Buy our over-priced crap to help keep things running.




















| File - Download RunPE Detector v2.0 | ||||||||
| Description | ||||||||
|
A plea... Deanna and I have been running this site since 2008 and lately we're seeing a big increase in users (and cost) but a decline in percentage of users who donate. Our ad-free and junkware-free download site only works if everyone chips in to offset the revenue that ads on other sites bring in. Please donate at the bottom of the page. Every little bit helps. Thank you so much. Sincerely, your Older Geeks: Randy and Deanna Always scroll to the bottom of the page for the main download link. We don't believe in fake/misleading download buttons and tricks. The link is always in the same place. RunPE Detector v2.0 Phrozen RunPE Detector is a security program, especially designed to detect and defeat some suspicious processes using a generic method. We at Phrozen Software do things differently, more creatively. So, when we set ourselves the task of creating a novel way of detecting, disabling and removing RATs, we didn't want to take the route every other anti-virus company has done before us. Phrozen Software studied the behaviour of RATs and discovered that hackers virtually always use a technique called RunPE. This technique spawns a legitimate process – often the default browser or a Microsoft system process – and replace it with a malicious program code directly in memory. Your computer is thus tricked and treats the malicious code as a legitimate process. The user and his anti-virus program have no idea that his default browser is effectively turned into a virus. RunPE is a technique that is used in several malicious ways. The two most common are : [1] FWB (Firewall Bypass): As its name suggests, this technique is implemented to bypass or disable the Application Firewall or the Firewall rules. Since most malware needs to connect to a remote Command-and-Control (C&C) Server, it needs to connect to the Internet via the Firewall. Since most users are connected to the Internet at home, normally the installed Firewall would prevent the malware from connecting to the Internet. Using the RunPE technique to hijack a legitimate process that is authorized to reach Internet, any malware could subsequently connect to the C&C without being detected by the Firewall. [2] Malware Packer or Crypter: Generally script kiddies – immature hackers - use a well-known type of malware that is already detected by most anti-virus programs. They then try the obfuscate this malware to evade detection. In order to achieve this, they need to buy programs such as a Packer or a Crypter. The price depends on its ability to evade anti-virus programs, update intervals, the number of extra functions, etc. A Crypter will simply obfuscate or conceal the malicious code and an anti-virus program will fail to detect it. A Packer will add an extra compression step to make