Buy our over-priced crap to help keep things running.




















| File - Download Internet Processes Viewer v3.8.5.0 | ||||||||
| Description | ||||||||
|
A plea... Deanna and I have been running this site since 2008 and lately we're seeing a big increase in users (and cost) but a decline in percentage of users who donate. Our ad-free and junkware-free download site only works if everyone chips in to offset the revenue that ads on other sites bring in. Please donate at the bottom of the page. Every little bit helps. Thank you so much. Sincerely, your Older Geeks: Randy and Deanna Always scroll to the bottom of the page for the main download link. We don't believe in fake/misleading download buttons and tricks. The link is always in the same place. Internet Processes Viewer v3.8.5.0 Retrieves detailed snapshots of your computerís active TCP and UDP network connections along with the owning processes and users each time you run it. It gives quick results with a level of detail helpful when analyzing Cybersecurity incidents and troubleshooting network applications. SHA-256: 814fa4d55277e46a81ca07c110977191f521499989acbee2bff7e41d0b2d1c28 This application may be used at no cost after reading and accepting the built-in EULA. Typical write access to your interactive user's HKCU Software registry is required for the product license acceptance. Uniquely identify executable modules used in creating and maintaining suspicious network connections. Provide .csv reports from the application running on an endpoint of interest to your Cybersecurity support team. Intended target audience: Cybersecurity, Network, Systems Analysts, and similar technical users. Click the question mark in the upper right hand corner of the program for full instructions on it's use. Minimum system requirements Microsoft Windows 10 or 11 and .NET 6 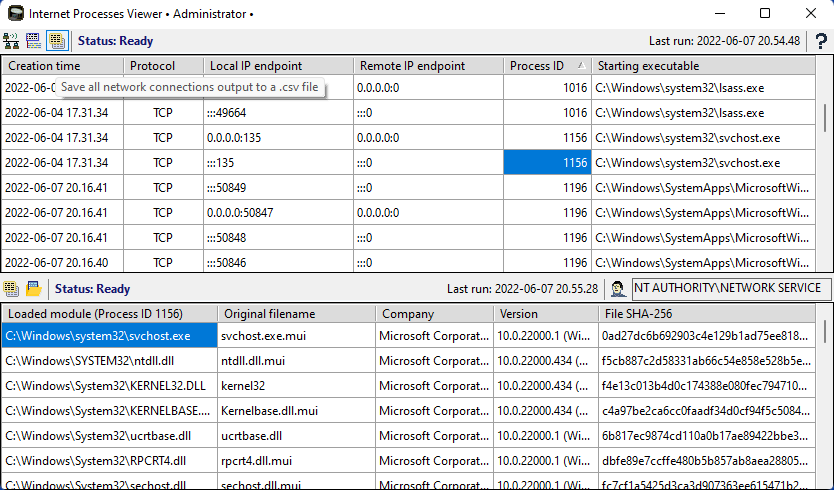 Click here to visit the author's website. Continue below for the main download link. |
||||||||
| Downloads | Views | Developer | Last Update | Version | Size | Type | Rank | |
| 3,416 | 6,491 | Steve Chaison Software <img src="https://www.oldergeeks.com/downloads/gallery/thumbs/InternetProcessesTracker_th.png"border="0"> | Jun 13, 2022 - 11:05 | 3.8.5.0 | 6.68MB | ZIP |  , out of 50 Votes. , out of 50 Votes. |
|
| File Tags | ||||||||
| Processes Internet Viewer v3.8.5.0 | ||||||||
Click to Rate File Share it on Twitter → Tweet
|