Buy our over-priced crap to help keep things running.




















| Files | ||||
| File Name | Rating | Downloads | ||
| AlternateStreamView 32bit v1.56 AlternateStreamView 32bit v1.56 AlternateStreamView is a small utility that allows you to scan your NTFS drive, and find all hidden alternate streams stored in the file system. After scanning and finding the alternate streams, you can extract these streams into the specified folder, delete unwanted streams, or save the streams list into text/html/csv/xml file. System Requirements This utility works on any version of Windows starting from Windows 2000 and up to Windows 10. Both 32-bit and 64-bit systems are supported. Known Issues It seems that starting from Windows 7, the standard 'Open With' dialog-box of Windows stopped working with alternate streams, and thus the 'Open Selected Stream With...' option provided by AlternateStreamView also doesn't work... Versions History Version 1.56: Added /RunAsAdmin command-line option for running AlternateStreamView as administrator. About Alternate Streams in NTFS File System NTFS system has a feature that allows you to add multiple streams in addition to the main file stream. When you open or view the file, only the main file stream is visible, while other additional streams are hidden from the user. Here's 3 examples of alternate streams usage in Windows operating system: Favorites of Internet Explorer: When You add a Web site link into your 'Favorites', a .url file containing the url and description is created. However, if the Web site also have an icon (favicon), the icon is saved as alternate stream for the same url file. The stream name of the icon is :favicon:$DATA Downloaded files of Internet Explorer: When you download and save a file with Internet Explorer, it automatically add a zone information for the saved file. This zone information is used for identifying the file as downloaded file from the Internet. The stream name in this case is :Zone.Identifier:$DATA Summary information of files: When ... |
 |
9,138 | Nov 13, 2019 Nir Sofer 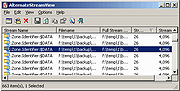 |
|
| AlternateStreamView 64bit v1.56 AlternateStreamView 64bit v1.56 AlternateStreamView is a small utility that allows you to scan your NTFS drive, and find all hidden alternate streams stored in the file system. After scanning and finding the alternate streams, you can extract these streams into the specified folder, delete unwanted streams, or save the streams list into text/html/csv/xml file. System Requirements This utility works on any version of Windows starting from Windows 2000 and up to Windows 10. Both 32-bit and 64-bit systems are supported. Known Issues It seems that starting from Windows 7, the standard 'Open With' dialog-box of Windows stopped working with alternate streams, and thus the 'Open Selected Stream With...' option provided by AlternateStreamView also doesn't work... Versions History Version 1.56: Added /RunAsAdmin command-line option for running AlternateStreamView as administrator. About Alternate Streams in NTFS File System NTFS system has a feature that allows you to add multiple streams in addition to the main file stream. When you open or view the file, only the main file stream is visible, while other additional streams are hidden from the user. Here's 3 examples of alternate streams usage in Windows operating system: Favorites of Internet Explorer: When You add a Web site link into your 'Favorites', a .url file containing the url and description is created. However, if the Web site also have an icon (favicon), the icon is saved as alternate stream for the same url file. The stream name of the icon is :favicon:$DATA Downloaded files of Internet Explorer: When you download and save a file with Internet Explorer, it automatically add a zone information for the saved file. This zone information is used for identifying the file as downloaded file from the Internet. The stream name in this case is :Zone.Identifier:$DATA Summary information of files: When ... |
 |
9,394 | Nov 13, 2019 Nir Sofer  |
|
