Buy our over-priced crap to help keep things running.




















| Files | ||||
| File Name | Rating | Downloads | ||
| BMP Wrap 2.0 BMP Wrap 2.0 Ever needed to email a file but it keeps on bouncing because it's an illegal attachment? Renaming the file or storing it in a ZIP archive sometimes works, but many ISP can detect that low-tech obfuscation. You need BMP Wrap. BMP Wrap temporarily hides a file inside a valid .BMP image. Once hidden, you can send the BMP file to anybody you wish and they can then extract that file from the BMP image using BMP Wrap. Now you can send EXEs, DLLs, or whatever file format you want, and the destination mail server will never be the wiser. No installation is required - just save the EXE file to your desktop, and then drag the file you want to wrap/unwrap onto the the BMPWrap Icon (a new .BMP file is created, the original file is left unmodified). This program is free & does not include any ad-ware or other malware. |
 |
5,263 | Jan 27, 2017 HCI Design  |
|
| Crypter Geek 2.0 Crypter Geek 2.0 Encrypt / Decrypt text files by this mysterious encryption tool, No installation required. Warning: Windows Defender and other anti-malware programs may incorrectly detect this as malicious. It is a clean file. |
 |
6,211 | Feb 25, 2017 Christos Beretas  |
|
| DeepSound 2.0 DeepSound 2.0 DeepSound is a steganography tool and audio converter that hides secret data into audio files. The application also enables you to extract secret files directly from audio files or audio CD tracks. DeepSound might be used as copyright marking software for wave, flac, wma, ape, and audio CD. DeepSound also support encrypting secret files using AES-256(Advanced Encryption Standard) to improve data protection. The application additionally contains an easy to use Audio Converter Module that can encode several audio formats (FLAC, MP3, WMA, WAV, APE) to others (FLAC, MP3, WAV, APE). System requirements: - Windows XP/Vista/7/8 - Microsoft .NET Framework 3.5 Documentation: 1 DeepSound 2.0 1.1 Hide data into carrier audio file To hide data into audio file, follow these steps: Select carrier audio file or drag and drop audio file (flac, wav, wma, mp3, ape) into the file explorer. Click to 'Add files' or drag and drop secret files into the panel on the right side of application. Press F3 key or click to encode secret files. You can choose output audio format (wav, flac or ape). DeepSound does not support wma output format. If you want to hide data into wma, hide secret data into wav file and then use external software such as Windows Media Encoder for convert wav to wma lossless file. In settings dialog you can turn On/Off encrypting and set password. Modified audio file will be copied to output directory. Click Ok to start hiding secret files into carrier audio file. 1.2 Extract secret data from audio file or audio CD track To extract secret data from audio file, follow these steps: In the file explorer, select audio file or audio CD track, which contains secret data. If the secret files are encrypted, enter ... |
 |
6,287 | Mar 16, 2016 Jozef Bátora  |
|
| Naval Battle 2.0 Naval Battle 2.0 The fantastic battleship table game for your computer. Features Very intuitive graphics animated game It has three types of game mode: Single Player, Two on Same computer and Multi Player Now with an updated and brilliant design It includes a lot of great features |
 |
5,619 | Aug 26, 2016 bruno256 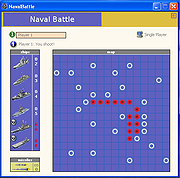 |
|
| Terminal Wings 2.0 Terminal Wings 2.0 Give wings to your insipid Windows Terminal. Have you ever been dreaming about having a marvelous Microsoft Windows Terminal, something that's at the same time beautiful, time saving and better to organize when you need to work on several terminals at the same time. Don’t search furthermore: Terminal Wings is the application you were searching for. Already in its very first version it's very complete and powerful. Imagine what power you could harness in the near future. How does it work? Contrary to other applications which simply try to replicate the same efficiency of the embedded Windows Terminal coded by Microsoft, our Terminal Wings is not such an emulator which “Hooks” the process of a real terminal to 'copy/paste' the screen buffer and display its contents to the custom application frame. It also doesn't create virtual pipes to redirect output/input buffers (stdout ; stdin ; stderror) to capture send and capture terminal commands. The reason we don’t use both above methods is due to the instability of such methods. When you execute regular commands it works pretty fine, but when it comes to use more complex console programs it become quite unstable (depending of the emulator you use). So , what is our solution? Very basically, we do not emulate the Windows Terminal at all, but we use the real one. We Patch the window and associated messages and embed it into our own frame. Well, this might sound very easy, but in effect it is quite complex to code if you want to make it appear very smoothly. Important Notice: At this moment in time, the application is only available for Microsoft Windows 10. Depending on the initial success of this program, we might be tempted to support other Windows versions too. Current Functions Available Multi Tabs : Organise your terminals using ... |
 |
5,554 | Nov 15, 2019 Phrozen Software  |
|
| ToolTipFixer 2.0 ToolTipFixer 2.0 Ever since Microsoft invented the Windows Shell with explorer.exe back in the days of Windows 95, there's been a bug that's gone from one version of Windows to the next; and with each upgrade it became worse and worse - until Vista where it only rears its ugly head every once in a while instead: tooltips appear behind the taskbar, where you can't read them and they are of no use to you. And there's nothing you can do about it! NST ToolTipFixer patches this bug for once and for all, doing what Microsoft hasn't been able to do in 13 years. ToolTipFixer 2.0 (October 14, 2008) Installer options for service vs. application Minimize memory usage as much as possible Create standalone ToolTipFixer module Remove .NET Dependencies |
