|
|

Your download link is at the very bottom of the page... always. |
Processed through Paypal No account required. |
Buy our over-priced crap to help keep things running.










|
|

Your download link is at the very bottom of the page... always. |
Processed through Paypal No account required. |










| File - Download PeStudio Standard v9.09 | ||||||||
| Description | ||||||||
|
A plea... Deanna and I have been running this site since 2008 and lately we're seeing a big increase in users (and cost) but a decline in percentage of users who donate. Our ad-free and junkware-free download site only works if everyone chips in to offset the revenue that ads on other sites bring in. Please donate at the bottom of the page. Every little bit helps. Thank you so much. Sincerely, your Older Geeks: Randy and Deanna Always scroll to the bottom of the page for the main download link. We don't believe in fake/misleading download buttons and tricks. The link is always in the same place. PeStudio Standard v9.09 pestudio is used by many Cyber Emergency Response Teams (CERT) worldwide in order to perform malware initial assessments. Malicious software often attempts to hide its intents in order to evade early detection and static analysis. In doing so, it often leaves suspicious patterns, unexpected metadata, anomalies and other indicators. The goal of pestudio is to spot these artifacts in order to ease and accelerate Malware Initial Assessment. The tool uses a powerful parser and a flexible set of configuration files that are used to detect various types of indicators and determine thresholds. Since the file being analyzed is never started, you can inspect unknown or malicious executable file, trojan and ransomware without any risk of infection. features pestudio implements a rich set of features that is especially designed to retrieve every single detail of any executable file. Results are checked against the Microsoft specification. Additionally, the content of the file being analyzed is checked against several white and black lists and thresholds. pestudio can query Antivirus engines hosted