|
|

Your download link is at the very bottom of the page... always. |
Processed through Paypal No account required. |
Buy our over-priced crap to help keep things running.










|
|

Your download link is at the very bottom of the page... always. |
Processed through Paypal No account required. |










| File - Download Ghidra v11.2 | ||||||||
| Description | ||||||||
|
A plea... Deanna and I have been running this site since 2008 and lately we're seeing a big increase in users (and cost) but a decline in percentage of users who donate. Our ad-free and junkware-free download site only works if everyone chips in to offset the revenue that ads on other sites bring in. Please donate at the bottom of the page. Every little bit helps. Thank you so much. Sincerely, your Older Geeks: Randy and Deanna Always scroll to the bottom of the page for the main download link. We don't believe in fake/misleading download buttons and tricks. The link is always in the same place. Ghidra v11.2 A software reverse engineering (SRE) suite of tools developed by NSA's Research Directorate in support of the Cybersecurity mission SHA-256: a98fe01038fe8791c54b121ede545ea799d26358794d7c2ac09fa3f5054f3cdc Ghidra Software Reverse Engineering Framework Ghidra is a software reverse engineering (SRE) framework created and maintained by the National Security Agency Research Directorate. This framework includes a suite of full-featured, high-end software analysis tools that enable users to analyze compiled code on a variety of platforms including Windows, Mac OS, and Linux. Capabilities include disassembly, assembly, decompilation, graphing, and scripting, along with hundreds of other features. Ghidra supports a wide variety of process instruction sets and executable formats and can be run in both user-interactive and automated modes. Users may also develop their own Ghidra plug-in components and/or scripts using Java or Python. In support of NSA's Cybersecurity mission, Ghidra was built to solve scaling and teaming problems on complex SRE efforts, and to provide a customizable and extensible SRE research platform. NSA has applied Ghidra SRE capabilities to a variety of problems that involve analyzing malicious code and generating deep insights for SRE analysts who seek a better understanding of potential vulnerabilities in networks and systems. Ghidra Installation Guide   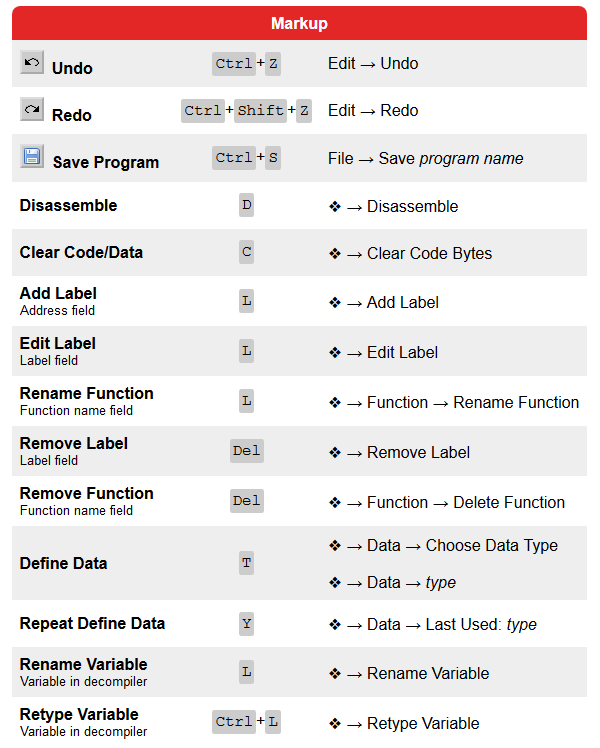 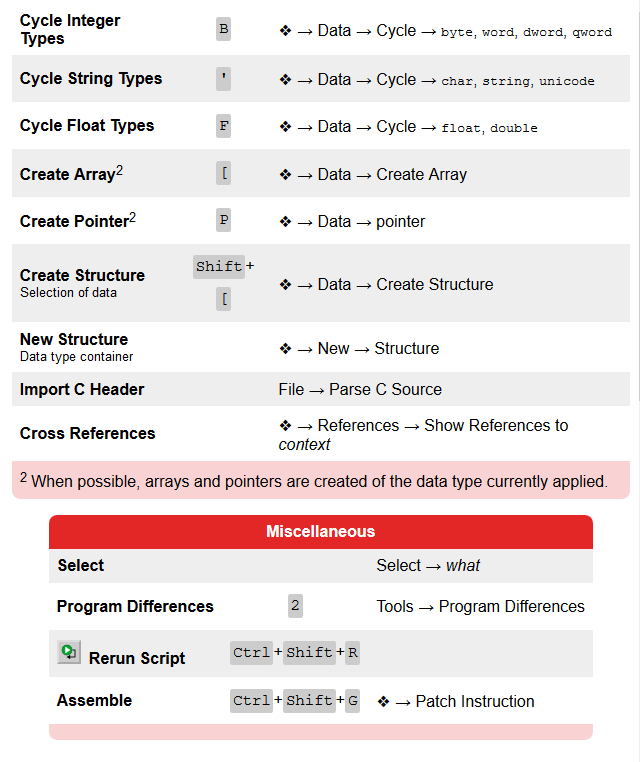 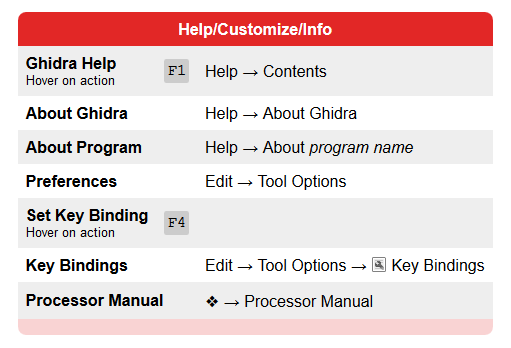 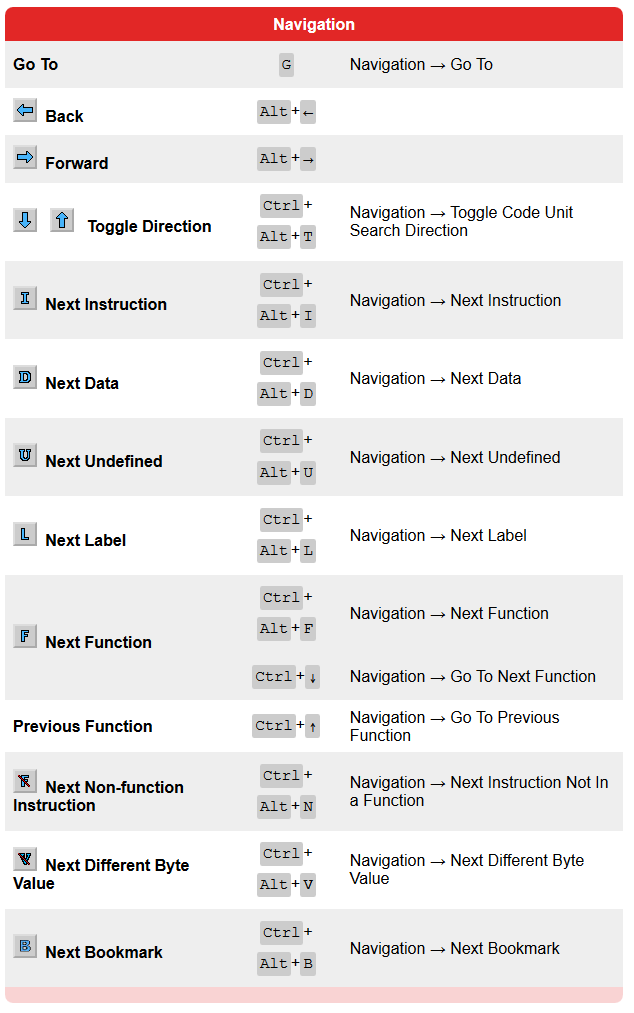  Changes v11.2 (September 2024) New Features Basic Infrastructure. Ghidra now requires JDK 21 to run. (GP-4122) Build. A Gradle wrapper script is now included at support/gradle/gradlew(.bat) which can be used to perform all Gradle commands without the need for prior Gradle installation. The Gradle wrapper requires an Internet connection to work. Offline Gradle installations on the PATH continue to work the same way as before. (GP-4486, Issue #455) Debugger. Provided new launchers/features for the traceRMI version of dbgeng, including extended launch options, kernel debugging, and remote process server connections. (GP-4686) Debugger. The Debugger Python components now require