|
|

Your download link is at the very bottom of the page... always. |
Processed through Paypal No account required. |
Buy our over-priced crap to help keep things running.










|
|

Your download link is at the very bottom of the page... always. |
Processed through Paypal No account required. |










| File - Download Microsoft Sysmon v15.15 | ||||||||
| Description | ||||||||
|
A plea... Deanna and I have been running this site since 2008 and lately we're seeing a big increase in users (and cost) but a decline in percentage of users who donate. Our ad-free and junkware-free download site only works if everyone chips in to offset the revenue that ads on other sites bring in. Please donate at the bottom of the page. Every little bit helps. Thank you so much. Sincerely, your Older Geeks: Randy and Deanna Always scroll to the bottom of the page for the main download link. We don't believe in fake/misleading download buttons and tricks. The link is always in the same place. Microsoft Sysmon v15.15 A Windows system service and device driver that, once installed on a system, remains resident across system reboots to monitor and log system activity to the Windows event log. It provides detailed information about process creations, network connections, and changes to file creation time. By collecting the events it generates using Windows Event Collection or SIEM agents and subsequently analyzing them, you can identify malicious or anomalous activity and understand how intruders and malware operate on your network. 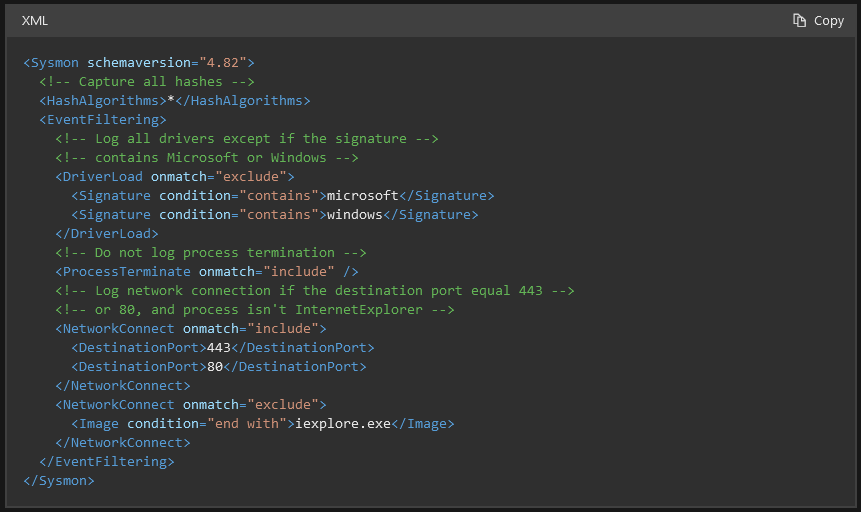 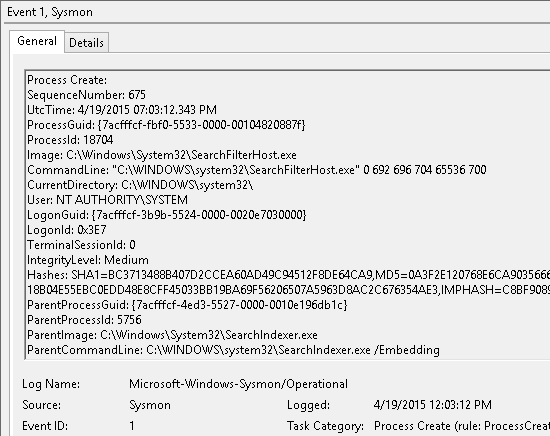 Note that Sysmon does not provide analysis of the events it generates, nor does it attempt to protect or hide itself from attackers. Overview of Sysmon Capabilities Sysmon includes the following capabilities: • Logs process creation with full command line for both current and parent processes. • Records the hash of process image files using SHA1 (the default), MD5, SHA256 or IMPHASH. • Multiple hashes can be used at the same time. • Includes a process GUID in process create events to allow for correlation of events even when Windows reuses process IDs. • Includes a session GUID in each event to allow correlation of events on same logon session. • Logs loading of drivers or DLLs with their signatures and hashes. • Logs opens for raw read access of disks and volumes. • Optionally logs network connections, including each connection’s source process, IP addresses, port numbers, hostnames and port names. • Detects changes in file creation time to understand when a file was really created. Modification of file create timestamps is a technique commonly used by malware to cover its tracks. • Automatically reload configuration if changed in the registry. • Rule filtering to include or exclude certain events dynamically. • Generates events from early in the boot process to capture activity made by even sophisticated kernel-mode malware. Usage Common usage featuring simple command-line options to install and uninstall Sysmon, as well as to check and modify its configuration: Install: sysmon64 -i [<configfile>] Update configuration: sysmon64 -c [<configfile>] Install event manifest: sysmon64 -m Print schema: sysmon64 -s Uninstall: sysmon64 -u [force] Parameter and Description -i Install service and driver. Optionally take a configuration file. -c Update configuration of an installed Sysmon driver or dump the current configuration if no other argument is provided. Optionally takes a configuration file. -m Install the event manifest (implicitly done on service install as well). -s Print configuration schema definition. -u Uninstall service and driver. Using -u force causes uninstall to proceed even when some components are not installed. The service logs events immediately and the driver installs as a boot-start driver to capture activity from early in the boot that the service will write to the event log when it starts. On Vista and higher, events are stored in Applications and Services Logs/Microsoft/Windows/Sysmon/Operational. On older systems, events are written to the System event log. If you need more information on configuration files, use the -? config command. Specify -accepteula to automatically accept the EULA on installation, otherwise you will be interactively prompted to accept it. Neither install nor uninstall requires a reboot. Examples Install with default settings (process images hashed with SHA1 and no network monitoring) cmd sysmon -accepteula -i Install Sysmon with a configuration file (as described below) cmd sysmon -accepteula -i c:\windows\config.xml Uninstall cmd sysmon -u Dump the current configuration cmd sysmon -c Reconfigure an active Sysmon with a configuration file (as described below) cmd sysmon -c c:\windows\config.xml Change the configuration to default settings cmd sysmon -c -- Show the configuration schema cmd sysmon -s Go here for Event ID descriptions: https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon#events Click here to visit the author's website. Continue below for the main download link. |
||||||||
| Downloads | Views | Developer | Last Update | Version | Size | Type | Rank | |
| 5,833 | 18,989 | Microsoft Corp. <img src="https://www.oldergeeks.com/downloads/gallery/thumbs/Sysmon1_th.png"border="0"> | Feb 12, 2025 - 12:08 | 15.15 | 4.64MB | ZIP |  , out of 91 Votes. , out of 91 Votes. |
|
| File Tags | ||||||||
| Sysmon v15.15 Microsoft | ||||||||
|
Click to Rate File Share it on Twitter → Tweet
|