
|
Whoa! Slow down there, Speedy.
Kindly read this and then continue to download below.
Like seeing no ads? No misleading/fake download buttons?
We like it too! This site has been kept alive for 15 years
because of people just like you who download and donate.
No one is stopping you from downloading without donating
but the site runs on the "Honor System". If your momma
raised you to be honorable, make a donation and download
'til ya turn blue. Make your momma proud!
Thank you! -Randy & Deanna (The Older Geeks)
Missouri Ozarks, USA
Monthly operating costs = $750
Donations cover operating costs first
then are set aside for future upgrades and/or
handed-over to Deanna for new shoes.
Or
Or
Send a check payable to Home Computer Repair LLC, 208 E. Water St. Mount Vernon, MO 65712
|
Recent Super Donors ($50+)
Thanks, Mark
Thanks, Michael
Thanks, Russell
Thanks, Home Business Services Inc
Recent Donors
Thanks, Stephen
Thanks, Suzanne
Thanks, Art
Thanks, Paul
Thanks, Graham
Thanks, Ruschmann & Scherling LLC
Thanks, Antonia
Thanks, Michael
Thanks, Douglas
Thanks, Tery
|











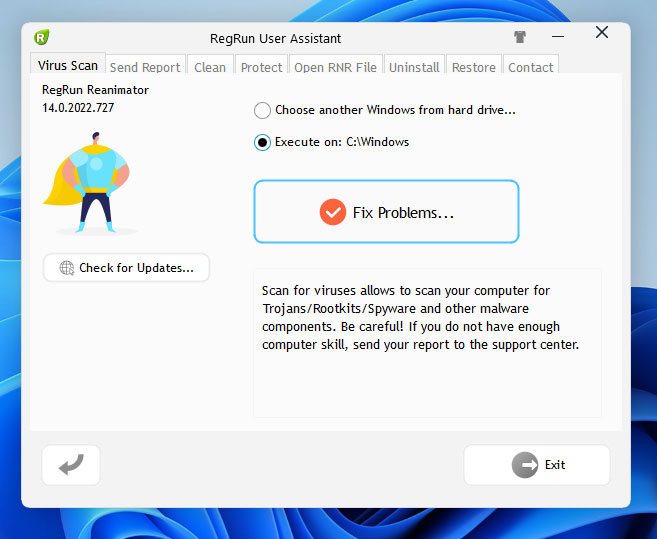
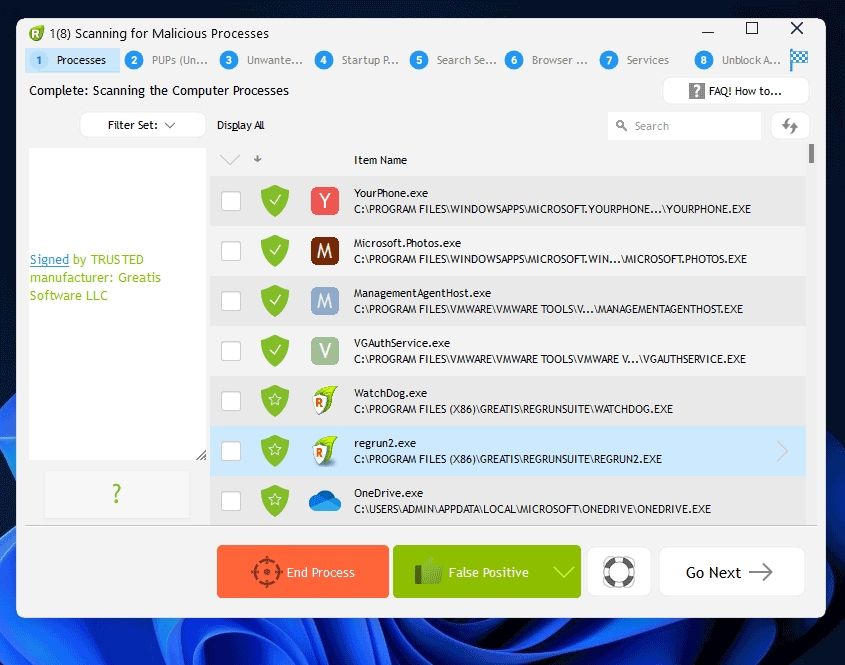
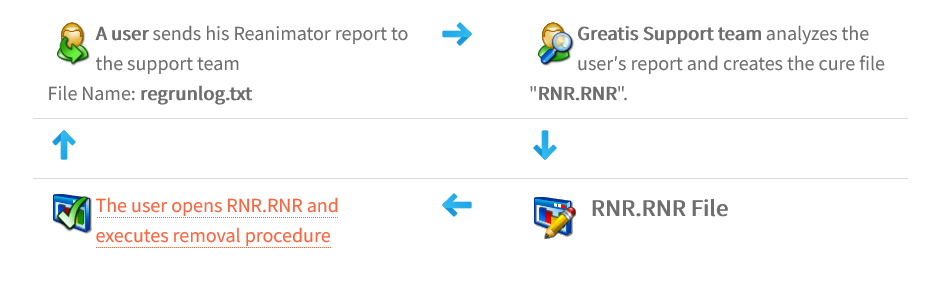
 , out of 54 Votes.
, out of 54 Votes.