Python 3.9 to Python 3.12. (GP-4842) Decompiler. The Decompiler now supports the automatic recovery of stack strings. (GP-3307, Issue #1380, #2285, #6431, #6592) Decompiler. Added a Search All button to the Decompiler Find dialog. This button will show all results of the search in a table. (GP-3491, Issue #5317, #538) GUI. Added Create Table action to the Symbol Tree and Symbol Table to create a new temporary table of symbols. (GP-4574) GUI. Added a Find Uses of field action to the Enum Editor. (GP-4577, Issue #6475) GUI. Added support for Ctrl-A to select all in the Python window. (GP-4605, Issue #6502) Headless. Added a JShell launcher with the full Ghidra classpath. (GP-4876) Processors. Added Intel MC16/60 and MC16/80 processor specifications. (GP-4879) Scripting. Added VSCodeProjectScript, which can create a new Visual Studio Code project that is setup to do Ghidra scripting and module development, with similar capabilities to the Eclipse GhidraDev plugin. (GP-4795) Search. Updated the Memory Search feature to show results in the query window and added two new features: (1) dynamic updating of results that change, stay the same, increment, or decrement; and (2) combining results from successive searches using boolean set operations. (GP-4559) Improvements Analysis. Refactored Sparc processor detection and mitigation of Call/Return behavior due to an instruction in the delay slot that changes the o7 link register. Also fixed 64/32 relocations, sparc calling conventions, and added several missing instructions and hidden structure return pointer location. (GP-3808, Issue #5646, #6300) Analysis. Added support for Golang 1.15 and 1.16. Versions supported are now 1.15-1.22. (GP-4482) Analysis. Added a new MIDIDataType and audio player for embedded MIDI scores. (GP-4516, Issue #6337) Analysis. Refactored eBPF analyzers and expanded on applied BPF Helper functions. (GP-4682) Analysis. Updated the RTTIAnalyzer to improve its determination of the end of virtual function tables. (GP-4748) BSim. Added BSim database connect/disconnect actions to BSim Server Manager. This will allow an idle connection to be disconnected without the need to exit Ghidra or removing a server entry, which, in the case of a local H2 database, will allow another process to use it. (GP-4867, Issue #6703) Byte Viewer. Extended HexInteger to other integral data types. (GP-4709, Issue #6658, #6659) CodeCompare. Added ability to add functions to the last function comparison window. (GP-4634) Data Types. Added Edit Data Type action that allows users to edit a chosen data type from anywhere in the tool by using the Ctrl-Shift-D keyboard shortcut. (GP-4148, Issue #5975, #6576) Data Types. Added Undo/Redo popup menu actions for Archives within datatype tree. (GP-4719) Data Types. Added Undo/Redo support to the structure and union datatype editors as well as other minor improvements. (GP-4740) Data Types. Improved performance of various structure editor behaviors including setting the structure size. (GP-4949, Issue #6504, #6936) Debugger. Provided more complete compiler matching using ldefs language definition files. (GP-4675) Debugger:Agents. Deprecated Framework-Debugging module and Model-based debug connectors, moving