|
|

Your download link is at the very bottom of the page... always. |
Processed through Paypal No account required. |
Buy our over-priced crap to help keep things running.










|
|

Your download link is at the very bottom of the page... always. |
Processed through Paypal No account required. |










| Files | ||||
| File Name | Rating | Downloads | ||
 |
Hacker Hacker Hack your way through the security softwares and defeat your enemies! In Hacker you will control various programs that have different abilites. Your goal is to advance from node to node and try to defeat all the security programs that include guards, scanners and firewalls. Use your credits to buy more programs from shops around the map and fuse them together to create even more powerful versions. Take control of every server you get your hands on and shut down the national defense core! Play the arena mode and try to defeat as many waves of enemy programs as possible. The game was greatly inspired by an old flash game called The Nightfall Incident. You should go check that out too. controls: WASD to move around in the map menu LMB to do stuff |
 |
6,612 | Sep 28, 2016 Pixel Melody 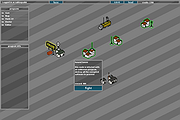 |
| Process Hacker v3.0.4706 Process Hacker v3.0.4706 A free, powerful, multi-purpose tool that helps you monitor system resources, debug software and detect malware. Graphs and statistics allow you quickly to track down resource hogs and runaway processes. Use Ctrl+I to view system performance information. Move your cursor over a graph to get a tooltip with information about the data point under your cursor. You can double-click the graph to see information about the process at that data point, even if the process is no longer running. Can't edit or delete a file? Discover which processes are using that file. Use Ctrl+F to search for a handle or DLL. If all else fails, you can right-click an entry and close the handle associated with the file. However, this should only be used as a last resort and can lead to data loss and corruption. See what programs have active network connections, and close them if necessary. Use Ctrl+I to view system performance information. Move your cursor over a graph to get a tooltip with information about the data point under your cursor. You can double-click the graph to see information about the process at that data point, even if the process is no longer running. See a hightly detailed overview of system activity with highlighting. Add extra columns to show even more system activity and information! Get real-time information on disk access. This may look very similar to the Disk Activity feature in Resource Monitor, but Process Hacker has a few more features! Get real-time information on disk usage. Enable disk statistics for detailed disk usage information. View detailed stack traces with kernel-mode, WOW64 and .NET support. Hover your cursor over the first column (with the numbers) to view parameter and line number information when available. Get real-time information on network usage. Enable network adapter statistics for detailed information network usage information. Go beyond services.msc: create, edit and control services. By default, ... |
 |
4,519 | Mar 24, 2022 Wen Jia Liu 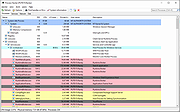 |
|
| Resource Hacker v5.2.8 Resource Hacker v5.2.8 A freeware resource compiler and decompiler for Windows applications. Resource Hacker is a resource editor for 32bit and 64bit Windows® applications. It's both a resource compiler (for *.rc files), and a decompiler - enabling viewing and editing of resources in executables (*.exe; *.dll; *.scr; etc) and compiled resource libraries (*.res, *.mui). While Resource Hacker is primarily a GUI application, it also provides many options for compiling and decompiling resources from the command-line. Compiling: Compiling can be initiated either by opening an existing resource script file, or by creating one from scratch using Resource Hacker's editor. A complete list of Resource-Definition Statements can be found here. Additional features of Resource Hacker's compiler include: The #INCLUDE directive (to access definition statements in header files etc) can be nested to multiple levels, as can the #IF, and #IFDEF directives. #DEFINE, #UNDEF, #IF, #ELIF, #ELSE, #IFDEF, #IFNDEF, #INCLUDE, and #PRAGMA directives are all supported. Strings, between double-quote (") characters, may contain typical 'C' style backslashed 'escaped' characters \t , , \\ , \" , \x, \u and \377 (octal). A double-quote within a string must be 'escaped' using either a preceding backslash or with another double-quote. Script comments are preceded either by double forward-slashes (//) or by a semi-colon (;). Filenames with relative paths are allowed. Filenames that contain spaces must be enclosed within double-quote characters. Compiler error messages are reported, even errors nested within INCLUDE statements... Viewing and Editing Resources: Once a resource file has been opened, its resources will generally be displayed as either an image (or group of images) or as decompiled text. Binary resources, usually images, can't be edited directly with Resource Hacker, but they can still be very easily exported and imported once they've been modified by an external image editor. (I see no benefit in duplicating what third-party image editors do ... |
 |
5,948 | Mar 06, 2025 Angus Johnson 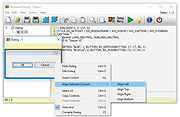 |
|
| Universal Radio Hacker v2.9.1 Universal Radio Hacker v2.9.1 The Universal Radio Hacker (URH) is a complete suite for wireless protocol investigation with native support for many common Software Defined Radios. URH allows easy demodulation of signals combined with an automatic detection of modulation parameters making it a breeze to identify the bits and bytes that fly over the air. As data often gets encoded before transmission, URH offers customizable decodings to crack even sophisticated encodings like CC1101 data whitening. When it comes to protocol reverse-engineering, URH is helpful in two ways. You can either manually assign protocol fields and message types or let URH automatically infer protocol fields with a rule-based intelligence. Finally, URH entails a fuzzing component aimed at stateless protocols and a simulation environment for stateful attacks. Download user guide here. Instructional Video: This download is for the Windows 64bit version. If you need the Windows 32bit version, download here. If you need the MacOS version, download here. If you need the Linux version, download here. Changes: v2.9.1 Dec 30, 2020 0c8f383 use *.wav format for demodulated signal export 8af7da3 change separation colors to green and magenta a3eceba fix disappearing separation area in demod view 6a7048c fix #829 7d2e41b fix overflow in AutoInterpretation for certain signals Click here to visit the author's website. |
 |
5,343 | Feb 11, 2021 Dr. Johannes Pohl 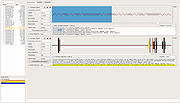 |
|
| Showing rows 1 to 4 of 4 | Showing Page 1 of 1 | 1 |
OlderGeeks.com Copyright (c) 2025