Buy our over-priced crap to help keep things running.




















| Files | ||||
| File Name | Rating | Downloads | ||
| 29 Avast Ransomware Decryption Tools 29 Avast Ransomware Decryption Tools Avast has created 29 different tools to decrypt your files encrypted by the following ransomware variants. This is a zip file containing all 29 of them. AES_NI Alcatraz Locker Apocalypse AtomSilo Babuk BadBlock Bart BigBobRoss BTCWare Crypt888 CryptoMix (Offline) CrySiS EncrypTile FindZip Fonix GandCrab Globe HiddenTear Jigsaw LambdaLocker Legion LockFile NoobCrypt Stampado SZFLocker TeslaCrypt Troldesh / Shade XData Click here to visit the author's website. |
 |
4,413 | Oct 28, 2021 Avast Software s.r.o.  |
|
| 80 Emsisoft Ransomware Decryption Tools v1.0 80 Emsisoft Ransomware Decryption Tools v1.0 Unlock your files without paying the ransom This is a compilation of all 80 of Emsisoft's free ransomware decryption tools compiled by OlderGeeks.com. Please note: Due to the nature of decryption tools sometimes carrying ransomware samples to do their work, some antivirus programs may detect viruses in these tools. It is recommended that you disable your antivirus software to use these tools. You may also have to disable your antivirus to unzip the file without any of the tools being deleted. The following tools are included in this zip file: Emsisoft Decryptor for Ragnarok Emsisoft Decryptor for SynAck Emsisoft Decryptor for Ziggy Emsisoft Decryptor for Cyborg Emsisoft Decryptor for Crypt32 Emsisoft Decryptor for CheckMail7 Emsisoft Decryptor for SpartCrypt Emsisoft Decryptor for Zorab Emsisoft Decryptor for RedRum Emsisoft Decryptor for JavaLocker Emsisoft Decryptor for KokoKrypt Emsisoft Decryptor for Ransomwared Emsisoft Decryptor for ChernoLocker Emsisoft Decryptor for TurkStatik Emsisoft Decryptor for Hakbit Emsisoft Decryptor for Jigsaw Emsisoft Decryptor for Paradise Emsisoft Decryptor for STOP Puma Emsisoft Decryptor for STOP Djvu Emsisoft Decryptor for Muhstik Emsisoft Decryptor for HildaCrypt Emsisoft Decryptor for GalactiCrypter Emsisoft Decryptor for Avest Emsisoft Decryptor for WannaCryFake Emsisoft Decryptor for Syrk Emsisoft Decryptor for JSWorm 4.0 Emsisoft Decryptor for LooCipher Emsisoft Decryptor for ZeroFucks Emsisoft Decryptor for Ims00rry Emsisoft Decryptor for GetCrypt Emsisoft Decryptor for JSWorm 2.0 Emsisoft Decryptor for MegaLocker Emsisoft Decryptor for ZQ Emsisoft Decryptor for CryptoPokemon Emsisoft Decryptor for Planetary Emsisoft Decryptor for Aurora Emsisoft Decryptor for HKCrypt Emsisoft Decryptor for PewCrypt Emsisoft Decryptor for BigBobRoss Emsisoft Decryptor for NemucodAES Emsisoft Decryptor for Amnesia2 Emsisoft Decryptor for Amnesia Emsisoft Decryptor for Cry128 Emsisoft Decryptor for Cry9 Emsisoft Decryptor for Damage Emsisoft Decryptor for CryptON Emsisoft Decryptor for MRCR Emsisoft Decryptor for Marlboro Emsisoft Decryptor for Globe3 Emsisoft Decryptor for OpenToYou Emsisoft Decryptor for GlobeImposter Emsisoft Decryptor for NMoreira Emsisoft Decryptor for OzozaLocker Emsisoft Decryptor for Globe2 Emsisoft Decryptor for Globe Emsisoft Decryptor for Al-Namrood Emsisoft Decryptor for FenixLocker Emsisoft Decryptor for Fabiansomware Emsisoft Decryptor for Philadelphia Emsisoft Decryptor for Stampado Emsisoft Decryptor for ApocalypseVM Emsisoft Decryptor for Apocalypse Emsisoft Decryptor for BadBlock Emsisoft Decryptor for Xorist Emsisoft Decryptor for 777 Emsisoft Decryptor for AutoLocky Emsisoft Decryptor for Nemucod Emsisoft Decryptor ... |
 |
2,717 | Oct 16, 2021 Emsisoft Ltd 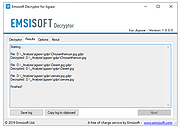 |
|