| Attack Surface Analyzer v2.3.299 Attack Surface Analyzer v2.3.299 A Microsoft developed open source security tool that analyzes the attack surface of a target system and reports on potential security vulnerabilities introduced during the installation of software or system misconfiguration. Attack Surface Analyzer 1.0 from Microsoft was released in 2012 and is no longer available. Attack Surface Analyzer 1.0 has been valuable to software developers and IT security personnel for years in helping detect key system changes that may occur from software installation. Attack Surface Analyzer 2 is a rewrite from the ground up on .NET Core and is an Open Source project managed by Microsoft. Scenarios 1) Attack Surface Analyzer can help identify potential security risks exposed through changes to services, user accounts, files, network ports, certificate stores, and the system registry. It also includes some support for “live” monitoring of certain system changes (i.e. file system and registry). 2) Another key use for the tool is in ensuring your software development process and products are following best practices for least privilege and reducing the attack surface for your customers by providing evidence, to your security and release teams, that your code does only what it claims. Maintaining customer trust is one reason why it is recommended from the Microsoft SDL Practices. Typical users of ASA: -DevOps Engineers - View changes to the system attack surface introduced when your software is installed. -IT Security Auditors - Evaluate risk presented when third-party software is installed. See How to Run Attack Surface Analyzer. System Requirements Operating System Support ASA is tested on Windows 11, Linux and MacOS systems. No installed pre-requisites or redistributables are required, beyond those of .NET Core. Additional OS compatibility for .NET Core is located here https://github.com/dotnet/core/blob/master/release-notes/3.1/3.1-supported-os.md. This download is for the Windows version. All other download assets are below: MacOS: ASA_macos_2.3.299.zip Linux: ASA_linux_2.3.299.zip NetCore: ASA_netcoreapp_2.3.299.zip Click here ... |
 |
5,051 | Jul 11, 2023 Microsoft Corp.  |
|
| Chainsaw v2.11.0 Chainsaw v2.11.0 Rapidly Search and Hunt through Windows Event Logs Chainsaw provides a powerful ‘first-response’ capability to quickly identify threats within Windows forensic artifacts such as Event Logs and the MFT file. Chainsaw offers a generic and fast method of searching through event logs for keywords, and by identifying threats using built-in support for Sigma detection rules, and via custom Chainsaw detection rules. Features 🎯 Hunt for threats using Sigma detection rules and custom Chainsaw detection rules 🔍 Search and extract forensic artefacts by string matching, and regex patterns 📅 Create execution timelines by analysing Shimcache artefacts and enriching them with Amcache data 💡 Analyse the SRUM database and provide insights about it ⬇️ Dump the raw content of forensic artefacts (MFT, registry hives, ESE databases) ⚡ Lightning fast, written in rust, wrapping the EVTX parser library by @OBenamram 🪶 Clean and lightweight execution and output formats without unnecessary bloat 🔥 Document tagging (detection logic matching) provided by the TAU Engine Library 📑 Output results in a variety of formats, such as ASCII table format, CSV format, and JSON format 💻 Can be run on MacOS, Linux and Windows See the Wiki for usage instructions. Changes v2.11.0 Improvements to the MFT parser, allowing data streams to be extracted, decoded and written to disk. Decoded MFT Datastreams can now be queried via the Search command and via the Hunt Command. This download is for the Windows version (very bottom of page). All other download assets are below: MacOS: chainsaw_x86_64-apple-darwin.zip chainsaw_aarch64-apple-darwin.zip Linux: chainsaw_x86_64-unknown-linux-gnu.tar.gz chainsaw_aarch64-unknown-linux-gnu.tar.gz Other: chainsaw_all_platforms+rules+examples.zip Click here to visit the author's website. |
 |
2,685 | Jan 29, 2025 F-Secure Countercept  |
|