toward removal. (GP-4801) Debugger:Agents. User may now use binary (0b prefix), octal (0 prefix), or hex (0x prefix) in integer-valued launcher option fields. (GP-4847) Debugger:Registers. Changed how Go To [address] actions are presented with regard to Force Full View. (GP-3898, Issue #5817) Decompiler. Added Go To Next/Previous Highlight actions to allow navigating Decompiler middle-mouse highlights. (GP-3494, Issue #538) Decompiler. Improved Function Editor to facilitate partial changes which limit impact to Decompiler results (e.g., only change calling convention) and avoid locking full function signature. (GP-4324) Decompiler. Improved multi-threaded decompilation performance and possibly disassembly by removing some unnecessary locking. (GP-4712, Issue #6649, #6650) Decompiler. Provided initial support for recovering optimized heap strings in the Decompiler. (GP-4733) Decompiler. The Decompiler now forces casting to a signed value when converting integers to floating-point. (GP-4871, Issue #6760) Demangler. Added support for GNU Demangler output simplification. (GP-3810, Issue #5725) Demangler. Improved Microsoft Demangler to include handling of noexcept attributes and certain type name suffixes. (GP-4626) Demangler. Modified MDMang: added calling conventions and custom data type; added end, empty parameter, and unnamed template types; modified reference modifiers and guard name processing; fixed empty member pointer qualification; and worked around LLVM embedded object issue. (GP-4663) Demangler. Changed application of MDMang `anonymous namespace' strings to their underlying anonymous name to avoid namespace conflicts. (GP-4717, Issue #6661) Demangler. Added char8_t primitive type to DemangledDataType. (GP-4823) Demangler. Updated the GNU Demangler to support global constructors and destructors. (GP-4825, Issue #6791) Documentation. Added discussions of program specification extensions and instruction length modification to the advanced Ghidra class slides, along with miscellaneous clarifications and improvements. (GP-3774, Issue #5667, #5702) DWARF. Added DWARF analyzer option to ignore parameter storage location info and to use calling convention default layout instead. Also added DWARF analyzer option to specify the calling convention name for functions created by the analyzer. (GP-4150) Eclipse Integration. The latest Eclipse GhidraDev plugin (4.0.0) now requires Eclipse 2023-12 or later running under JDK 21 or later. (GP-4846) Function Compare. Added actions to compare functions from the Listing, Decompiler, and Functions Table. (GP-4619) GUI. Updated the Listing and Byte Viewer title bars to show the number of addresses or bytes selected while dragging. (GP-1359, Issue #2482) GUI. Added Show Namespace action to the Function Call Trees to display the function's namespace in each node. (GP-3251, Issue #5115) GUI. Add Filter Thunks action to the Function Call Trees to hide think functions. (GP-3252, Issue #5116) GUI. Added the Simplified Name column to the Symbol Table. (GP-3377, Issue #6125) GUI. Added the ability to Snapshot the Symbol Tree. (GP-3849) GUI. Added the structure member comment to the Decompiler tooltip window. (GP-4661) GUI. Added single