| Bitdefender Ransomware Recognition Tool v1.0.0.2 Bitdefender Ransomware Recognition Tool v1.0.0.2 A tool to help ransomware victims find which family and sub-version of ransomware has encrypted their data and then get the appropriate decryption tool, if it exists. Ransomware has grabbed the headlines ever since 2014. While most ransomware attacks can’t be defeated, Bitdefender constantly creates and updates ransomware decryption tools for families that have either vulnerable encryption algorithms or for which a master decryption key has been leaked. This tool analyzes both the ransom note and the encrypted file samples to identify the strain of ransomware and suggest a decryption tool for the identified family, if such a tool is available. Step 1 Download the BRR tool and save it somewhere on your computer. The latest version is always available here. This tool requires an active internet connection. Step 2 Run the BDRansomRecognitionTool.exe and allow it to execute if prompted by an UAC alert. Step 3 Read and agree to the End User License Agreement Step 4 The application has two fields to fill in: Choose the path to the ransom note file or the path to a folder containing encrypted files. You can choose either option, but the tool needs at least one of the pieces of information to detect which strain of ransomware has encrypted your information. If none of the fields are filled in, you cannot proceed any further Step 5 Press Scan. The application gives a warning if the ransom-note path is not filled in, as the detection accuracy is slightly lower in this case. The content of the ransom note is submitted for analysis to Bitdefender cloud. If the user provides any encrypted file, NO file content will be submitted to our cloud, as the tool only analyzes the filename and its extension. If the ransomware family cannot be identified, the user is informed about this. In some cases, multiple families of ransomware display similar features. ... |
 |
5,428 | Nov 13, 2019 BitDefender Labs 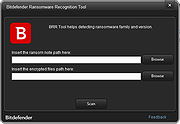 |
|
| Emsisoft Decryptor for Paradise v1.0.0.1 Emsisoft Decryptor for Paradise v1.0.0.1 The Paradise ransomware encrypts victims using Salsa20 and RSA-1024, and appends one of several extensions such as ".paradise", "2ksys19", ".p3rf0rm4", ".FC", ".CORP", and ".STUB" An example ransom note "---==%$$$OPEN_ME_UP$$$==---.txt" can be found below. WHAT HAPPENED! Your important files produced on this computer have been encrypted due a security problem. If you want to restore then write to the online chat. Contact! Online chat: http://prt-recovery.support/chat/6-Support Your operator: Support Your personal ID: [redacted] Enter your ID and e-mail in the chat that you would immediately answered. Attention! Do not rename encrypted files. Do not try to decrypt your data using third party software, it may cause permanent data loss. Do not attempt to use the antivirus or uninstall the program. This will lead to your data loss and unrecoverable. Decoders of other users is not suitable to decrypt your files - encryption key is unique. How to use the Emsisoft Decryptorfor Paradise MPORTANT! Be sure to quarantine the malware from your system first, or it may repeatedly lock your system or encrypt files. If your current antivirus solution fails to detect the malware, it can be quarantined using the free trial version of Emsisoft Anti-Malware. If your system was compromised through the Windows Remote Desktop feature, we also recommend changing all passwords of all users that are allowed to login remotely and check the local user accounts for additional accounts the attacker might have added. How to decrypt your files 1. Download the decryptor from the same site that provided this “How To” document. 2. Run the decryptor as an administrator. The license terms will show up next, which you have to agree to by clicking the “Yes” button: 3. After accepting the terms, select your file pair using the “Browse” buttons. Then, click the “Start” button. 4. The decryptor will display the reconstructed encryption details once the recovery process has finished. The display is purely informational ... |
 |
3,927 | Jan 21, 2020 Emisoft 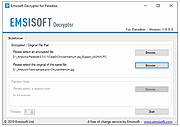 |
|