the malware smaller in size. It is then easier to to transfer or it can be virtually invisibly added to a legitimate process. Therefore, it will be harder to detect when it is downloaded to the victim's computer. Here, RunPE is used to uncrypt the malware in memory and to place it into a legitimate process without being written on the disc. More advanced techniques exists for Crypting and Packing malware, but since most creators of Crypters and/or Packers developed from common script kiddies that visited the same forums to get a basic knowledge, they all have learned to use the RunPE method. How does it work? Basically, the RunPE is a very simple method, but at the same time also very efficient. Yes, most commercial anti-virus heuristic scans detect this trick, but not everybody thinks a good commercial anti-virus solution is money well spent. When you really understand the RunPE injection method, you can easily imagine a way to get rid of most of the possible versions by using a Memory PE Headers Scan of each process and comparing the Memory PE Headers to the Process Image Path PE Header version. Since the Malware PE Header that has hijacked a legitimate process is very different from the legitimate process Image Path PE Header, we could detect the presence of a hijacked process. Is it efficient? Yes. After testing our program against several of the most used types of malware, the detection rate was good. (Against RunPE technique only) Since many RAT’s (Remote Administration Tools), Trojans, Backdoors Crypters and Packers are using RunPE to hide their suspicious activities, using our tool often is a first good step for making sure your system is clean from most destructive types of malware. Does it remove the Malware? Yes it can, but we cannot achieve a good success rate like for the detection process. It is easy to detect a hijacked process by the RunPE injection method, but it is much more difficult to detect what type of malware loaded the attack. To detect the presence of the malware on the disk we scan for all application files in the file system (.EXE, .COM, .BAT, .SCR, .PIF) and then compare their PE Headers to the malicious running process. If a malicious running process PE Header is similar to the current scanned file then we can assume we have detected the original file of infection. Since most of the time the injected malicious process file will be located inside a loader (or stub file) used to run the malicious code in memory, RunPE host detection failed often. To work, the malware loader must load itself to memory using RunPE andnot being Packed or Compressed. So how to remove if it doesn’t detect the host location? The first step is to install a (trial version of a) commercial anti-virus program and attempt a deep scan of the system. If the anti-virus program detects viruses, remove these viruses and then scan again using the RunPE Detector program to be sure it