| Combofix v19.11.4.1 Combofix v19.11.4.1 ComboFix is a program, created by sUBs, that scans your computer for known malware, and when found, attempts to clean these infections automatically. In addition to being able to remove a large amount of the most common and current malware, ComboFix also displays a report that can be used by trained helpers to remove malware that is not automatically removed by the program. Please note that running this program without supervision can cause your computer to not operate correctly. Therefore only run this program at the request of an experienced helper. Windows XP/Vista/7/8 32-bit program. Can run on both a 32-bit and 64-bit OS This program works with Windows 8, but not Windows 8.1 at this time and still no Windows 10 support. :( Click here to visit the author's website. |
 |
12,339 | Nov 13, 2019 sUBs  |
|
| CrowdInspect v1.7.0.0 CrowdInspect v1.7.0.0 A free community tool for Microsoft Windows systems that helps alert you to the presence of potential malware on your network. It is a host-based process inspection tool utilizing multiple sources of information to detect untrusted or malicious process and network-active applications. Beyond simple network connections, CrowdInspect associates the connection entry with the process that is responsible for that activity. CrowdInspect captures process name, the entry’s process ID number, local port, local IP address, remote port, remote IP address and reverse resolved DNS name of the remote IP address. CrowdInspect records details of any entry that is associated with a remote IP address and maintains a chronological list of those accessed. You may click the “Live/History” toolbar button to switch between the regular live process window and the network history list window. Click here to visit the author's website. |
 |
2,536 | Nov 09, 2021 CrowdStrike 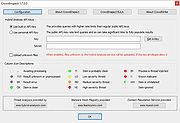 |
|
| HiJackThis+ v3.1.0.2 HiJackThis+ v3.1.0.2 The resurrection of one of our favorite virus/malware removal tools of all time! HiJackThis+ (Plus) (previously called: HiJackThis Fork v3) is a fork and a continuation of the original Trend Micro HiJackThis by Merijn Bellekom development, once a well-known tool. HiJackThis+ is a free utility for Microsoft Windows that scans your computer for settings changed by adware, spyware, malware and other unwanted programs. The difference from classical antiviruses is the ability to function without constant database updates, because HiJackThis+ primarily detects hijacking methods rather than comparing items against a pre-built database. This allows it to detect new or previously unknown malware - but it also makes no distinction between safe and unsafe items. Users are expected to research all scanned items manually, and only remove items from their PC when absolutely appropriate. Therefore, FALSE POSITIVES ARE LIKELY. If you are ever unsure, you should consult with a knowledgeable expert BEFORE deleting anything. HiJackThis+ is not a replacement of a classical antivirus. It doesn't provide a real-time protection, because it is a passive scanner only. Consider it as an addition. However, you can use it in form of boot-up automatic scanner in the following way: • Run the scanning • Add all items in the ignore-list • Set up boot-up scan in menu "File" - "Settings" - "Add HiJackThis to startup" • Next time when user logged in, HiJackThis will silently scan your OS and display UI if only new records in your system has been found. Features • Lists non-default settings in the registry, hard drive and memory related to autostart • Generates organized, easily readable reports • Does not use a database of specific malware, adware, etc • ... |
 |
2,555 | Jul 14, 2023 Alex Dragokas 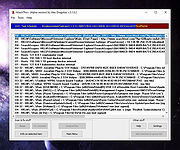 |
|
| hollows_hunter v0.3.4 hollows_hunter v0.3.4 Scans all running processes. Recognizes and dumps a variety of potentially malicious implants (replaced/implanted PEs, shellcodes, hooks, in-memory patches). Hollows Hunter allows you to scan your full system, searching for potentially malicious implants, and extract them for further analysis. It is an application based on PE-sieve (DLL version), so there is a big overlap of the features between those two. They have a similar command-line interface, but while PE-sieve is an engine dedicated to scanning a single process, Hollows Hunter offers many additional features and filters on the top of this base. More information about similarities and differences described here. Start by familiarizing yourself with PE-sieve by reading the PE-sieve's Wiki. Changes: v0.3.4 2-10-22 Updated PE-sieve (v0.3.4): Supported changes in the implementation of /mignore Supported new PE-sieve param: /threads: enabling scan of the threads' callstack . This is another layer of shellcode detection, allowing to capture "sleeping beacons", and others, decrypted just before the execution. This download is for the 64bit version. If you need the 32bit version, download here. Click here to visit the author's website. |