option in the Front End Tool to control whether or not cursors blink in any field panel or text component. (GP-4676, Issue #6570) GUI. The Edit Data Type action in the Decompiler will now select the structure field row when launching the editor. (GP-4728, Issue #5717) GUI. New Listing fields and Copy Special actions have been added for imagebase offset, memory block offset, and function offset (disabled by default). (GP-4855, Issue #6794) Headless. Improved handling of headless command-line arguments when the optional list of arguments passed to a pre/post script contain arguments that start with a dash. (GP-4707, Issue #6639) Importer. Added a new Add Library Search Path action to files and folders in the File System Browser that will allow library files to be loaded from within a GFileSystem. (GP-4563) Importer. Added a new -librarySearchPaths command line argument to the headless analyzer, which allows a semicolon-delimited list of library search paths to be specified. (GP-4564) Importer. OMF records are now marked up. (GP-4722) Importer:ELF. Improved ELF handling of unresolved symbols during relocation-processing to prevent import failure. (GP-4737, Issue #6673) Multi-User. Upgraded yajsw to 13.12. (GP-4860) PDB. Changed the PDB symbol server search config dialog to allow marking symbol servers as trusted/untrusted instead of using the symbol server's connection type. (GP-4735) PDB. Improved PDB class namespaces determination and standardized some naming between PDB and MDMang. (GP-4773) PDB. Added char8_t primitive type to PDB Universal analyzer. (GP-4822) PDB. Modified PDB MSDIA interpretation of malformed datatype fields with no underlying datatype. (GP-4827, Issue #6744) Processors. Fixed several PPC EVX instructions that were not affecting the destination register as a return value assigned from a pseudoOp call. (GP-4702) Processors. Added PSPEC label description tag and addr="next" which allows for a large number of contiguous labels placed at an address based on the previous label without specifying the exact address of each label. (GP-4742) Processors. Processor specs now accept the volatile attribute in tags. (GP-4849, Issue #6755) ProgramTree. Updated the Program Tree default double-click behavior. Double-clicking now navigates instead of replacing the view. This can be changed in the tool options. (GP-4691) Scripting. GhidraScripts can now declare an @runtime metadata comment to specify which GhidraScriptProvider is required to run them (e.g., Jython). This will allow different GhidraScriptProviders that use the same script file extension (e.g., .py) to coexist. (GP-4706) Scripting. Improved RecoverClassesFromRTTIScript heuristics for determining class constructors and destructors. (GP-4764) Scripting. Changed RecoverClassesFromRTTIScript virtual function definitions from using the formal signature (i.e., no this param) to using void *this param. This will improve the Decompiler output while continuing to not force a particular class structure on the generic definition's this param. (GP-4812) Scripting. RecoverClassesFromRTTIScript now caches vfunction list in order to speed up processing. (GP-4863, Issue #6834) Scripting. Fixed a recursion issue in