| ESET TeslaCrypt Decryptor v1.1.0.1 ESET TeslaCrypt Decryptor v1.1.0.1 ESET® released a decryptor for recent variants of the TeslaCrypt ransomware. If you have been infected by one of the new variants (v3 or v4) of the notorious ransomware TeslaCrypt and the encrypted files have the extensions .xxx, .ttt, .micro, .mp3 or remained unchanged, then ESET has good news for you. Recently, TeslaCrypt’s operators have announced they are wrapping up their malicious activities. On this occasion, one of ESET’s analysts anonymously contacted the group, using the official support channel offered to the ransomware victims by the TeslaCrypt’s operators and requested the universal master decryption key. Surprisingly, they made it public. This has allowed ESET to promptly create a free decrypting tool capable of unlocking files affected by all variants of this ransomware. How do I clean a TeslaCrypt infection using the ESET TeslaCrypt decrypter? Issue Your personal files became encrypted and the following information may be displayed in your computer, or in a .txt, .html or .png file Your ESET product detects the infection Win32/Filecoder.TeslaCrypt How to decrypt your files using the ESETTeslaCryptDecryptor.exe tool Solution Download the ESETTeslaCryptDecryptor.exe tool and save the file to your Desktop. Click Start → All Programs → Accessories, right-click Command prompt and then select Run as administrator from the context menu. Windows 8 / 8.1 / 10 users: press the Windows key + Q to search for applications, type Command prompt into the Search field, right-click Command prompt and then select Run as administrator from the context menu. Type the command cd %userprofile%\Desktop (do not replace "userprofile" with your username–type the command ... |
 |
5,998 | Nov 13, 2019 ESET  |
|
| TeslaDecoder 1.0.1 TeslaDecoder 1.0.1 TeslaDecoder has the ability to decrypt all variants of the TeslaCrypt ransomware. This includes the following extensions: .micro, .xxx, .ttt, .mp3, and also encrypted files that have not had their file extensions changed. For older versions of the TeslaCrypt ransomware, when run TeslaDecoder, it will search for particular Windows registry keys, the storage.bin file, or key.dat file, and if it finds these keys, it will attempt to extract the decryption key. If a decryption key is extracted it can then decrypt all of the files in a designated folder or all files on a system. Some victim's of this ransomeware have had the decryption key stripped from the data files. In this case, TeslaDecoder will not be able to help you decrypt your files. For the newest versions of the TeslaCrypt ransomeware (The most common), read the instructions contained in the download package to decrypt your files. Changelog for TeslaDecoder, TeslaViewer and TeslaRefactor --------------------------------------------------------- **************** * TeslaDecoder * **************** ========== = 1.0.1 = ========== - Removed check of a value at offset 0x08 for TeslaCrypt 3/4 encrypted files ========== = 1.0.0 = ========== - Added 4th PrivateKyTesla into TeslaDecoder. All files encrypted by TeslaCrypt 3.0.0 - 4.2 can be decrypted. The key is predefined when extension of TeslaCrypt 3/4 is choosen in Set key dialog. ========== = 0.0.91 = ========== - Decrypt list - If listed file doesn't have TeslaCrypt extension, the file extension is not changed. ========== = 0.0.90 = ========== - Added support for listing encrypted files and decryption of listed files in the list file. - GUI changes - Log changes - Internal changes - README.txt rewritten ========== = 0.0.85 = ========== - Added support for TeslaCrypt 4.0 with the same extension as the original file. ========== = 0.0.84 = ========== - Fixed and issue when PublicKeyBC in exx files is shorter than 64 characters ========== = 0.0.83 = ========== - Fixed a bug when all files were skipped if decryption of xxx, ttt, micro, mp3 files was selected and ... |
 |
6,256 | Nov 13, 2019 BloodDolly  |
|
| Showing rows 1 to 6 of 6 | Showing Page 1 of 1 | 1 |
OlderGeeks.com Copyright (c) 2025