 |
3,921 | Feb 11, 2022 HASHEREZADE  |
|
| ImHex v1.36.2 ImHex v1.36.2 A modern hex editor and reverse engineering tool written in pure C++20 using GLFW and Dear ImGui. Features Features • Byte patching • Patch management • Copy bytes as feature -Bytes -Hex string -C, C++, C#, Rust, Python, Java & JavaScript array -ASCII-Art hex view -HTML self-contained div • String and hex search • Colorful highlighting • Goto from start, end and current cursor position Custom C++-like pattern language for parsing highlighting a file's content • Automatic loading based on MIME type • arrays, pointers, structs, unions, enums, bitfields, namespaces, little and big endian support, conditionals and much more! • Useful error messages, syntax highlighting and error marking Doesn't burn out your retinas when used in late-night sessions • Dark mode by default, but a light mode is available as well Data importing • Base64 files • IPS and IPS32 patches Data exporting ... |
 |
2,108 | Dec 30, 2024 WerWolv 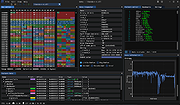 |
|
| Metadefender Client v4.1.20.56 Metadefender Client v4.1.20.56 Metadefender Cloud Client is the most thorough free malware analysis tool available. By running data through Metadefender Cloud, Cloud Client performs a deep endpoint forensic analysis for malware using several unique methods. Look for threats and assess the security state of your endpoint if you think it may be compromised. Methods: Memory Module Multi-Scanning: process and dynamic link library (DLL) analysis using over 40 anti-malware engines Local Anti-malware Analysis: a unique and effective analysis of anti-malware log files Rogue IP Detection: ensuring there are no network connections to a rogue IP address using several IP reputation sources Memory Module Multi-Scanning Running over 40 anti-malware engines that use heuristic detection, Metadefender Cloud Client analyzes all running processes and loaded memory modules. It performs a deep scan, analyzing the DLLs accessed by these processes for malware as well. This results in a deeper analysis than that of other free tools like Process Explorer or VirusTotal. And it does all this quickly – in just a few minutes. When you run it, Metadefender Cloud Client begins scanning all processes and DLL files for any threat. Once the analysis is complete, you’ll see a summary at the top of the window of how many potential threats of all kinds were identified. You’re able to click on each individual result and see the specific processes and DLLs that may be infected. Cloud Client is unique in allowing you to review the results on such a granular level. Highlight a process to see the results of the analysis. Click the arrow next to it in order to see the libraries accessed by the application while it runs. Then, click on individual DLL files to see the threats identified, and which specific anti-malware engines identified them. You can also see a list of potentially infected ... |
 |
5,663 | Nov 15, 2019 OPSWAT, Inc. 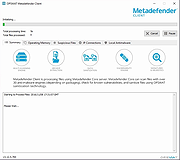 |
|
| Phrozen ADS (Alternate Data Stream) Revealer v1.0.5642 Phrozen ADS (Alternate Data Stream) Revealer v1.0.5642 Phrozen ADS (Alternate Data Stream) Revealer is a Microsoft Windows program, especially designed to reveal possible malicious ADS files in your file system. Since the Alternate Data Stream functionality is only available for NTFS (New Technology File System), the program is able to scan and detect this kind of files only for this type of file system (Physical Hard Drive/Virtual Hard Drive/Physical Removable Device/Virtual Removable Device). If some ADS Files are detected during the scan you then can decide wether or not you want to keep them or to back them up. You can also have a content preview to detect in one glance if it looks legitemate or not. Phrozen ADS Revealer is the perfect tool to sanitize your