RecoverClassesFromRTTIScript. (GP-4865, Issue #6832, #6833) Scripting. Changed PasteCopiedListingBytesScript to handle hexdump format and listing bytes field split to multiple lines. (GP-4928) Terminal. Added Select All action to Terminal window. (GP-4631, Issue #6502) Version Tracking. The Version Tracking Matches table now has table column filters and now allows users to delete matches from the table (although this is not recommended). (GP-4410, Issue #6066, #6281) Bugs Basic Infrastructure. Fixed a ClassSearcher exception that could occur when launching Ghidra in single jar mode. (GP-4844, Issue #6809) Data Types. Corrected concurrency exception related to use of EnumDataType.getNames() method. (GP-4797, Issue #6765) Data Types. Fixed StructureDB.delete(Set ordinals) and UnionDB.delete(Set ordinals) method implementations which failed to properly remove component records from database and update remaining components correctly. This method is used by the Structure and Union editors when removing components. (GP-4814) Data Types. Fixed issue in the Data Type Chooser dialog that caused inconsistent auto-complete behavior. (GP-4854) Debugger. Fixed catchpoint-related errors in GDB versions <= 10. (GP-4745, Issue #6666) Debugger. Provided an initial fix for dealing with error induced by the occurrence of continue during another GDB command. (GP-4750, Issue #6678) Debugger. Fixed potential register description errors when info registers all or info registers general are invalid. (GP-4757) Debugger. Added attach script for dbgeng (WinDbg). (GP-4784, Issue #6735) Debugger. Fixed an issue with Listing display when trace overlay spaces are present. This issue had affected the dbgmodel connector. (GP-4788) Debugger. Removed test logic that was accidentally left in place. (GP-4841, Issue #6802) Debugger. Fix for potentially missing Attributes field from older versions of dbgmodel. (GP-4856, Issue #6825) Debugger. The default Emulator was updated to remove TraceRmi launchers. Users should delete and re-import Emulator.tool, or remove the TraceRmiPlugin manually. (GP-4953) Debugger:Emulator. Fixed memory-space issues, especially in RegistersProvider. (GP-4781) Debugger:Emulator. Changed stack allocation to adhere to SP in program register context at PC. (GP-4834, Issue #6427) Debugger:GDB. Fixed issue with GDB continuing instead of stepping over (or out of) library function calls. (GP-4858, Issue #6822) Debugger:Mappings. Fixed launchers to adhere to Modules window's Auto-Map setting. Fixed DebuggerStaticMappingService to update properly on changes. (GP-4713, Issue #6662) Debugger:Mappings. Fixed/rewrote buggy StaticMappingService. (GP-4868) Debugger:Memory. Fixed stale Force Full View menu toggle when tabbing between traces. (GP-4835) Debugger:Registers. Fixed issue preventing Registers panel from displaying frames other than 0. (GP-4850) Debugger:Watches. Fixed issue in Watches where evaluation of concatenations failed. The error reported was "index -1 in array of size 2" or similar. (GP-4952) Decompiler. Fixed analysis of floating-point expressions in the Decompiler that could sometimes cause loss of precision in constants. (GP-2559, Issue #4586, #5785, #6708) Decompiler. Fixed a bug causing the