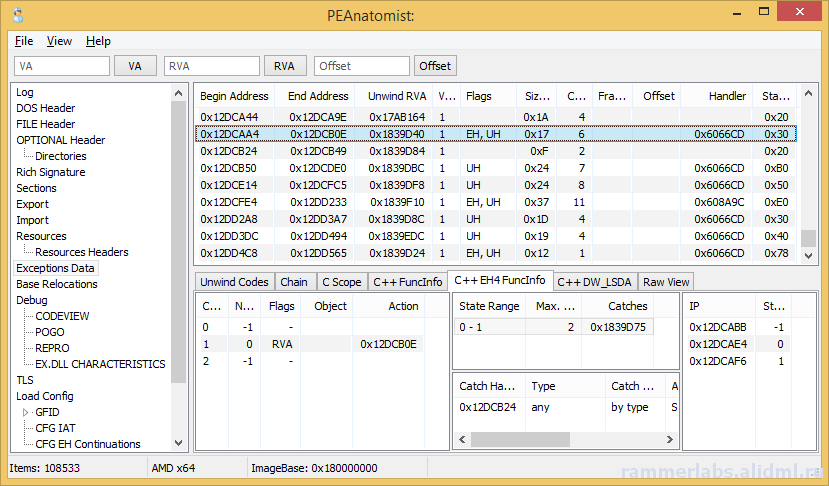 Click here to visit the author's website. Continue below for the main download link. |
||||||||
| Downloads | Views | Developer | Last Update | Version | Size | Type | Rank | |
| 4,129 | 8,939 | RamMerLabs <img src="https://www.oldergeeks.com/downloads/gallery/thumbs/PEAnatomist7_th.png"border="0"> | Nov 09, 2023 - 12:42 | 0.2.12224.1953 | 252.8KB | ZIP |  , out of 44 Votes. , out of 44 Votes. |
|
| File Tags | ||||||||
| v0.2 PEAnatomist | ||||||||
|
Click to Rate File Share it on Twitter → Tweet
|