NTFS file systems against bloated content or hidden malwares. Another great tool to put in your collection and 100% free. What are Alternate Data Stream Alternate data streams allow more than one data stream to be associated with a filename, using the format "filename:streamname" (e.g., "text.txt:extrastream"). NTFS Streams were introduced in Windows NT 3.1, to enable Services for Macintosh (SFM) to store resource forks. Although current versions of Windows Server no longer include SFM, third-party Apple Filing Protocol (AFP) products (such as GroupLogic's ExtremeZ-IP) still use this feature of the file system. Very small ADS (called Zone.Identifier) are added by Internet Explorer and recently by other browsers to mark files downloaded from external sites as possibly unsafe to run; the local shell would then require user confirmation before opening them.[21] When the user indicates that they no longer want this confirmation dialog, this ADS is deleted. Alternate streams are not listed in Windows Explorer, and their size is not included in the file's size. They are ignored when the file is copied or moved ... |
 |
6,212 | Nov 15, 2019 PHROZEN SAS 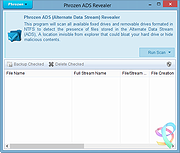 |
|
| RunPE Detector v2.0 RunPE Detector v2.0 Phrozen RunPE Detector is a security program, especially designed to detect and defeat some suspicious processes using a generic method. We at Phrozen Software do things differently, more creatively. So, when we set ourselves the task of creating a novel way of detecting, disabling and removing RATs, we didn't want to take the route every other anti-virus company has done before us. Phrozen Software studied the behaviour of RATs and discovered that hackers virtually always use a technique called RunPE. This technique spawns a legitimate process – often the default browser or a Microsoft system process – and replace it with a malicious program code directly in memory. Your computer is thus tricked and treats the malicious code as a legitimate process. The user and his anti-virus program have no idea that his default browser is effectively turned into a virus. RunPE is a technique that is used in several malicious ways. The two most common are : [1] FWB (Firewall Bypass): As its name suggests, this technique is implemented to bypass or disable the Application Firewall or the Firewall rules. Since most malware needs to connect to a remote Command-and-Control (C&C) Server, it needs to connect to the Internet via the Firewall. Since most users are connected to the Internet at home, normally the installed Firewall would prevent the malware from connecting to the Internet. Using the RunPE technique to hijack a legitimate process that is authorized to reach Internet, any malware could subsequently connect to the C&C without being detected by the Firewall. [2] Malware Packer or Crypter: Generally script kiddies – immature hackers - use a well-known type of malware that is already detected by most anti-virus programs. They then try the obfuscate this malware to evade ... |
 |
6,440 | Nov 15, 2019 PHROZEN SAS 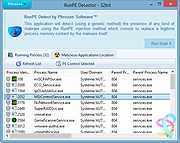 |
|
| SecureMyBit Deny v1.4 SecureMyBit Deny v1.4 SecureMyBit Deny is a simple, light and freeware security tool that permits you to deny execution of scripts that rely on Windows Script Host, perform impairment indicators analysis to detect possible malicious behaviours in analyzed executables, type your text safely against keyloggers, mouseloggers, screenloggers, etc. Then you can monitor your file system for changes and new files, detect processes that are connected to ports commonly used by malware and optimize security settings. (Please note that some antivirus or antimalware programs can detect SecureMyBit Deny as malware, we want to specify that this is a false positive, you can add SecureMyBit Deny to the exclusion list of your antivirus/antimalware). What’s new? Fixed heuristic engine false positive of EXE Analyzer (SecureMyBit Deny.exe) Changed ON/OFF text of File System Monitor button (Thanks @ticklemefeet for the suggestion) Fixed bug in Security Ports Scan Fixed critical bug of Text Editor Anti-Logger Fixed bug in File System Monitor Heuristic engine updated to improve ransomware detection, hash computing, decryption code