Decompiler to fail to resolve array references properly in nested structures. (GP-4887) Decompiler. Fixed a corner case in the Decompiler for optimized division simplification where the division operands are extended from different-sized variables. (GP-4890, Issue #6648) Decompiler. Corrected a use after free vulnerability in Sleigh decompiler backend. (GP-4929, Issue #6890) Diff Tool. Fixed the Save Default Diff Apply Settings action in the Diff Apply Settings window. (GP-4670) Eclipse Integration. Fixed a GhidraDev issue that could result in a NullPointerException within GhidraHelpService when launching Ghidra. (GP-3490, Issue #6734) Function. Fixed an issue with incomplete function body creation due to the removal of a branching reference when the branch destination was to the next instruction and the instruction flowType had no fallthrough. (GP-4926) GUI. Fixed the Structure Editor Tab key traversal. (GP-4716, Issue #5738) GUI. Fixed issue in add references dialog where moving the mouse sometimes reset the address space combo box back to the default ram space. (GP-4779) GUI. Fixed minor rendering issues with combo boxes when using the Metal Look and Feel. (GP-4818) GUI. Fixed Structure Editor sometimes not getting focus when opening. (GP-4857, Issue #6782) GUI. Fixed an exception in the Stack editor when editing and using the down arrow. (GP-4891, Issue #6883) GUI. Fixed incorrect cell being edited on Tab key press while editing in the Enum Editor. (GP-4892, Issue #6873) Importer. Fixed an IndexOutOfBoundsException that could occur when loading OMF binaries. (GP-4884, Issue #6862) Importer:ELF. Corrected regression bug where ELF Importer was ignoring option to disable relocation processing. (GP-4799, Issue #6751) Importer:ELF. Added missing mips opinion for R3/4 n32 automatic processor identification during import. (GP-4939) Listing. Fixed bug in the GoTo dialog where it wouldn't find a label if you had more than one namespace in the path. (GP-4761, Issue #6699) Multi-User. Fixed regression causing Version Control status not updated after check-in. (GP-4921) PDB. Supplied work-around for class that contains inner member with same class name as containing class name; pertaining to LLVM lambdas. (GP-4595) PDB. Fixed a bug in the processing of PDB MSDIA names passed from the native pdb.exe processing component. Members that had a bit-field type or that had a namespace delimiter in the name were affected. (GP-4843, Issue #6788) Processors. Fixed PIC16 PCLATH and RP0 code flow and data reference issues. (GP-4596, Issue #3239, #6466) Processors. Fixed ARM ldaexd instruction semantics. (GP-4645, Issue #6526) Processors. Fixed ARM sha1su0.32 instruction semantics. (GP-4646, Issue #6529) Processors. Fixed ARM sha1su1.32 instruction semantics. (GP-4647, Issue #6530) Processors. Corrected CMOV semantics when destination and source overlap. (GP-4714, Issue #6523) Processors. Fixed bug in SPARC sdivcc instruction. (GP-4747, Issue #6689) Processors. Fixed m68000 ext instruction not updating flags. (GP-4749, Issue #6679, #6690) Processors. Fixed extension of immediates for certain variants of the x86 SBB instruction. (GP-4754, Issue #6521) Processors. Corrected semantics for x86 PEXTR