by Virustotal. Only the MD5 of the file being analyzed is sent. This feature can be switched ON or OFF using an XML file included with pestudio. Even a suspicious binary file must interact with the operating system in order to perform its activity. pestudio retrieves the libraries and the functions referenced. Several XML files are used to blacklist functions (e.g. Registry, Process, Thread, File, etc). Blacklist files can be customized and extended according to your own needs. pestudio brings out the intent and purpose of the application analyzed. Resources sections are commonly used by malware to host payload. pestudio detects many embedded file types (e.g. EXE, DLL, SYS, PDF, CAB, ZIP, JAR, etc ). Detected items can be saved to a file, allowing therefore the possibility of further analysis. The goal of pestudio is to allow investigators to analyze unknown and suspicious executable files. For this purpose, pestudio can also produce an XML output report file documenting the executable file being analyzed. The goal of this XML output Report file is to offer its further use by any third-party analysis tool. pestudio runs from the Graphical User Interface (GUI) as well as from the Command prompt (CLI). Running pestudio from the prompt offerts the possibillty to analyze executable file and to create associated XML output files in a batch mode. Version 9.09 . Fix a bug when handling malformed relocations table . Add handling of Rich-header sha256: dca9e38b32d1c5aeb7fbb3e04e7b6f4a070c1dbd116b60e35079560763988ca5 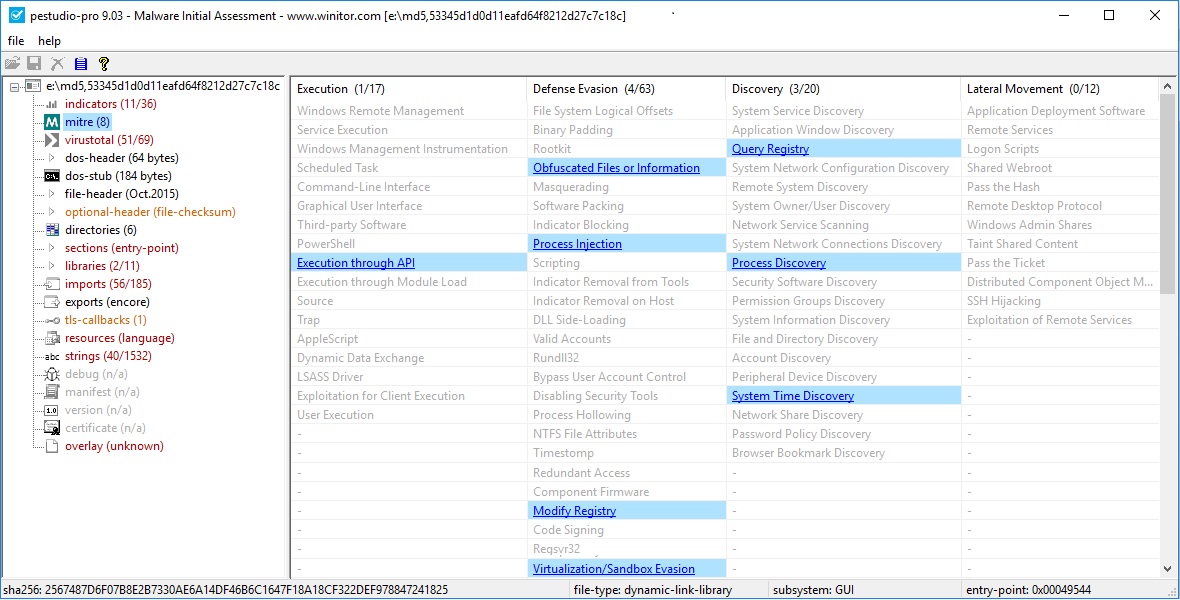 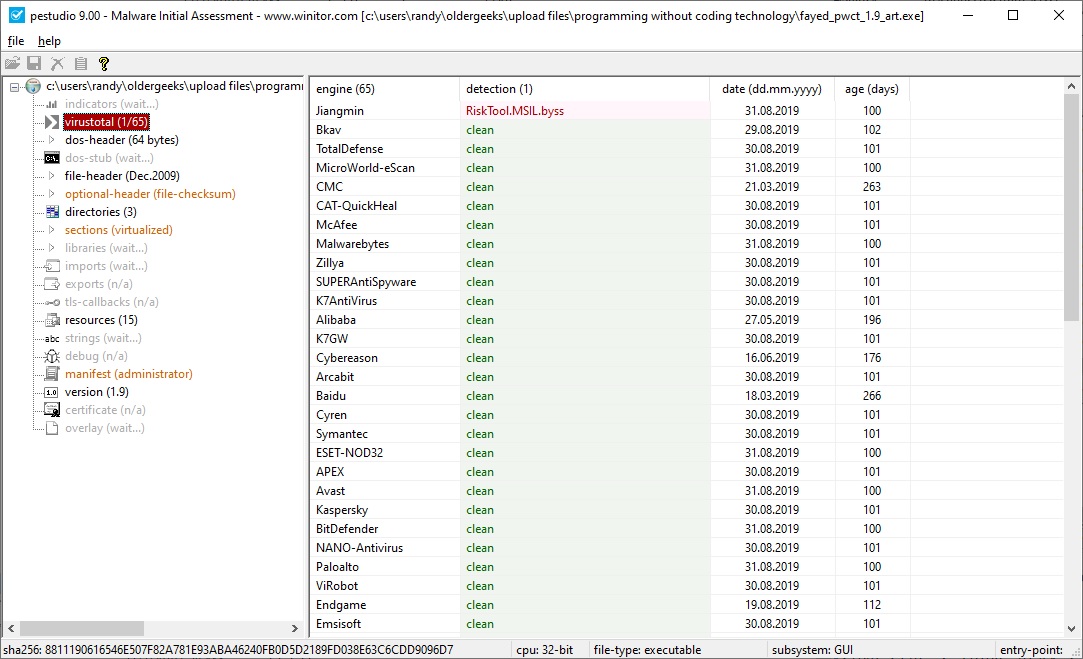     Click here to visit the author's website. Continue below for the main download link. |
||||||||
| Downloads | Views | Developer | Last Update | Version | Size | Type | Rank | |
| 9,469 | 22,684 | Marc Ochsenmeier <img src="https://www.oldergeeks.com/downloads/gallery/thumbs/pestudio1_th.png"border="0"> | Dec 27, 2020 - 13:16 | 9.09 | 956.3KB | ZIP |  , out of 65 Votes. , out of 65 Votes. |
|
| File Tags | ||||||||
| PeStudio v9.09 Standard | ||||||||
|
Click to Rate File Share it on Twitter → Tweet
|