and registry usage of analyzed EXE Added “Clear log” button to File System Monitor Key Features: Deny scripts execution Make USB read-only Text Editor Anti-Logger Perform EXE analysis Security Ports Scan Monitor File System easily Optimize security settings Terms & Conditions: WE AREN’T ABSOLUTELY RESPONSIBLE FOR ANY KIND OF PROBLEMS, DAMAGES, LOSS OF DATA, LOSS OF FILES OR ANY OTHER KINDS OF PROBLEMS. THE SOFTWARE IS PUBLISHED “AS IS”. THERE MAY BE FALSE POSITIVES IN EXE ANALYZER REPORT(S) BECAUSE OF THE HEURISTIC ANALYSIS. Thank you. SecureMyBit Development Team Compatibility Windows Vista Windows 7 Windows 8/8.1 Windows 10 Special Requirement: Microsoft .NET Framework 4.5 Languages: English SecureMyBit Deny Test: |
 |
5,070 | Nov 13, 2019 JM Security 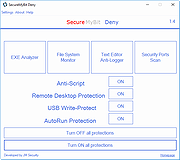 |
|
| SigcheckGUI v1.1.3 SigcheckGUI v1.1.3 GUI front-end for sigcheck.exe from Sysinternals. Scans for fake Root Certificates in Windows that malware uses to infect a computer. Supports: Win7 x32,Win7 x64,Win98,WinVista,WinVista x64,WinXP v1.1.3 - 2016-11-04 + SigcheckGUI now handles passed files and folders. (Thanks, zxhtrzdg) + Added "Clear unknown" to the Clear menu. * Changed/added some icons. * Verified SigcheckGUI works with sigcheck.exe v2.54. Click here to visit the author's website. |
 |
5,367 | Nov 15, 2019 Jody Holmes 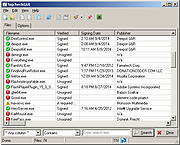 |
|
| Simple Software-restriction Policy v2.20 Simple Software-restriction Policy v2.20 A software policy makes a powerful addition to Microsoft Windows' malware protection. In particular, it is more effective against ransomware than traditional approaches to security. If you know about the Linux 'execute permission' bit then you'll understand what this is for. The mode of operation is somewhat different in that execute permission is granted to folders and subfolders rather than individual files, but the intention is the same, to stop undesirable or unknown software from launching unless you OK it. Additionally, it is possible to specify that certain executables (typically browsers and email clients) are run with reduced rights. This is a valuable damage-limitation measure against browser plugin vulns, etc. The protection can be turned off without a reboot whilst installing legitimate software, and will automatically reactivate after a specified time Click here to visit the author's website. |
 |
5,643 | Nov 15, 2019 IWR Consultancy  |
|
| Tron Script v12.0.6 Tron Script v12.0.6 A free collection of programs, tools, utilities, and Windows functions that are scripted together. It is designed to remove malware and bloatware, repair damaged operating systems, update old versions of very common applications, free up drive space by clearing out caches, and more. By consolidating and automating these tasks into a single execution it saves a lot of time and makes the whole process a more efficient. Tron's intended goal is to take a badly-running Windows PC (bloated, infected with malware, neglected, etc) and automate about 85% of the work involved in getting it to run well again. There is nothing Tron does which you couldn't do on your own without it. Tron's real power is in its automation and the breadth of tools that it uses to achieve its intended goal. While Tron can do a lot of good things for an affected PC, it is important to know that Tron is not a miracle cure-all. Tron is not a data recovery tool. It cannot recover files that were deleted or otherwise lost due to system failure or hardware failure. Tron is not a decryption tool. It cannot recover encrypted data such as files from an encrypted hard drive where you forgot the key, or if your computer was affected with ransomware. (Tron CAN remove the ransomware from your computer, but once your files have been encrypted the damage will have already been done.) Tron cannot solve bottlenecks that are inherent to your computer's hardware configuration. If your hardware is old, slow, or damaged, Tron cannot fix that. Tron is not a routine or preventative maintenance tool. As stated, the purpose of Tron is to automate a number of processes in order to get a badly ... |
 |
20,718 | Oct 18, 2023 vocatus  |
|
| Showing rows 1 to 16 of 16 | Showing Page 1 of 1 | 1 |
OlderGeeks.com Copyright (c) 2025