instructions which write to memory. (GP-4769, Issue #6511) Processors. Corrected semantics of x86 CMPPS instruction. (GP-4772, Issue #6512) Processors. Added semantics for several x86 AVX instructions in use by GCC: VCVTTSx2Sx, VDIVSx, VINSTERT128, and VEXTRACT128. (GP-4776) Processors. Corrected semantics of x86 PACKUSWB instruction. (GP-4777, Issue #6514) Processors. Added missing float-to-integer cast operation, trunc(), to x86 CVTSD2SI instruction. (GP-4778, Issue #6513) Processors. Fixed aliasing issues in certain x86 SIMD instructions. (GP-4783, Issue #6524) Processors. Fixed incorrect .sla file reference in PPC e500mc processor specification. (GP-4826) Processors. Fixed issue with the M68000 fmovem.l instruction using FPCR in place of FPIAR. (GP-4845, Issue #6810) Processors. Fixed sparc 32/64-bit multiply instructions. (GP-4912, Issue #6287, #6346) ProgramDB. Corrected NullPointerException when setting instruction length override for a non-fallthrough instruction. (GP-4775) References. Fixed spurious replacement of small constants when the low byte of an offset matches the low byte of the reference address. Also turned the option to manipulate constants with masks and shifts to be off by default. (GP-4667, Issue #1564) Scripting. Added check in the RecoverClassesFromRTTIScript to make sure ClassHierarchyDescriptor symbols are in a non-Global namespace before trying to promote their namespace to a class namespace. If such symbols are found in the Global namespace it indicates potential issues with either the RTTI data or the processing of the RTTI data; in these cases, no class recovery will be done for the associated classes. (GP-4763, Issue #6704) Scripting. Fixed NullPointerException in PropagateExternalParametersScript. (GP-4883, Issue #6841) Scripting. Fixed CodeUnitInsertionException error in RecoverClassesFromRTTIScript.java script. (GP-4932, Issue #6848) Notable API Changess Search. (GP-4559) The MemorySearchService has been changed. This had been a very specific service API created to support just one plugin and was not generally useful. The three existing methods have been consolidated into one method. The old service has been marked as deprecated and may be removed in future releases. If, in the unlikely event that anyone is using this service, please contact the Ghidra team to discuss your use case. Data Types. (GP-4949) Added API method Structure.setLength(int length) which allows the size of a non-packed structure to be set. Debugger:Agents. (GP-4847) LaunchConfigurator.configureLauncher() is changed such that arguments now requires ValStr<?> instead of just ? for its values. This affects both the new Trace-RMI launchers and the deprecated object-model launchers. Click here to visit the author's website. Continue below for the main download link. |
||||||||
| Downloads | Views | Developer | Last Update | Version | Size | Type | Rank | |
| 5,141 | 13,112 | NSA's Research Directorate <img src="https://www.oldergeeks.com/downloads/gallery/thumbs/Ghidra7_th.png"border="0"> | Sep 27, 2024 - 12:35 | 11.2 | 405.05MB | ZIP |  , out of 82 Votes. , out of 82 Votes. |
|
| File Tags | ||||||||
| Ghidra v11.2 | ||||||||
|
Click to Rate File Share it on Twitter → Tweet
|