Buy our over-priced crap to help keep things running.




















| File - Download Chainsaw v2.11.0 | ||||||||
| Description | ||||||||
|
A plea... Deanna and I have been running this site since 2008 and lately we're seeing a big increase in users (and cost) but a decline in percentage of users who donate. Our ad-free and junkware-free download site only works if everyone chips in to offset the revenue that ads on other sites bring in. Please donate at the bottom of the page. Every little bit helps. Thank you so much. Sincerely, your Older Geeks: Randy and Deanna Always scroll to the bottom of the page for the main download link. We don't believe in fake/misleading download buttons and tricks. The link is always in the same place. Chainsaw v2.11.0 Rapidly Search and Hunt through Windows Event Logs Chainsaw provides a powerful ‘first-response’ capability to quickly identify threats within Windows forensic artifacts such as Event Logs and the MFT file. Chainsaw offers a generic and fast method of searching through event logs for keywords, and by identifying threats using built-in support for Sigma detection rules, and via custom Chainsaw detection rules. 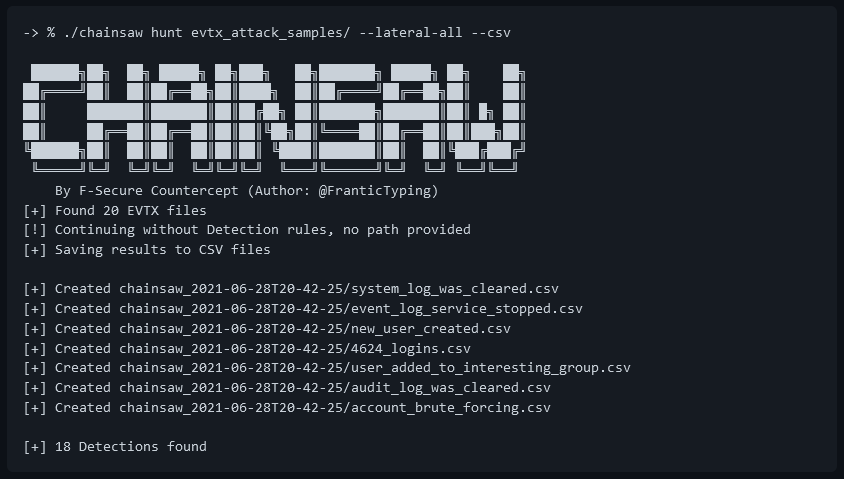 Features 🎯 Hunt for threats using Sigma detection rules and custom Chainsaw detection rules 🔍 Search and extract forensic artefacts by string matching, and regex patterns 📅 Create execution timelines by analysing Shimcache artefacts and enriching them with Amcache data 💡 Analyse the SRUM database and provide insights about it ⬇️ Dump the raw content of forensic artefacts (MFT, registry hives, ESE databases) ⚡ Lightning fast, written in rust, wrapping the EVTX parser library by @OBenamram 🪶 Clean and lightweight execution and output formats without unnecessary bloat 🔥 Document tagging (detection logic matching) provided by the TAU Engine Library 📑 Output results in a variety of formats, such as ASCII table format, CSV format, and JSON format 💻 Can be run on MacOS, Linux and Windows See the Wiki for usage instructions. Changes v2.11.0 Improvements to the MFT parser, allowing data streams to be extracted, decoded and written to disk. Decoded MFT Datastreams can now be queried via the Search command and via the Hunt Command.  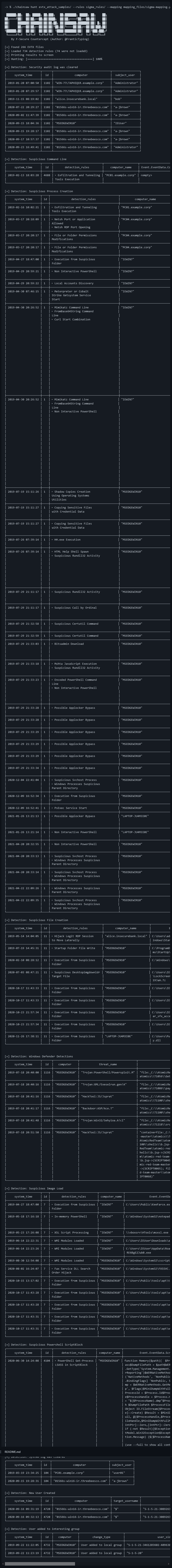 This download is for the Windows version (very bottom of page). All other download assets are below: MacOS: chainsaw_x86_64-apple-darwin.zip chainsaw_aarch64-apple-darwin.zip Linux: chainsaw_x86_64-unknown-linux-gnu.tar.gz chainsaw_aarch64-unknown-linux-gnu.tar.gz Other: chainsaw_all_platforms+rules+examples.zip Click here to visit the author's website. Continue below for the main download link. |
||||||||
| Downloads | Views | Developer | Last Update | Version | Size | Type | Rank | |
| 2,681 | 5,777 | F-Secure Countercept <img src="https://www.oldergeeks.com/downloads/gallery/thumbs/Chainsaw5_th.png"border="0"> | Jan 29, 2025 - 12:11 | 2.11.0 | 3.11MB | ZIP |  , out of 30 Votes. , out of 30 Votes. |
|
| File Tags | ||||||||
| Chainsaw v2.11.0 | ||||||||
Click to Rate File Share it on Twitter → Tweet
|