was successfully removed. If the anti-virus program doesn’t detect any infection, then manually kill the malicious detected process using RunPE Detector program and attempt to identify common malware installation location (Registry, Paths, Services, etc…) scan using our Phrozen VirusTotal Uploader each file you find suspicious. If, after all these tests, you don’t succeed in removing the threat, then do a backup of your important files and reinstall the entire system. What to do next? If RunPE Detector has found malicious programs in your system even if now 100% cleaned you must change all your passwords (bank accounts, browsers, games, applications, etc.). It is entirely possible that the hacker has already stolen all you credentials. Be sure to inform your bank to prevent your bank account being emptied.. Never download programs from unknown sources, be certainly careful when downloading and using cracks or keygens and open them only in a Virtual Machine or a Sandbox (Sandboxie for example). Buy and keep up-to-date a good anti-virus program. We recommend Kaspersky or Bitdefender as commercial anti-virus programs and COMODO Internet Security for Firewall. Important Notice: Never allow anti-virus programs to scan your files in the cloud for privacy reasons. This function should not even exist, so don’t accept! Does it support 64bit process scanning? It supports 64bit-systems, but not yet the scanning of 64bit-processes. We are planning to support that in the near future. Note that nowadays most malware still being compiled in 32bit-architecture, because most hackers feel more comfortable to code it and it still has a higher infection rate. Since 64bit-machines run 32bit-code there are no imminent reasons for malware developers to code both 64bit and 32bit-code. Changelog: 24 Apr 2017 — V2.0 General Project recoded from scratch Better Pe File / Memory analysis Faster analysis Stability and memory usage improved More efficient code to unlock and remove threats GUI Phrozen Material Support Added Sha1 : fd7ccee62d46e5e11cee1e64d2c9e4ad2896f313 Sha256 : 88de09dd4ed4a16d919a1ef26ac270c237e04743c4fd61aca423623beb8cec5a 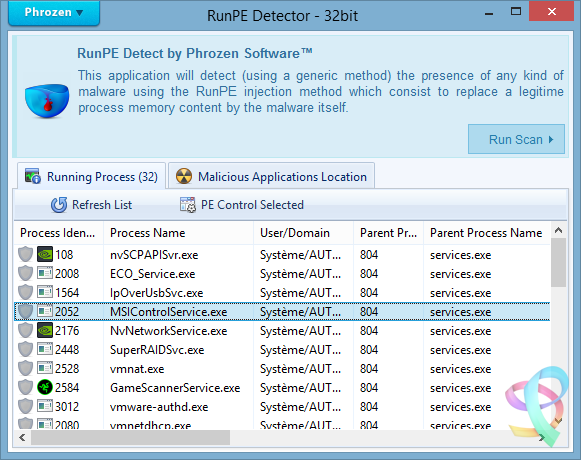 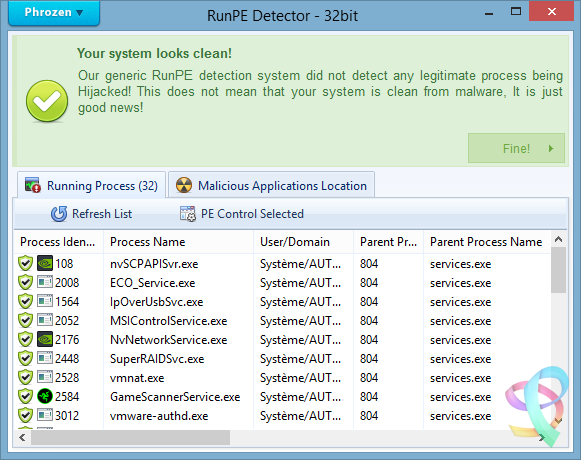 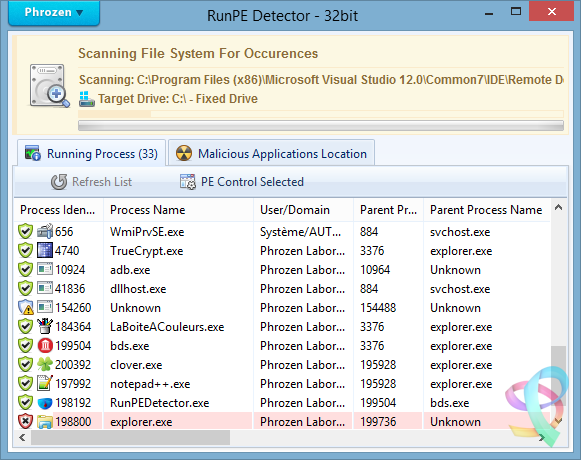 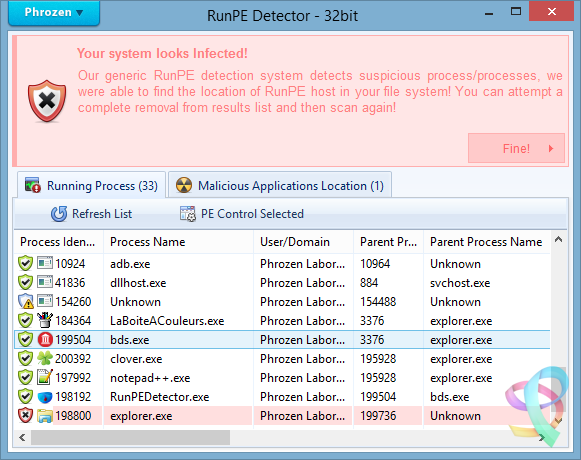 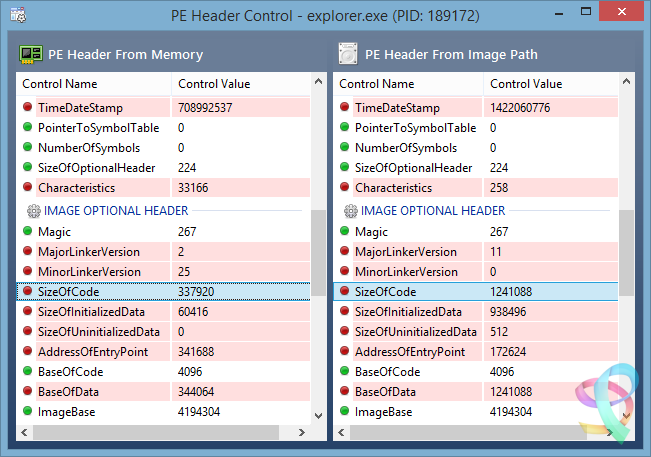 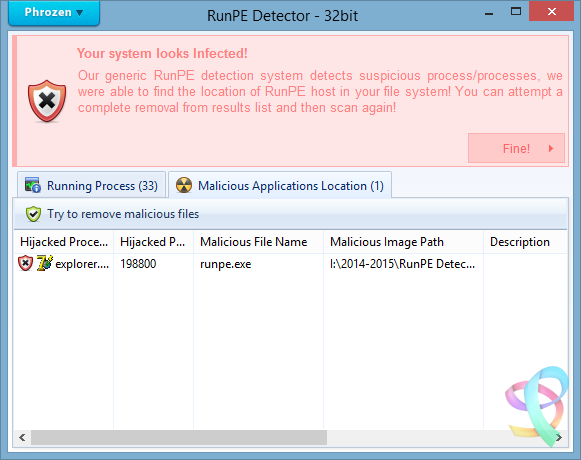 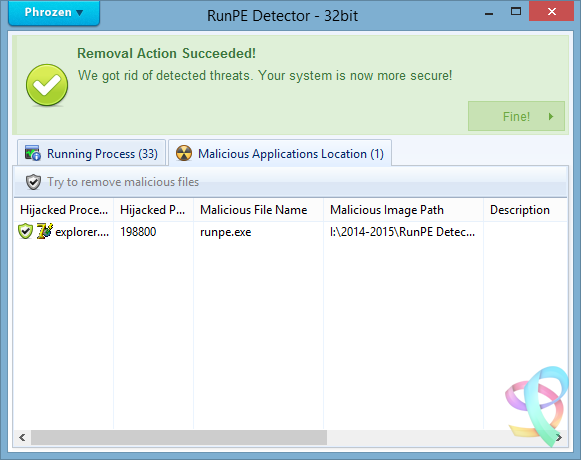 Click here to visit the author's website. Continue below for the main download link. |
||||||||
| Downloads | Views | Developer | Last Update | Version | Size | Type | Rank | |
| 6,437 | 13,264 | PHROZEN SAS <img src="https://www.oldergeeks.com/downloads/gallery/thumbs/RunPE Detector1_th.png"border="0"> | Nov 15, 2019 - 12:04 | 2.0 | 2.57MB | ZIP |  , out of 67 Votes. , out of 67 Votes. |
|
| File Tags | ||||||||
| v2.0 RunPE Detector | ||||||||
Click to Rate File Share it on Twitter → Tweet
|