 |
5,321 | May 23, 2017 NeoSmart Technologies  |
|
| Windows Firewall Notifier 2.0 Windows Firewall Notifier 2.0 Windows Firewall Notifier extends the default Windows embedded firewall behavior, allowing it to handle real time connections monitoring, connections map, bandwidth usage monitoring. Requirements WFN requires Windows Vista SP2 or later (Windows 7, 8, 8.1, 10...) with Microsoft .NET 4.5.2 or higher. Windows Server 2008 or later are not officially supported, but WFN should work fine on them. Connections listing Real time connections mapping with routes Bandwidth monitoring Adapters information Windows Firewall status management Notification popup for unknown outgoing connections (optional) |
 |
8,985 | Mar 14, 2017 Daniel Pharos  |
|
| Windows License Key Dump 2.0 Windows License Key Dump 2.0 Windows License Key Dump is the free command-line tool to recover the product/serial Keys of Windows and other popular software. It automatically detects and decrypts the license/serial keys of over 200+ popular software programs including Office, SQL Server, Adobe, Nero and many more. Being a command-line tool makes it useful for penetration testers and forensic investigators. |
 |
9,205 | Feb 10, 2014 Security Xploded |
|
| Windows USB Blocker 2.0 Windows USB Blocker 2.0 Windows USB Blocker is the free tool to quickly Block or Unblock USB Storage Devices on any Windows system. USB devices are one of the primary causes for spreading virus/malware from one system to another without the user knowledge. Often it is risky to allow others to insert USB stick (often infected with virus) into your system. Hence it is always advised to disable USB when you are not around. In such cases, Windows USB Blocker tool will help you to instantly block USB and safeguard your system from these viruses. Beauty of this tool is that it will block only USB Storage devices like USB Sticks or Portable Disks. However normal USB devices like wireless keyboard/mouse plugs, bluetooth/wireless/internet dongles will continue to work without any problem. It has cool GUI interface and very simple to use for everyone. With just one click you can instantly Block or Unblock USB on your system. It is fully portable and does not require JAVA or .NET components. It is successfully tested on all platforms starting from Windows XP to Windows 8. Features Free Tool to block or unblock USB Blocks only USB Storage Devices (USB Sticks/Disks) Simple tool with cool GUI interface Displays current USB block status No need to log off or restart the system Fully portable, does not require any .NET or other dependencies Includes Installer for local installation & un-installation Works on both 32-bit & 64-bit systems from Windows XP to Windows 8 Changelog: Version 2.0 : 10th Feb 2015 Integrated Uninstaller into Windows Add/Remove Programs, now you can uninstall it in a standard way. |
 |
6,796 | Feb 13, 2015 SecurityXploded |
|
| Winkey Finder 2.0 Beta 1 Winkey Finder 2.0 Beta 1 Win Keyfinder 2.0 retrieves your Microsoft Windows 7, Windows 8, Windows 8.1, windows XP, windows 2000, windows ME, 98, 2003 and .NET both 32bit and 64bit Operating system Product keys from the registry and display it for you. It does not generate any product key it merely displays the key stored in registry. It also retrieves Microsoft Office Product key stored in registry. Here are some features of Win Keyfinder 2.0: View Windows 8 and Windows 8.1 Product CD Key View/change XP Key View Windows 7 Product/CD Keys. View Windows Vista Product Key View/Change MS office Key View Win98 Key view Win2000 Key View .Net Key View Win2003 Key Check Activation Status (WinXP) / Coming soon Win 7/Vista Save Your Product Key By Encrypting It De-Crypt your saved encrypted key Support for MS Office Product keys |
 |
6,774 | Mar 13, 2015 Winkey Finder |
|
| WMI Explorer 2.0 WMI Explorer 2.0 WMI Explorer is a utility intended to provide the ability to browse and view WMI namespaces/classes/instances/properties in a single pane of view and is inspired by the PowerShell based WMI Explorer written by Marc. As someone who works with Configuration Manager (SCCM), I spend a lot of time in wbemtest trying to find things which is very time consuming. I started this project with the intention to combine the features of currently available WMI Explorers, and to make it easier and quicker to find what you're looking for in WMI. WMI Explorer is a utility intended to provide the ability to browse and view WMI namespaces/classes/instances/properties in a single pane of view and is inspired by the PowerShell based WMI Explorer written by Marc. As someone who works with Configuration Manager (SCCM), I spend a lot of time in wbemtest trying to find things which is very time consuming. I started this project with the intention to combine the features of currently available WMI Explorers, and to make it easier and quicker to find what you're looking for in WMI. Requirements * Microsoft .NET Framework 4.0 Full or .NET Framework 4.5.1 * Minimum display resolution: 1024x768 * Administrator rights to view some WMI objects * (Optional) Internet access for automatic update check Features * Browse and view WMI objects in a single pane of view. * Connect as alternate credentials to remote computers. * Asynchronous and Synchronous mode for enumeration. * Method execution. * SMS (Configuration Manager) mode providing additional functionality for Configuration Manager. * Filter classes and instances matching specified criteria. * View classes/instances in Managed Object Format (MOF). * Search classes, methods and properties for names matching specified criteria. * Run WQL queries. * Automatic generation of WQL query for the selected Class/Instance. * Automatic script creation (PowerShell and VBS). * Highlighting enumerated objects. * Display property descriptions and possible enumeration values (if available). * Display methods descriptions ... |
 |
5,944 | May 06, 2016 Vinpa  |
|
| Showing rows 1 to 11 of 11 | Showing Page 1 of 1 | 1 |
OlderGeeks.com Copyright (c) 2025